A Cross-Site Scripting (XSS) vulnerability was identified on the WordPress plugin NextGen Gallery before 6.0.4.
Securin Zero-Days
CVE-2015-9410 – Cross Site Scripting Vulnerability in Blubrry PowerPress
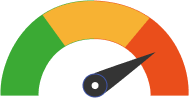
Severity:High
Vendor
Blubrry PowerPress
Affected Product
Blubrry PowerPress Podcasting
CVE
CVE-2015-9410
Securin ID
2015-CSW-09-1006
Status
Fixed
Date
September 4, 2015
Description
Proof of Concept (POC):
Visit the following page on a site with this plugin
http://yourwordpresssite.com/wordpress/wpadmin/admin.php?page=powerpress/powerpressadmin_basic.php and modify the value of tab variable with “></script><script>alert(document.cookie);</script> payload and send the request to the server. Now, the added XSS payload is echoed back from the server without validating the input. It also affects the wp-config.php file, $table_prefix, and corrupts the database connectivity.
Note: XSS payload has been tried with the application once after implementing Unfiltered Html Settings as defined to the wp-config.php file.
define( ‘DISALLOW_UNFILTERED_HTML’, true );
Issue 1: The Post Request tab variable in the URL http://localhost/wordpress/wp-admin/admin.php?page=powerpress/powerpressadmin_basic.php is vulnerable to Cross-Site Scripting (XSS).
.png)
Figure 01: Invalid HTTP script Request sent to the server through the vulnerable tab variable in the URL http://yourwordpresssite.com/wordpress/wp-admin/admin.php?page=powerpress/powerpressadmin_basic.php and its echoed back in the HTTP Response without validation.
Impact
An XSS vulnerability allows an attacker to inject malicious code into the applications via the images [1] [alttext] parameter.
Remediations
Download the latest updated version of Blubrry PowerPress Podcasting and apply the patch as per vendor advisory.
Timeline
Sep 04, 2015: Discovered in Blubrry PowerPress Podcasting plugin 6.0.4 version.
Sep 04, 2015: Reported to WordPress.
Sep 07, 2015: The vendor acknowledged the issue.
Sep 09, 2015: Fixed in Blubrry PowerPress Podcasting plugin 6.0.5 version.