An issue was discovered on HTTP post request in WSO2 API Manager 2.6.0 in the ‘implement phase’ of the API Publisher. A stored cross-site script (XSS) vulnerability allows an attacker to inject malicious code into the application.
Securin Zero-Days
CVE-2019-20441 – Stored Cross-Site Scripting in WSO2
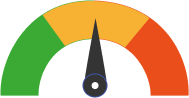
Severity:Medium
Vendor
WSO2
Affected Product
WSO2 API Manager
CVE
CVE-2019-20441
Securin ID
2019-CSW-01-1022
Status
Fixed
Date
July 6, 2019
Description
Proof of Concept (POC):
The following vulnerability was tested on the WSO2 API Manager version 2.6.0 Product.
Issue 01: Stored Cross-Site Scripting.
.png)
Figure 01: Design an API with valid values in the required fields of the page.
.png)
Figure 02: Click on “Next Implement” after completing the forms with valid information.
.png)
Figure 03: Valid HTTP Request captured in the proxy with filled information.
.png)
Figure 04: ‘Context’ variable is added with XSS Payload, “><script>alert(document.cookie)</script>.
.png)
Figure 05: Submitted the API details to the server with XSS payload.
.png)
Figure 06: XSS Payload gets stored and reflects whenever the user views the publisher page.
.png)
Figure 07: Stored XSS payload in the source code.
Impact
Through an XSS attack, the attacker can make the browser redirect to a malicious website. Unauthorized actions such as changing the UI of the web page, retrieving information from the browser are possible. But since all session-related sensitive cookies are set with httpOnly flat and protected, session hijacking or mounting a similar attack would not be possible.
Remediations
Download the relevant patch based on the product version.
| Code | Product | Version | Patch |
| AM | WSO2 API Manager | 2.6.0 | WSO2-CARBON-PATCH-4.4.0-5185 |
Timeline
Jul 05, 2019: Discovered CVE-2019-20441 in WSO2 API Manager v2.6.0.
Jul 06, 2019: Reported to the intigriti platform.
Jul 23, 2019: Closed the issue in the intigriti platform as it was “out of scope.”
Jul 26, 2019: Reported to WSO2.
Jul 26, 2019: WS02 acknowledged the report.
Aug 13, 2019: Fixing began in all affected versions.
Nov 04, 2019: Public and customer announcement by the vendor about the vulnerability