Attack Surface Management
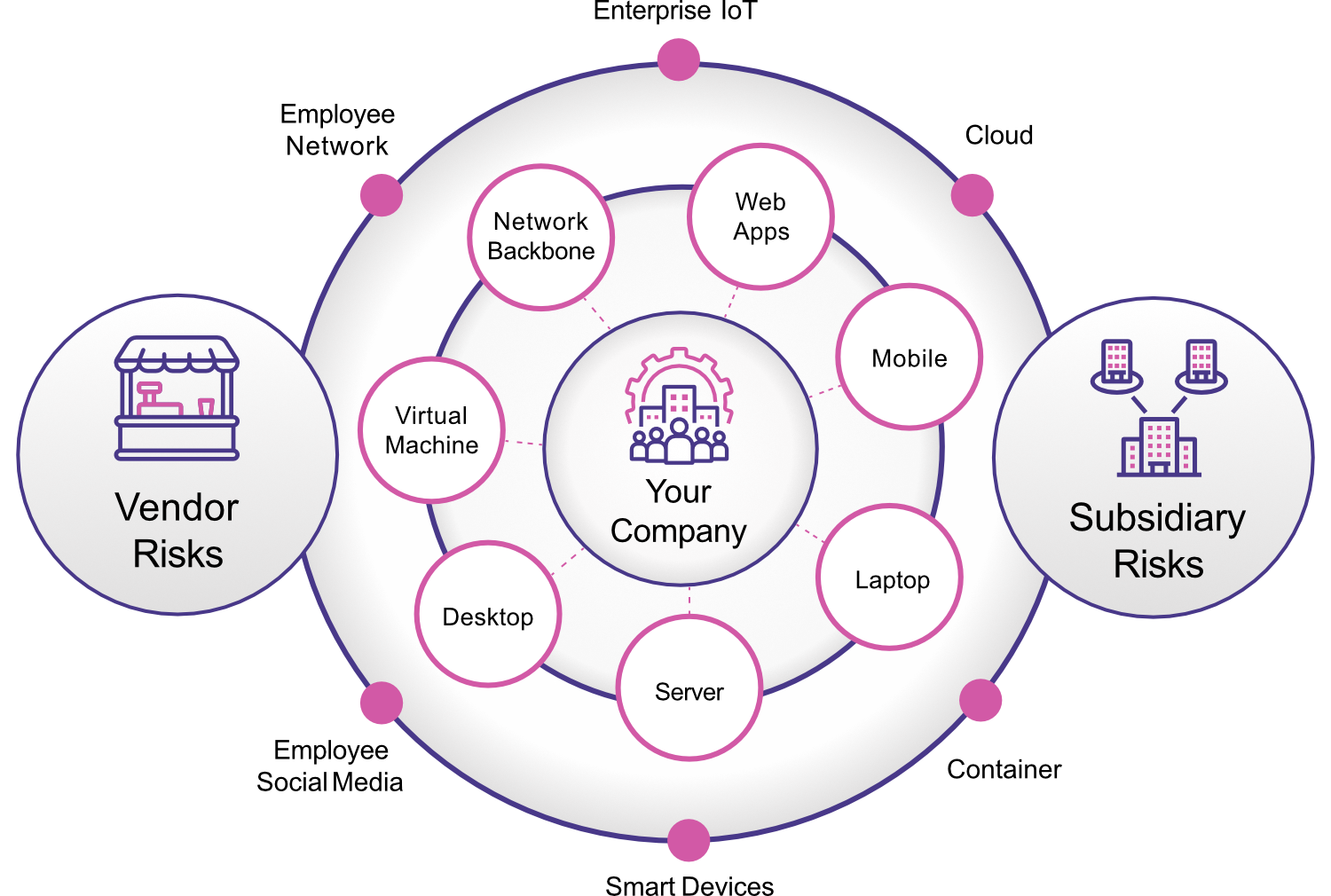
What is an Attack Surface?
It is the sum of both known and unknown assets that are visible to the internet. Typically, where an unauthorized user can attempt to enter or extract data from your environment.
