Vulnerability Intelligence
What is Vulnerability Intelligence?
Vulnerability intelligence helps organizations identify, monitor, and mitigate vulnerabilities that could lead to a potential attack.
Securin’s Vulnerability Intelligence (VI) provides your security team with an entire spectrum of vulnerability information through an intuitive dashboard or integrated APIs. Powered by 29+ authoritative intelligence feeds and over 1,000 sources, Securin VI’s artificial intelligence (AI) and machine learning (ML) models continuously measure a vulnerability’s risk by dynamically tracking its trajectory from exploitation to weaponization.
Comprehensive Threat Intelligence Database
Attackers are always a step ahead because researchers cannot understand the true risk posed by a vulnerability. To do that, a researcher needs to access multiple data sources and combine multiple factors to assess its risk.
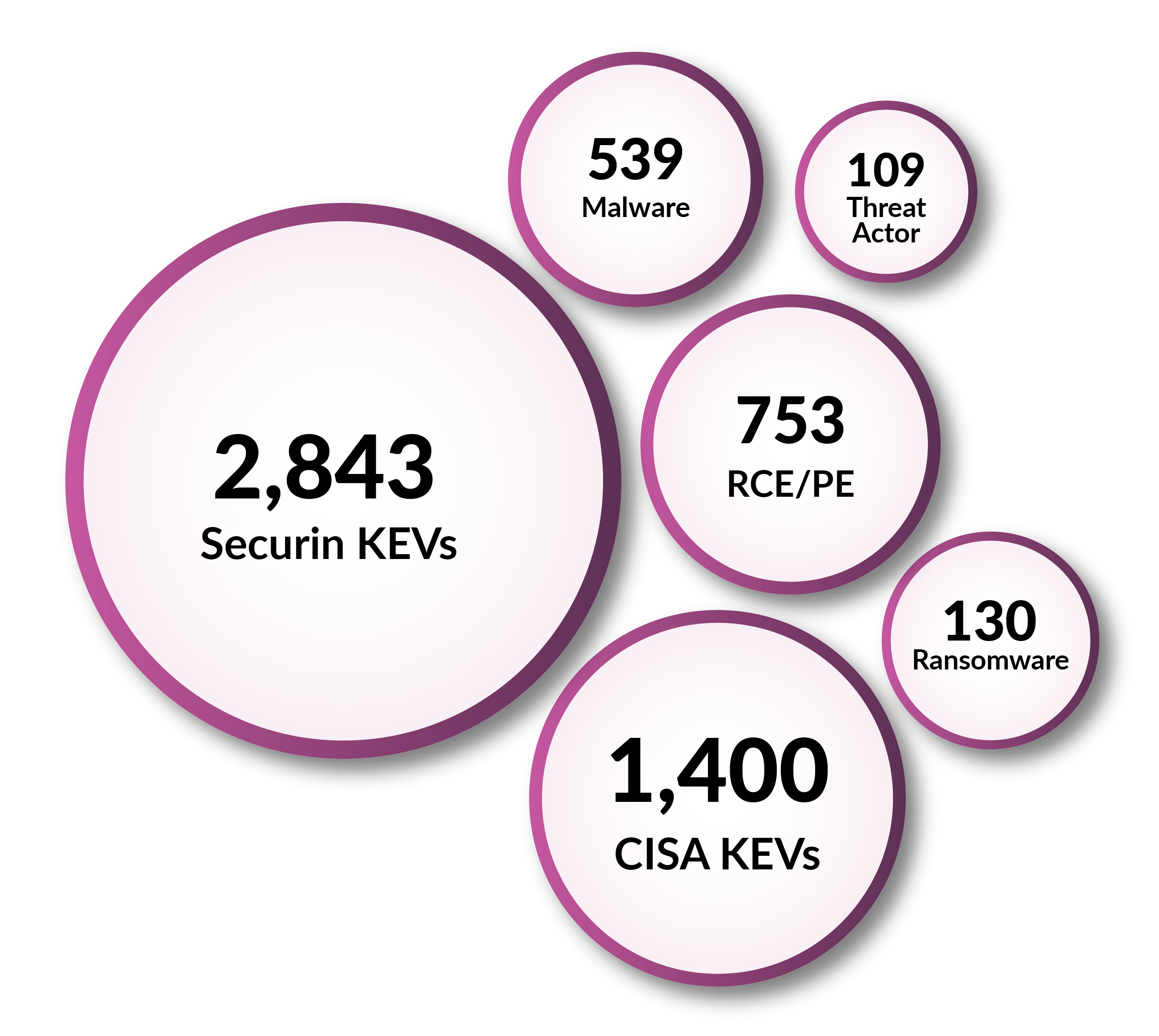
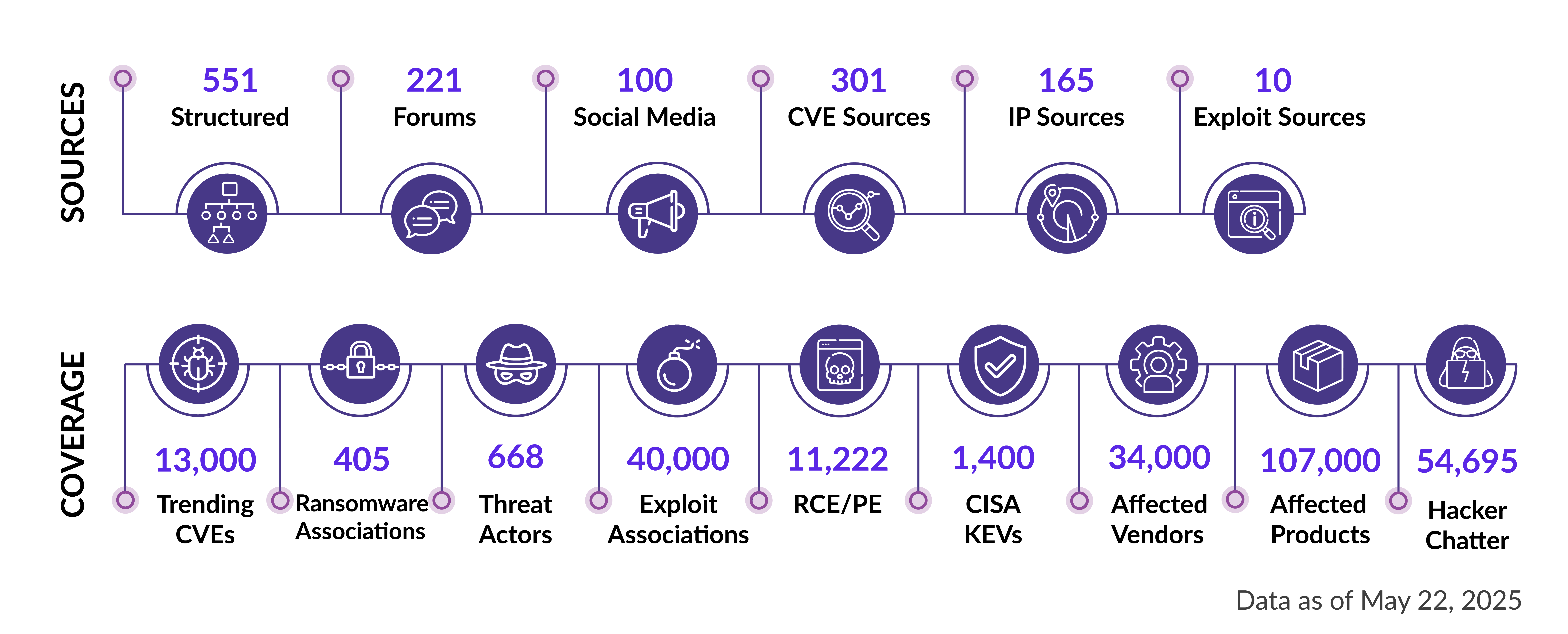
Securin’s VI provides unparalleled coverage, with data being collected continuously from over 1,000 different sources.
