A Cross-Site Scripting vulnerability was identified on WordPress plugin BulletProof Security before .52.5 in the admin/db-backup-security/db-backup-security.php page.
Securin Zero-Days
CVE-2015-9230 – Cross-Site-Scripting Vulnerability in AIT Pro BulletProof Security
Severity:Medium
Vendor
AIT Pro BulletProof
Affected Product
AIT Pro BulletProof Security
CVE
CVE-2015-9230
Securin ID
2015-CSW-09-1005
Status
Fixed
Date
September 4, 2015
Description
Proof of Concept (POC):
Visit the following page on a site with this plugin installed.
http://yourwordpresssite.com/wordpress/wpadmin/admin.php?page=bulletproofsecurity/admin/db-backup-security/db-backup-security.php and modify the value of DBTablePrefix variable with “></script><script>alert(document.cookie);</script> payload and send the request to the server. Now, the added XSS payload is echoed back from the server without validating the input. It affects the wp-config.php file, $table_prefix, and corrupts the database connectivity.
Note: XSS payload has been tried with the application once after implementing Unfiltered Html Settings as defined to the wp-config.php file.
Define (‘DISALLOW_UNFILTERED_HTML’, true);
Users: You must be an Administrator and logged into the site as an Administrator to enter/test the XSS HTML testing code in the Randomly Generated DB Table Prefix Form text box. Please do not try this test if you are using a version of BPS versions. Entering an invalid DB Table Prefix name will crash your website.
Issue 1: The Post Request DBTable Prefix variable in the URL http://yourwordpresssite.com/wordpress/wpadmin/admin.php?page=bulletproofsecurity/admin/db-backup-security/db-backup-security.php is vulnerable to Cross-Site Scripting (XSS).
.png)
Figure 01:Invalid HTTP script Request sent to the server through the vulnerable DBTablePrefix variable in the URL http://localhost/wordpress/wpadmin/admin.php?page=bulletproof-security/admin/db-backup-security/db-backup-security.php
.png)
Figure 02: Echoed back HTTP Response without validation.
.png)
Figure 03: Response Executed in the browser with the Cookie value.
.png)
Figure 04: $table_prefix is also damaged with the given XSS Payload.
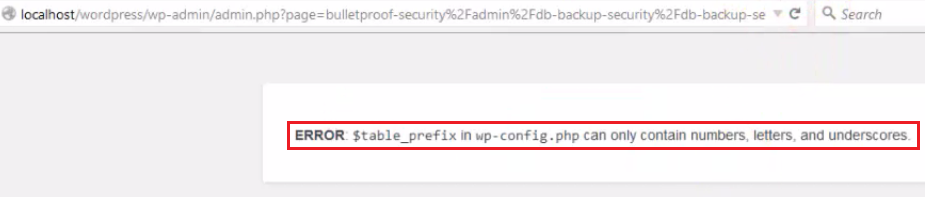
Figure 05: Error message after the payload gets executed in the browser.
Impact
An XSS vulnerability allows an attacker to inject malicious code into the applications via the DBTablePrefix parameter.
Remediations
Download the latest updated version of the Nextgen plugin and apply the patch as per vendor advisory.
Timeline
Sep 04, 2015: Discovered in AIT Pro BulletProof Security Plugin.
Sep 04, 2015: Fixed in AIT Pro BulletProof Security Plugin Version .52.5.