Our Attack Surface Management (ASM) provides you a view of your true attack surface! We enable you to proactively defend against evolving threats and insidious cyber-attacks. Our effective combination of automation and human intelligence provides your organization with a holistic solution to mitigate dangerous exposures within your digital environment.
Securin's ASM Platform
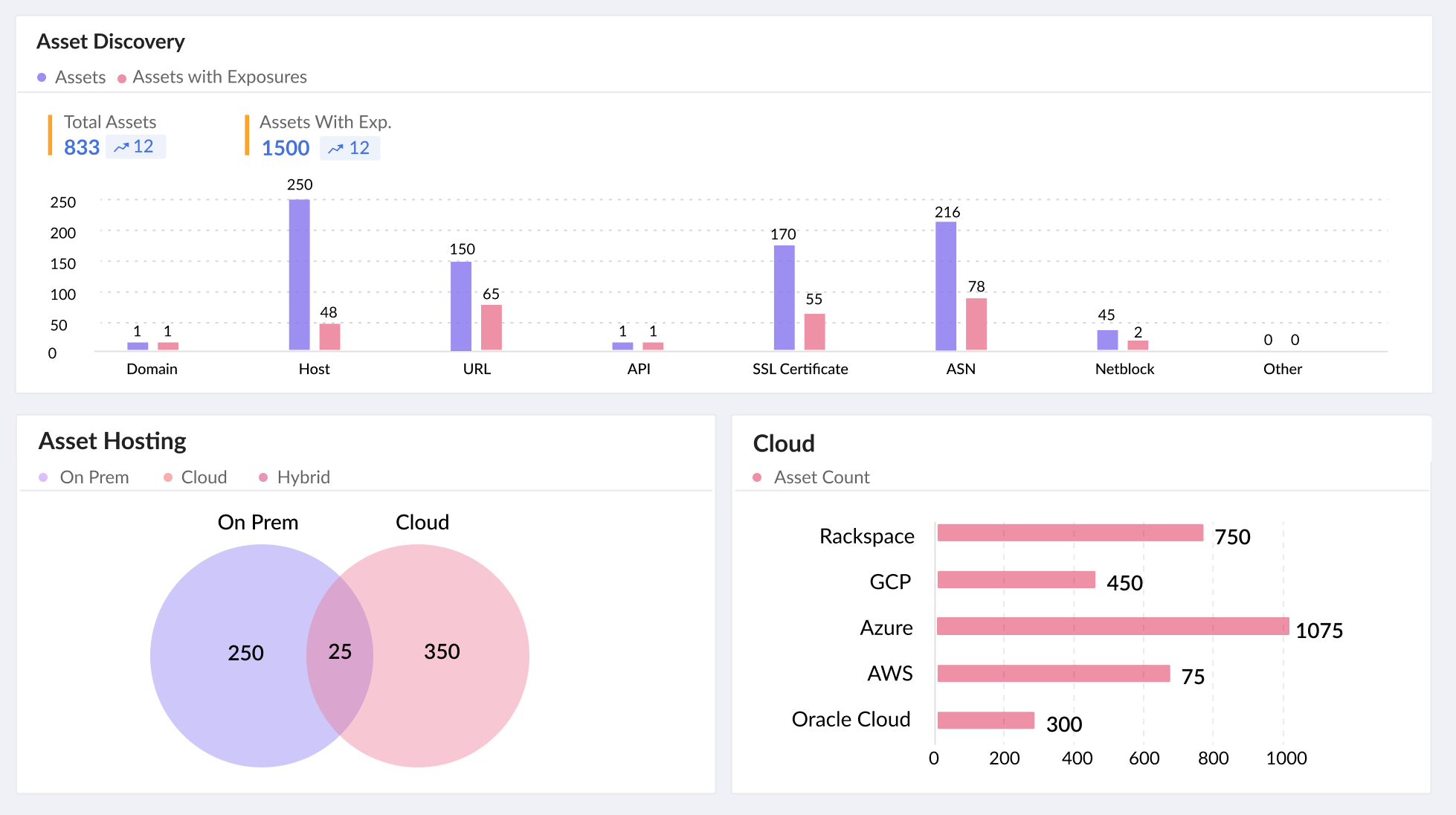
ASM Work?
