A reflected cross-site scripting vulnerability identified on OcPortal CMS 9.0.20. An input variable vulnerable to XSS is ‘field_name’ in the CF_EMOTICON_CELL.tplfile.\ocportal\themes\default\templates\OCF_EMOTICON_CELL.tpl.
Securin Zero-Days
CVE-2015-9549 – Reflected Cross-Site Scripting in OcPortal CMS
Severity:Medium
Vendor
OcPortal
Affected Product
OcPortal
CVE
CVE-2015-9549
Securin ID
2015-CSW-10-1013
Status
Fixed
Date
November 6, 2015
Description
Proof of Concept (POC):
As per the documentation of the Ocportal, a value in a template that is not meant to contain HTML is marked as an escaped value ({VALUE*}). This means that ‘HTML entities’ are put in replacement of HTML control characters.
.png)
Here the VALUE that is marked with * symbol will be filtered with the XSS filter, and it will be sanitized before displaying it to the user, but they forgot to mark FIELD_NAME in OCF_EMOTICON_CELL.tplfile.\ocportal\themes\default\templates\OCF_EMOTICON_CELL.tpl
.png)
The View_all link beside the emoticons in the following screen is having this FIELD_NAME variable.
.png)
The View_all link is sending the following GET request to the server
.png)
The following is the source code of emoticons.php file\ocportal\data\emotions.php
.png)
The following is the code related to emoticons_script function in misc_scritps.php file\ocportal\sources\misc_scripts.php
\ocportal\sources\misc_scripts.php
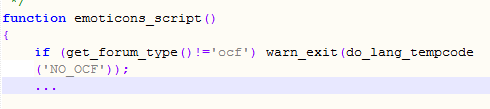
Code that is loading the template file with the user-entered input \ocportal\sources\misc_scripts.php
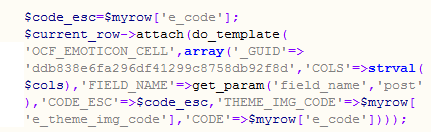
This code is reading the GET request parameter field_name and displaying it back to the user without filtering because of the variable is not marked with * symbol. Obviously, it will not go for any filtration.
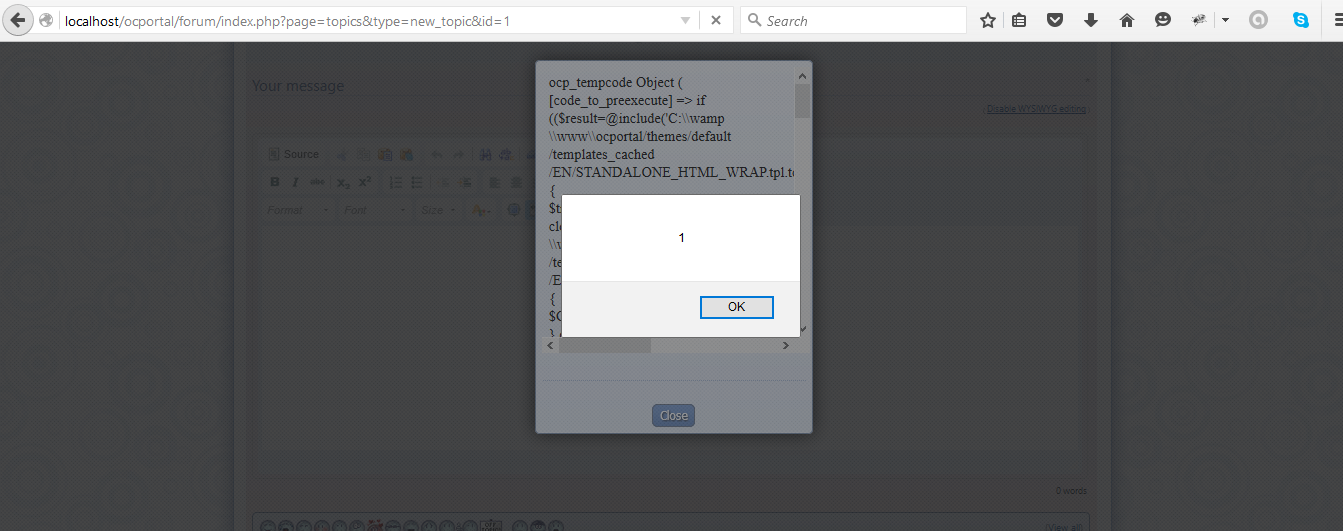
GET request to emoticons.php with script vector as the value of field_name
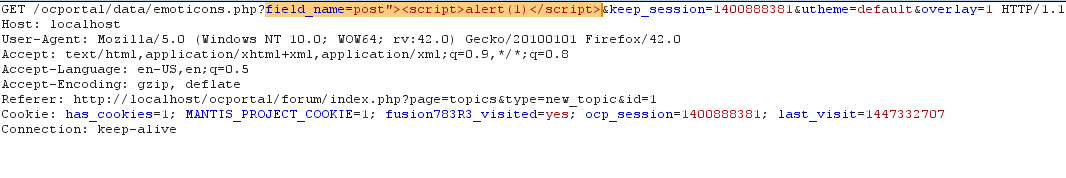
And the inserted payload is reflecting back to the user, as shown in the following screen.
Impact
A reflected cross-site script (XSS) vulnerability allows an attacker to inject malicious code into the emotions.php by providing XSS payload as a value for field_name.
Remediations
Download the latest version and update it as per the vendor advisory.
Timeline
Nov 06, 2015: Reported to Vendor
Nov 06, 2015: Vendor Response
Nov 07, 2015: Vendor Released Fixed
Nov 13, 2015: Public Disclosure
Aug 08, 2020: CVE Assigned