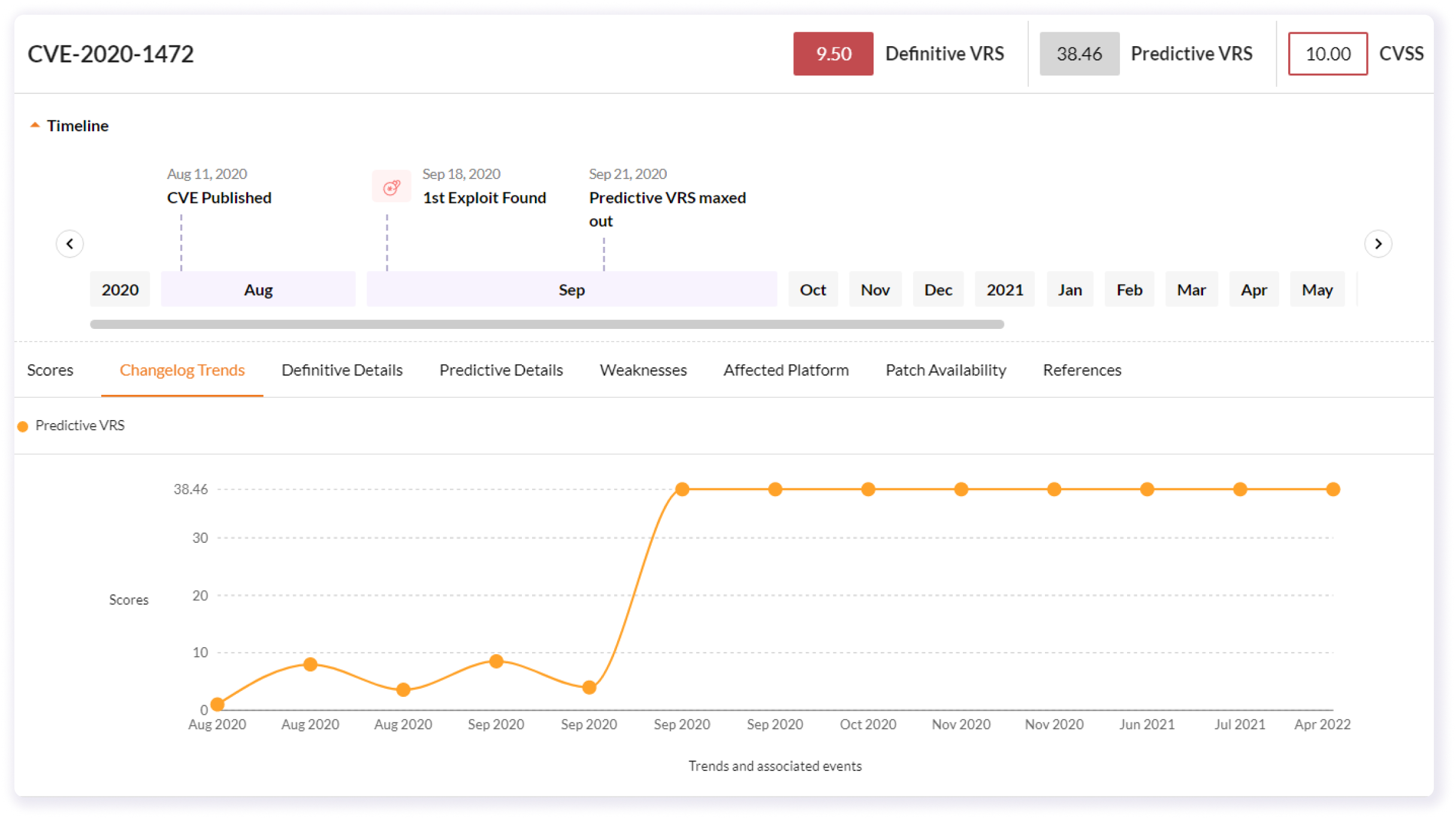
Securin Vulnerability Intelligence Features, Widgets, & Capabilities
| RCE/PE Vulnerabilities | Categorize vulnerabilities by exploit type Remote Code Execution (RCE), Privilege Escalation (PE), Web App, Denial of Service (DoS) etc. |
| Trending | Exclusive filters for vulnerabilities that are being actively searched in the deep and dark web and hacker networks, updated multiple times per day |
| Ransomware and Threat Groups | A living list of vulnerabilities with conclusive associations to ransomware operators and advanced persistent threat groups. |
| Exploits | Exploits and their classifications and aliases with a timeline of when they became publicly available. |
| Temporal Scores | Temporal scores for each vulnerability to accurately measure its risk based on the exploitability, report confidence, and remediation level. |
| CVSS V2 to V3 Mapping | Mapping old vulnerabilities (discovered before 2015) with V2 scoring to CVSS V3 severity rating to provide uniformity in understanding the risk level of a vulnerability. |
| Advisories and Warnings | Securin experts curate and distribute an exclusive filtered view of vulnerabilities that are evolving via our ThreatWatch feature. |
| Zero Days | An exclusive dashboard that lists newly discovered zero days (and also those without CVE numbers) with all pertinent details, severity scores, and predictive insights. |