Discover
Discover All Digital Assets
Discover all your assets: internal, external, cloud, containers, APIs, SaaS, and applications (web and mobile). Gain visibility into your organization's known and unknown assets. Securin's platform continuously tracks changing assets and provides in-depth visibility into your attack surface.
Analyze
Classify & Prioritize Exposures
Meticulously classify and fingerprint assets to prioritize exposures based on severity and asset criticality for your organization. Securin automatically triages and tags all assets using a proprietary algorithm. Our platform analyzes exposure based on asset type, context, and criticality. Providing your IT team with actionable intelligence.
Mitigate
Identify Exposures for Remediation
Securin’s context awareness also extends to exposure mitigation by identifying suitable patches for your vulnerabilities. Our platform helps reduce the attack window by highlighting the unknown unknowns and maintains efficient remediation cycles.
Prioritize
Assign Asset Criticality
Asset criticality is assigned based on misconfigurations, vulnerable third-party software, and emerging cyberattack trends. Each exposure is analyzed and uniquely prioritized based on the severity and context in which the asset operates. Securin's platform also allows your organization to set asset criticality, thus delivering unique contextual exposure prioritization.
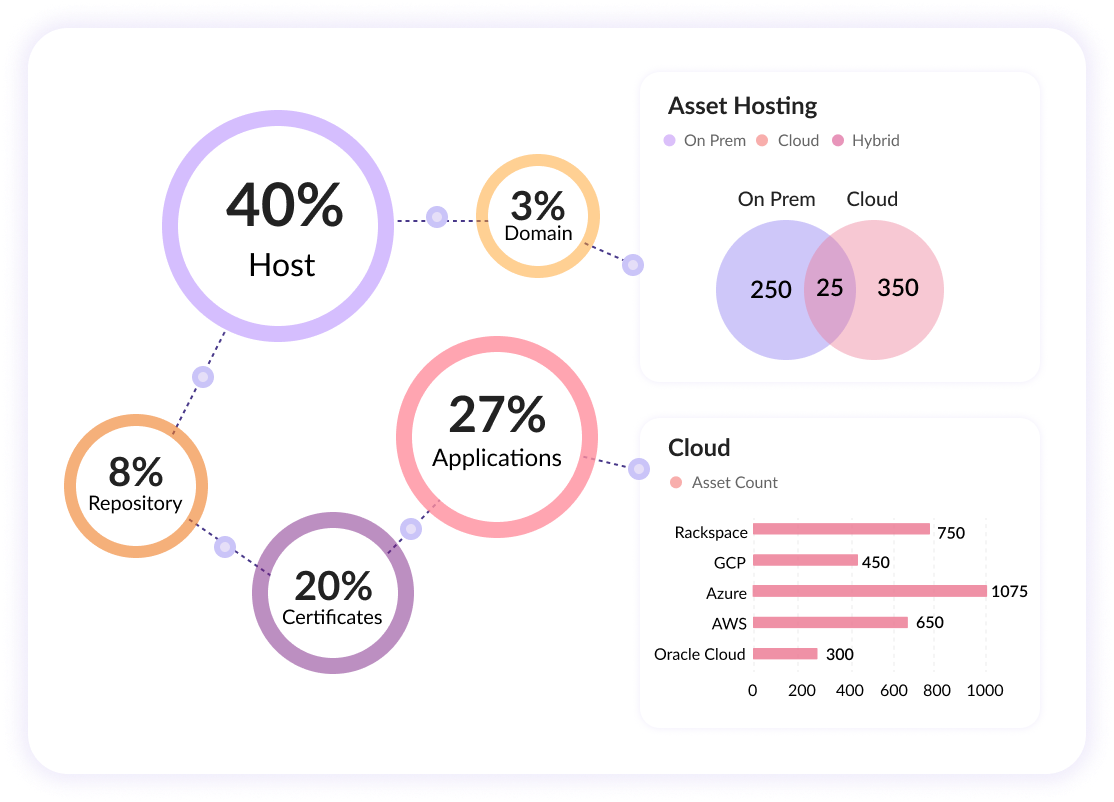
Continuous Attack Surface Discovery
Securin’s context awareness also extends to exposure mitigation by identifying suitable patches for your vulnerabilities. Our platform helps reduce the attack window by highlighting the unknown unknowns and maintains efficient remediation cycles.
