A Cross-Site Scripting vulnerability was identified in WordPress plugin Fast Secure Contact Form before 4.0.37 in fs_contact_form1[welcome].
Securin Zero-Days
CVE-2015-9539 – Reflected XSS in Fast Secure Contact Form
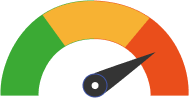
Severity:High
Vendor
Fast Secure
Affected Product
Fast Secure Contact Form
CVE
CVE-2015-9539
Securin ID
2015-CSW-09-1007
Status
Fixed
Date
September 7, 2015
Description
Proof of Concept (POC):
Visit the following page on a site with this plugin installed.
http://yourwordpresssite.com/wordpress/wpadmin/plugins.php?page=sicontactform%2Fsi-contact-form.php&fscf_form=1&fscf_tab=1 and modify the value of fs_contact_form1[welcome] variable with <script>alert(document.cookie);</script> payload and send the request to the server. Now, the added XSS payload is echoed back from the server without validating the input whenever we visit the script stored page.
Note: XSS payload has been tried with the application once after implementing Unfiltered Html Settings as defined to the wp-config.php file.
define( ‘DISALLOW_UNFILTERED_HTML’, true );
Issue: POST request parameter fs_contact_form1[welcome] variable in the given URL http://yourwordpresssite.com/wordpress/wpadmin/plugins.php?page=sicontactform%2Fsi-contact-form.php&fscf_form=1&fscf_tab=1 of Fast Secure Contact Form 4.0.37 is vulnerable to Cross-Site Scripting (XSS).
.png)
.png)
Figure 02: XSS Payload is executed in the browser whenever the user views it.
Impact
An attacker can inject malicious code into the applications via a vulnerable variable.
Remediations
Download the latest updated version of the Nextgen plugin and apply the patch as per vendor advisory.
Timeline
Sep 05, 2015: Discovered in Fast Secure Contact Form plugin 4.0.37 Version.
Sep 07, 2015: Reported to WP Plugin.
Sep 07, 2015: WP acknowledged the issue.
Sep 08, 2015: Fixed in 4.0.38 version of Fast Secure Contact Form plugin.