| Predictive Intel | Predictive scores for vulnerabilities based on their exploitability, evidence from hacker chats, deep and dark web forums, security community discussion in social media and more. |
| Affected Vendors and Products | Common Platform Enumeration (CPE) data of vendors and products affected by vulnerabilities. Know the code base used in each product through the Software Bill of Materials (SBOM) and pivot fast to stay safe from supply chain attacks. |
| Vulnerability Data by Sectors, Product Categorization, EOL | View vulnerabilities that exist in specific product categories such as VPNs, databases, data storage, gateways, online conference tools, web proxies, etc. Find vulnerabilities that pose threats to certain industries or sectors (health care, SLED, energy, critical infrastructure, etc.). |
| End of Life (EOL) | Filter products that have reached the End-of-Life (EOL) life cycle to manage and stay on top of your asset management. |
| CISA KEVs | Threat context for CISA's Known Exploited Vulnerabilities (KEVs), including weaponization lifecycle, updated as they evolve. |
Prioritize Vulnerabilities Through Threat Context
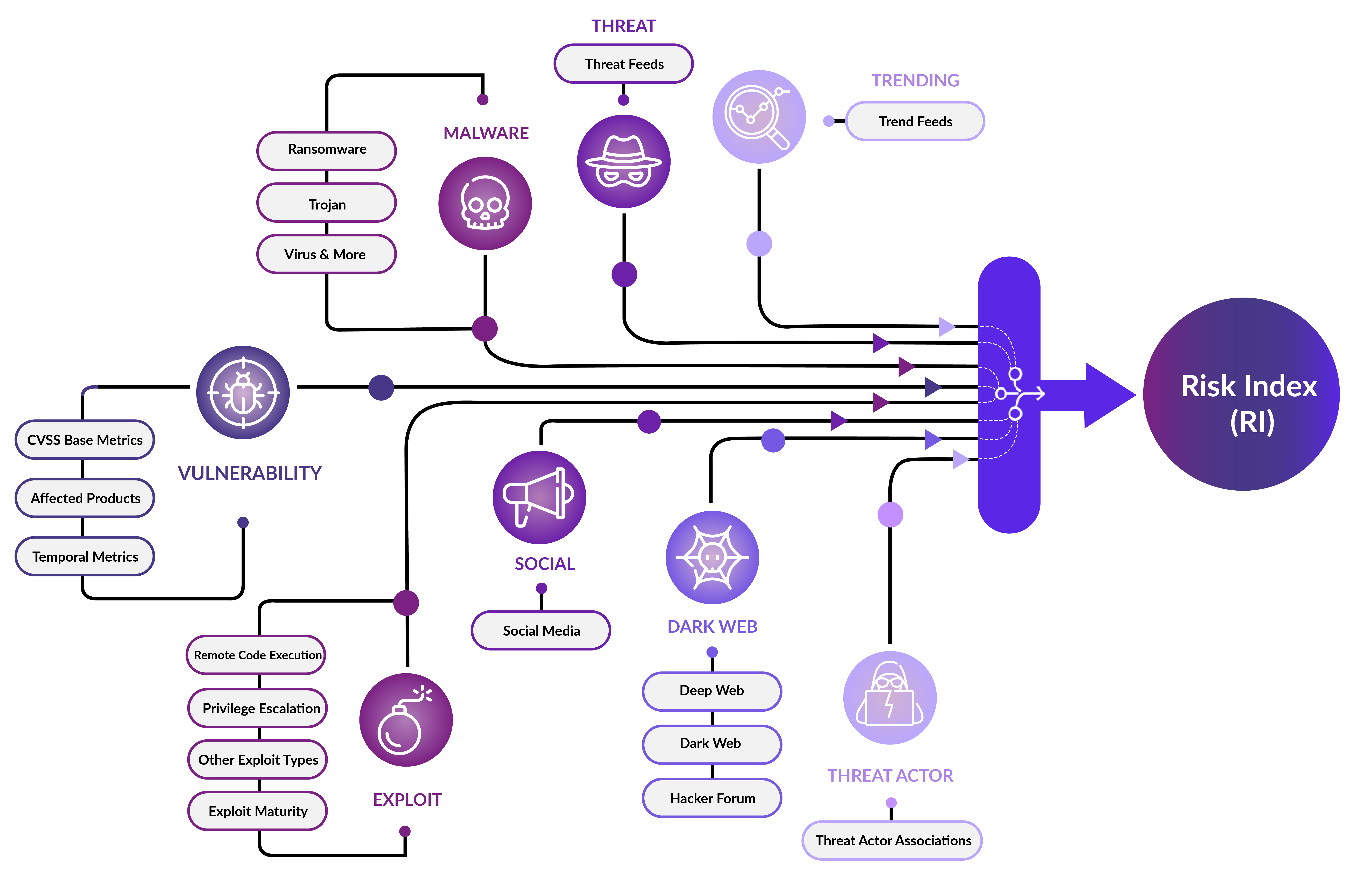
Securin VI’s contextual risk data provides security teams with accurate intel and multiple perspectives as it dynamically tracks a vulnerability’s real-world risks. Using Securin’s VI, security teams can assess the true risk of a vulnerability and prioritize it for remediation after understanding its threat context.