Contextual Exposure Prioritization
Securin ASM brings appropriate threat context to exposures, prioritizes assets based on criticality to the business, and helps your team spend their valuable time on remediation.
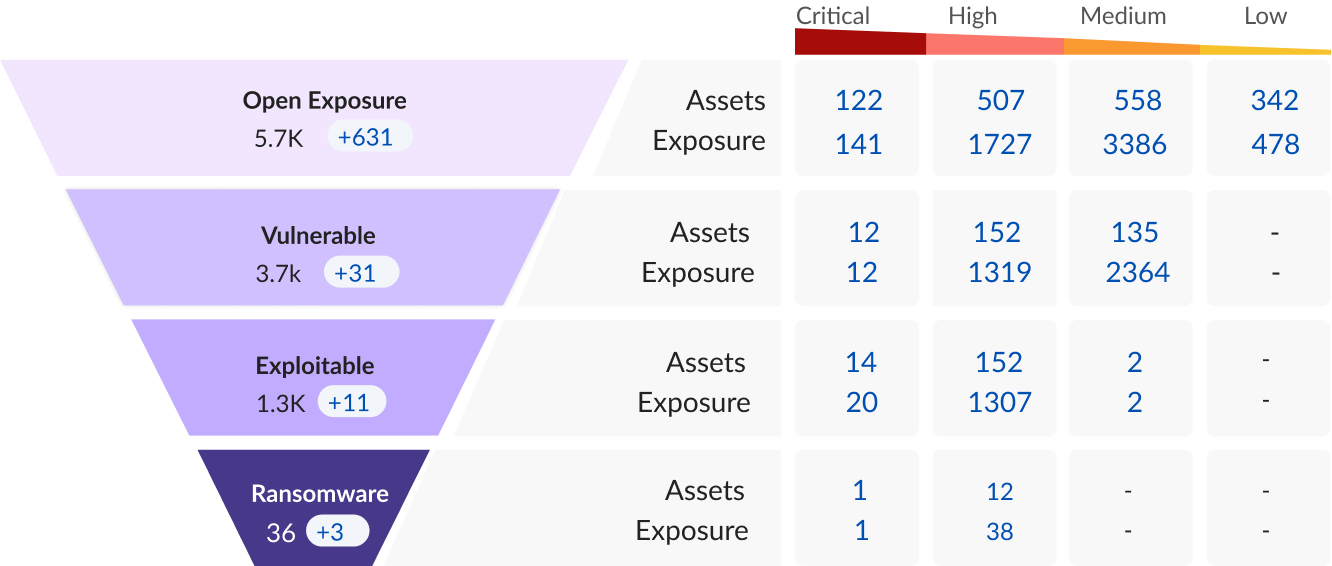
Integrating Securin ASM
The Securin ASM platform can integrate with data from other scanners, connect to ticketing systems, and even cloud services. Post integration, you can see all data, enriched with Securin Contextual Vulnerability Intel, in a single interface. You no longer need to look up multiple sources to discover, analyze, prioritize and mitigate the exposures that exist across all your assets.
ASM Benefits
Proactive Security
Proactively scan your known & unknown assets for exposures. Prioritize those exposures based on asset criticality & severity.
Accurate Threat Context
Securin’s threat hunting expertise & vulnerability intelligence provides accurate threat context on exposures for better remediation.
Constantly Reduce Risk
Constantly drive down the risk of cyber attacks by proactively mitigating blindspots, unpatched instances, & exposures.
Resources

Dec 18, 2024
Discover the pivotal role of multi-factor authentication in defending against sophisticated cyber threats and safeguarding digital assets.

Aug 28, 2023
Discover the five signs that indicate your business may be at risk and needs cybersecurity managed services immediately.

Aug 14, 2023
AI is used by cybercriminals to launch sophisticated attacks. However, organizations can leverage AI through cybersecurity managed services to stay safe.
Ready to Level Up?
Now that you’re ready to accelerate your security program, let’s put you in touch with one of our experts!

