The D-link router DIR-885L-MFC 1.15b02, v1.21b05 is vulnerable to credentials disclosure in telnet service through decompilation of firmware, that allows an unauthenticated attacker to gain access to the firmware and to extract sensitive data.
Securin Zero-Days
CVE-2020-29323 – D-Link Router DIR-885L-MFC Telnet Hardcoded Credentials
Severity:High
Vendor
D-Link
Affected Product
D-Link Router DIR-885L-MFC
CVE
CVE-2020-29323
Securin ID
2020-CSW-08-1048
Status
Fixed
Date
August 17, 2021
Description
Proof of Concept (POC):
Issues: The telnet hardcoded default credentials are the vulnerable elements in the firmware of DIR-868L.
Step 1: Extract the firmware
Step 2: Run the command cat etc/init0.d/S80telnetd.sh to get the username and the location of the variable used for storing the password.
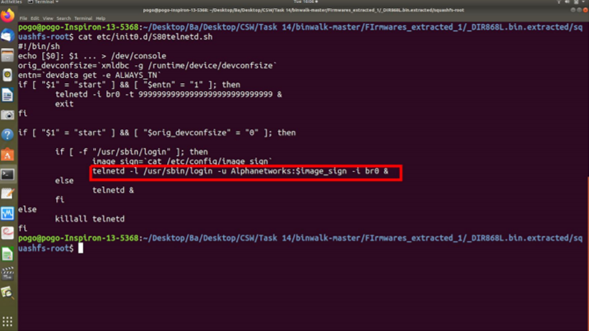
Figure 1: Clear text username as shown in screenshots
Step 3: Run the command cat etc/config/image_sign to get the password
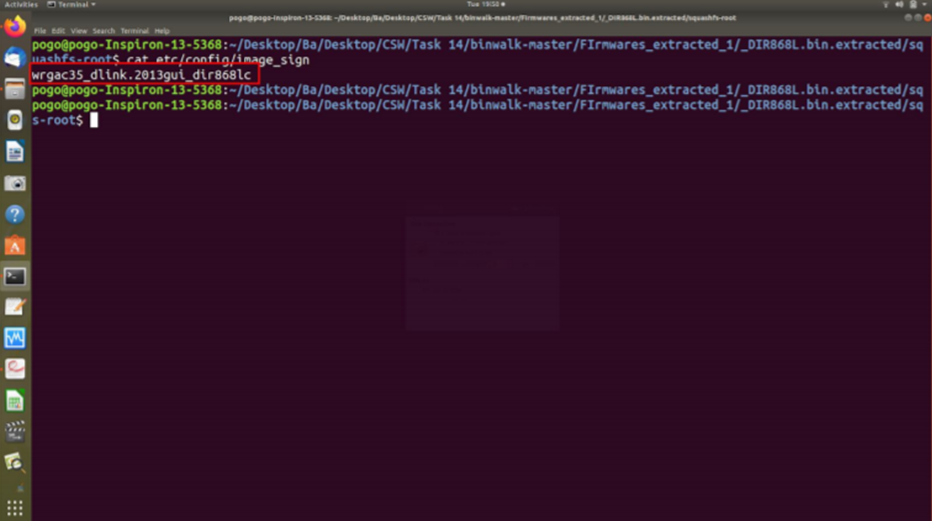
Figure 2: Clear text password as shown in screenshots
Impact
A successful exploit could allow the attacker to gain access to the firmware and to extract sensitive data.
Remediations
D-Link released a support announcement in response to the recommendations provided by the CSW team for these D-Link products – https://supportannouncement.us.dlink.com/announcement/publication.aspx?name=SAP10189
Timeline
Aug 17, 2020: Discovered in our research lab
Aug 18, 2020: Vulnerability reported to vendor and vendor acknowledged the vulnerability
Aug 20, 2020: Vendor responded saying “elevated to D-Link Corporation”.
Aug 26, 2020: Follow up
Aug 28, 2020: Vendor responded saying “should have an update in next few Days”
Sep 4, 2020: Follow up
Sep 7,2020: Vendor responded saying need more time to review and response from R&D
Sep 10, 2020: Vendor responded with a support announcement.