Securin’s VI also provides researchers access to MITRE ATT&CK techniques, tactics, and processes (TTPs), empowering them to assess how a vulnerability could be exploited in a real-world attack. Researchers and IT teams can use this context to prioritize vulnerabilities for remediation. Securin VI’s continuous research on MITRE tactics and techniques enables us to map all ransomware CVEs to their TTPs and red-flag those vulnerabilities with the complete kill chain. The VI platform also provides a handy sidekick feature to identify vulnerabilities within their network that can be chained together to mount crippling attacks.
Risk Index (RI)
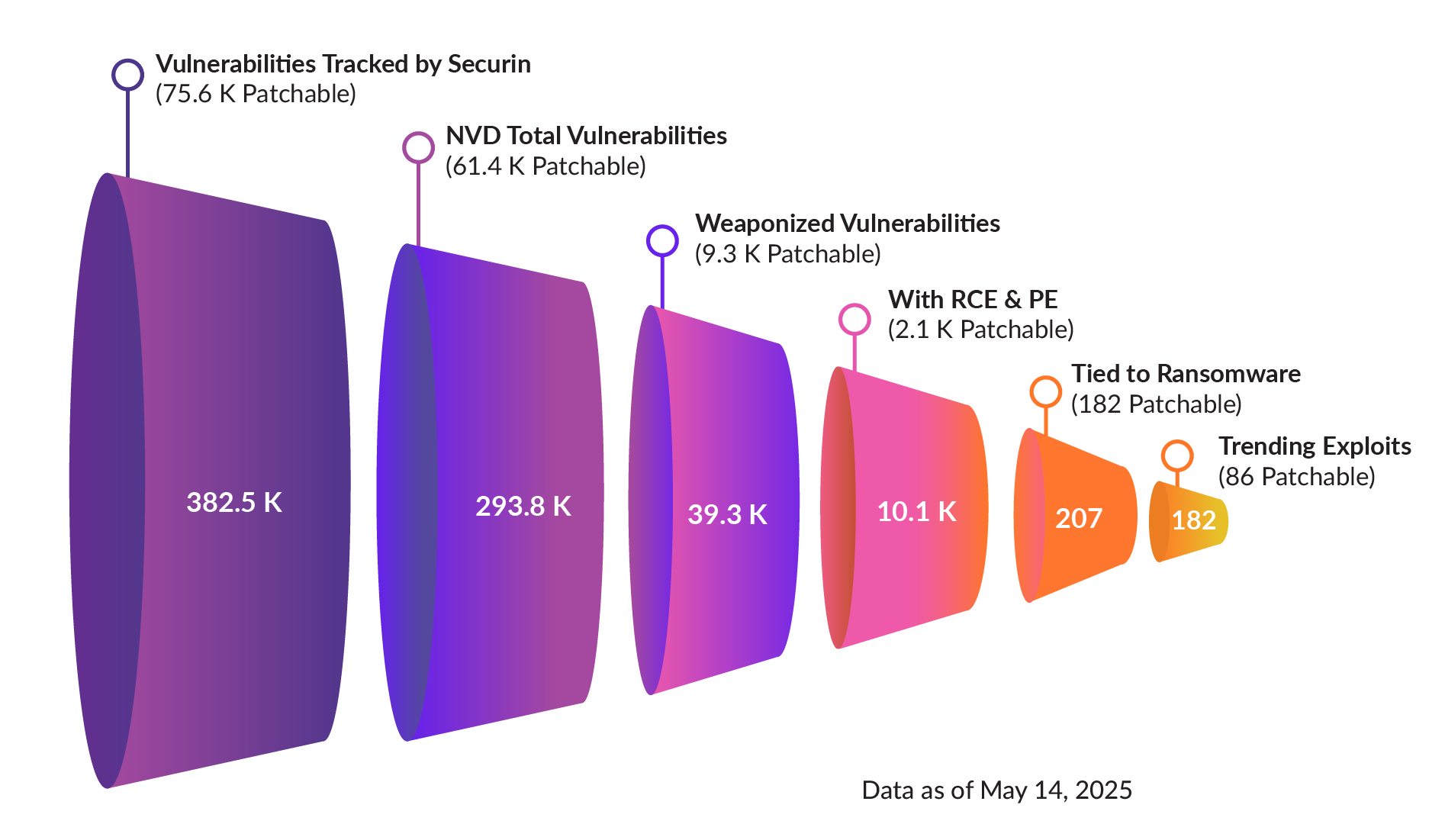
The Common Vulnerability Scoring System (CVSS) used for Common Vulnerabilities and Exposures (CVE) does not give a true measure of the risk posed by vulnerabilities. For example, we found that 28% of ransomware vulnerabilities do not have CVSS V3 scores, and 62% of them are rated less than 8 in CVSS V2 scores despite their association with ransomware. Organizations that solely depend on the CVSS are at a disadvantage, as security teams will not prioritize these vulnerabilities for remediation over those with higher scores.
