Penetration Testing as a Service
What is Penetration Testing?
It is a security test performed by security experts to attack your cyber defenses and analyze any exploitable vulnerabilities.
Learn how adversaries can exploit your vulnerabilities and weaknesses to breach critical systems and sensitive data. Our penetration testing (pentesting) simulates a real-world attack on your digital assets. We adopt a hacker’s perspective to detect and exploit vulnerabilities in your environment to determine if we can move laterally and compromise your entire IT infrastructure and applications.
Test Your Resilience
With Securin penetration testing discover and identify vulnerabilities missed by scanners and exploited by hackers. Learn how vulnerable your digital assets are against a real-world attack. Our testers conduct a real-world assault using tactics, techniques, and procedures used by hackers to compromise systems and breach networks. Our penetration testers follow the MITRE ATT&CK framework, NIST 800-115, and TTPs used by hackers to exploit and compromise digital environments.
Close Security Gaps
Understand the scale and scope of your cybersecurity tools as our experts penetrate through your defenses. We help identify and close your security gaps and secure your attack surface from evolving threats. Learn how hackers use advanced tactics to exploit vulnerabilities that exist in your environment and understand how to safeguard sensitive assets and data.
Meet Compliance Requirements
Test your compliance with industry standards such as ISO 27001, HIPAA, GRC, PCI-DSS, and SOC 2. Securin penetration testers conduct a real-world attack on your existing security controls to test their efficacy and identify exploitable vulnerabilities. Leverage our expertise to become compliant with mandated industry-specific regulations related to healthcare, finance, and technical industries.
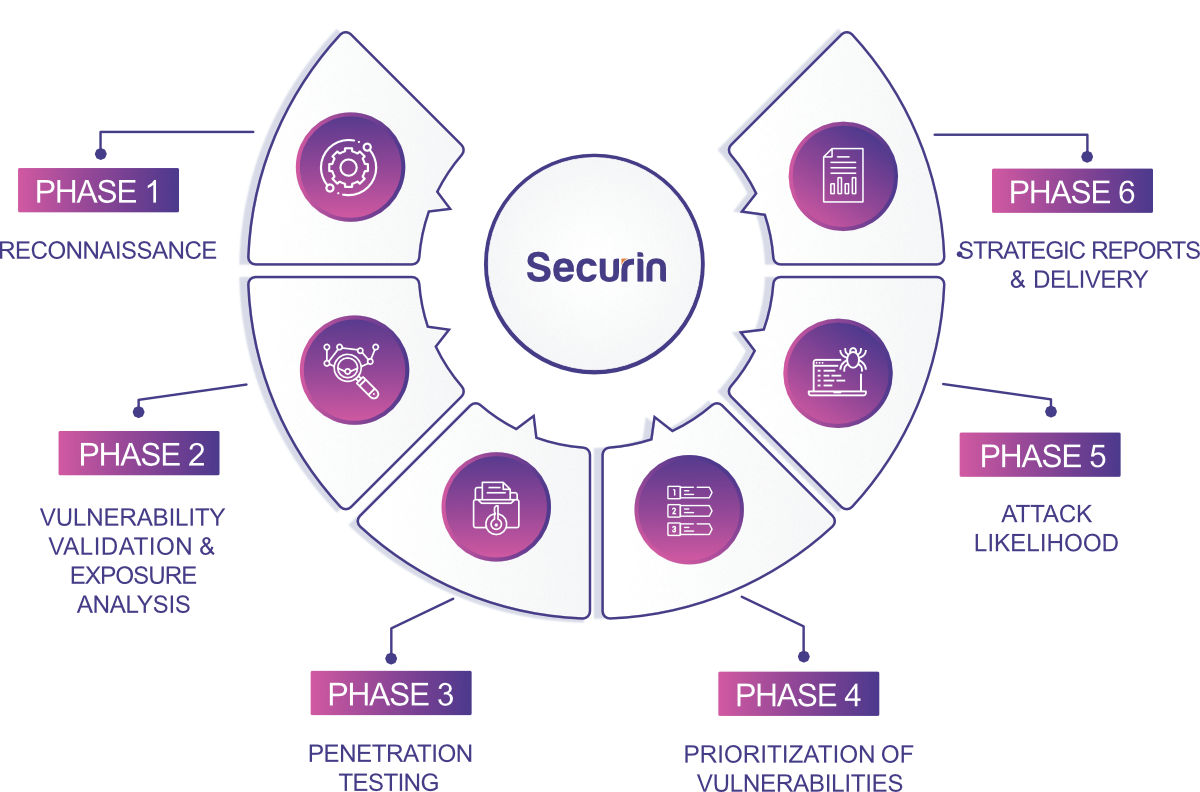
Penetration Testing as a Service Methodology
Penetration Testing Benefits

Know Your Security Gaps
Securin’s penetration testers adopt a hacker’s perspective to target blind spots, critical weaknesses, misconfigurations, and gaps in patching.

Validated Results for Faster Remediation
Actionable and prescriptive security remediations begin with a validated list of vulnerabilities. These recommendations enable you to stay safe from attackers.

Synchronized Results
Synchronized delivery of results allows you to view identified vulnerabilities within hours of commencing the assessment for rapid remediation.
Network Security Services
Network Penetration Testing
Securin’s Network Penetration Testing Program helps organizations stay ahead of attackers by providing deep insights about vulnerabilities that exist within their network. Build a resilient network that can defend assets from Advanced Persistent Threat (APT) groups, evolving attacker behavior, and trending threats.
Internal Network Penetration Testing
Securin internal network penetration testing focuses on testing infrastructure commonly deployed in data centers and office networks. For example Windows domains, network configuration interfaces, printers, and virtualization consoles. The testing simulates scenarios where attackers have gained a foothold on a network through phishing, browser compromise, VPN compromise.
External Network Penetration Testing
Securin’s External Penetration Testing Program provides organizations with an accurate picture of the risk associated with their externally facing assets. Our penetration testers test the security controls of external assets and help determine how vulnerable they are to attackers.
Application Security Services
Web Application Penetration Testing
Securin’s Network Penetration Testing Program helps organizations stay ahead of attackers by providing deep insights about vulnerabilities that exist within their network. Build a resilient network that can defend assets from Advanced Persistent Threat (APT) groups, evolving attacker behavior, and trending threats.
SaaS Penetration Testing
Securin’s SaaS penetration testing is an evaluation of a SaaS platform’s web application components, infrastructure, API, and source code. Securin uses a distinct and customized approach based on the target SaaS platform’s development components, features, and business functionality.
Mobile Application Penetration Testing
A mobile application penetration test is a point-in-time security controls review of an application or application components. The two key testing sections of this assessment are static analysis and dynamic analysis. These phases allow Securin to conduct a detailed security examination of the target mobile application components while gathering information to rank and prioritize threats.
API Penetration Testing
Securin’s API penetration test validates the security of your organizational methods and corresponding data. Our testing methodology uses standardized processes to ensure consistency and ensure your API workflow is secure. We evaluate all applications based on OWASP API Top 10 and CWE Top 25 programming errors.
Resources

Aug 28, 2023
Discover the five signs that indicate your business may be at risk and needs cybersecurity managed services immediately.

Aug 14, 2023
AI is used by cybercriminals to launch sophisticated attacks. However, organizations can leverage AI through cybersecurity managed services to stay safe.

Jan 10, 2022
Organizations have been increasingly relying on cloud services from Azure since Microsoft provides native support. As a result, CSW pentesters have been researching various attack
Ready to Level Up?
Now that you’re ready to accelerate your security program, let’s put you in touch with one of our experts!