To know the real risk of each vulnerability, Securin’s Vulnerability Intelligence applies a Risk Index (RI), using an accurate threat assessment model that computes the risk posed by each vulnerability based on its exploitability, threat associations, and potential impact. Powered by artificial intelligence (AI) and machine learning (ML), the RI attributes automated risk scores (0 to 10) considering the maturity, exploit impact, trends, and associated threats to present security teams with an accurate measure of risk that would help them prioritize dangerous vulnerabilities for remediation.
Vulnerability Intelligence Benefits
Continually Updated Insights
Our full-stack scanning identifies & prioritizes exposures based on weaponization, criticality, & threat context.

Accurate Threat Context
Prioritize high risk vulnerabilities based on accurate threat context
API Integration
Integrate with platforms and maximize investments in existing security tools
Resources

Sep 25, 2023
No organization is exempt from vulnerability management, but are you unwittingly committing the seven deadly sins of this vital cybersecurity practice?

Aug 28, 2023
Discover the five signs that indicate your business may be at risk and needs cybersecurity managed services immediately.

Nov 15, 2023
Explore our comprehensive guide to password protection and delve into the cyber threat landscape, covering sophisticated attacks like phishing and brute force attempts, as well as nuanced techniques like keylogging.
Ready to Level Up?
Now that you’re ready to accelerate your security program, let’s put you in touch with one of our experts!