Did you know that over 80% of data breaches have been linked to poor password security?
Passwords serve as one of the primary barriers between your sensitive data and the outside world. The surge in online accounts, spanning shopping platforms to restaurant apps, necessitates multiple passwords for users. While this brings convenience, it concurrently broadens the attack surface, providing hackers with numerous entry points to compromise personal information across diverse online services. Therefore, it is vital to not only create strong passwords but to also manage them effectively. This entails ensuring they are securely stored and regularly updated, implementing robust account authentication practices, devising strategies for password recovery, and, most importantly, setting up strong protocols for those instances when a password is forgotten or compromised.
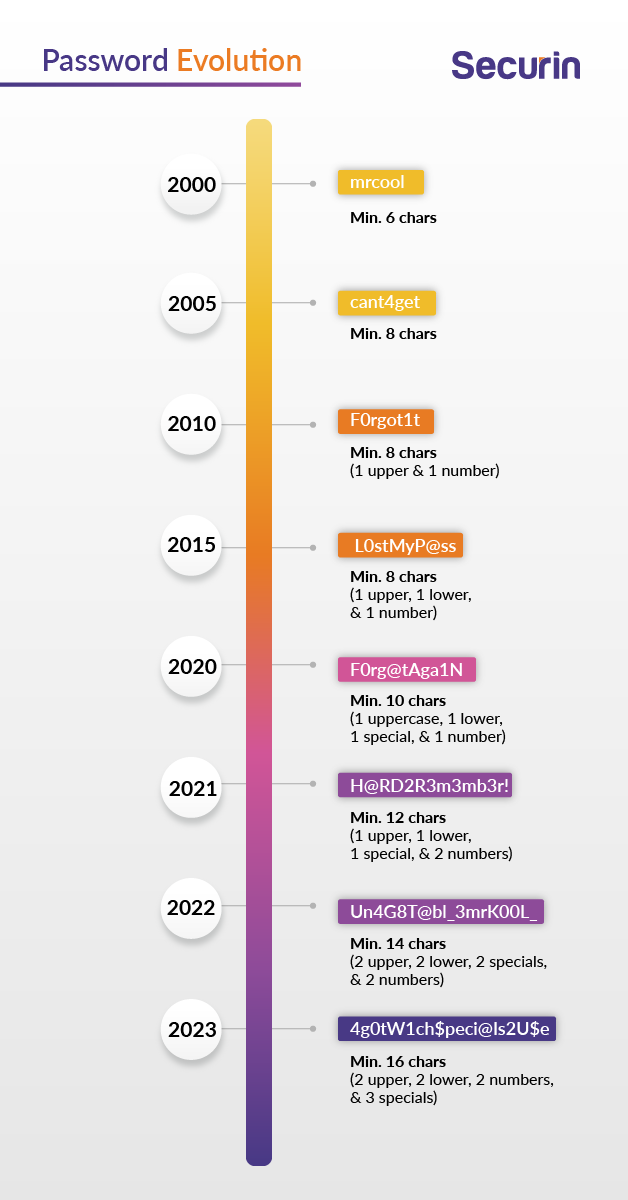
Over the past decade, password requirements have significantly evolved, with the length of passwords expanding from a mere six characters to at least 16 or more. This transformation is a direct response to the growing sophistication of cyber threats, as hackers employ increasingly powerful methods to crack passwords and compromise accounts.
Today, complex passphrases, which are easier to remember and feature a combination of upper and lower-case letters, numbers, and special characters, have become the new standard. Longer and more complex passwords or passphrases provide a higher level of resistance against such attacks. For instance, a 12-character password would take 62 trillion times longer to crack than a six-character password.
Understanding Password Attacks and Security
Passwords can be the weakest link in the security chain. Users often choose predictable combinations, employ easily guessable personal information, or recycle passwords across multiple accounts. Today, it is estimated that more than 24 billion usernames and passwords are available for sale on the dark web. Furthermore, they are not that expensive to purchase with many on sale for less than $5.
A successful breach from a compromised password can lead to identity and financial theft, fraud, and unauthorized access to an organization’s vital services. A compromised password may lead to perpetrators assuming your identity, harassing others using your accounts, stealing money, selling your data on the dark web, or engaging in blackmail. In an organizational context, a password breach can compromise sensitive business data, damage reputations, and result in financial and legal repercussions. This makes passwords prime targets for attackers who exploit various techniques and tools to crack them, most often trying one after the other till one cracks the password.
- Brute Force Attacks: This method is time-consuming and only occasionally successful. Attackers use specialized brute force password cracking software such as Burp Suite, THC-Hydra, and AirCrack to automate the generation and testing of countless password combinations. Additionally, Graphic Processing Units (GPU) acceleration and distributed computing systems are often employed to speed up the process.
- Dictionary Attacks: Attackers utilize dictionary files containing millions of words that are repeatedly tried against multiple accounts. In dictionary attacks, attackers have been known to use software such as Hashcat, John The Ripper, or CrackStation to guess the target’s password. However, breaking into an account protected by a robust 16-digit password containing various special characters and numbers would pose an almost insurmountable challenge for conventional computers. The advent of quantum computers, on the other hand, might alter this equation.
- Rainbow Table Attacks: Rainbow table attacks are used to crack encrypted or hashed passwords. Rainbow tables are precomputed lists of hashed passwords and their corresponding plaintext forms, used to rapidly decrypt hashed passwords. RainbowCrack and Ophcrack are tools that automate the process.If a match is found, the original password is revealed.
- Phishing Attacks: Phishing attacks trick users into revealing their passwords through deceptive emails, websites, or messages. Attackers craft convincing fake websites or emails that closely mimic legitimate ones, aiming to steal login credentials when users enter them. Timing is also a factor, with attacks often synchronized with current events for added credibility and effectiveness. Attackers may cast a wide net by sending mass emails, or target individuals or organizations based on their potential value.
- Social Engineering Attacks: These attacks rely on psychological manipulation, such as impersonating trusted entities and conducting persuasive phone calls to gain the trust of the target. Attackers often use a pretext, a fabricated reason or scenario, to engage with the target, such as posing as an IT technician or a manager requesting sensitive information.
- Keylogging Attacks: Keyloggers are hardware devices or malware programs that capture keystrokes, including passwords, without the user’s knowledge. Typically, keylogger software must be delivered to the victim’s device, often through malicious email attachments, infected software downloads, or compromised websites. It is important to be cautious about the sources of software installations, as attackers often use remote access tools, such as RATs (Remote Access Trojans), to monitor and retrieve recorded data.
- Credential Stuffing Attacks: Credential stuffing exploits the habit of users reusing passwords across multiple online services and involves using username and password combinations acquired from data breaches or the dark web. Successful breaches can happen within minutes or seconds, depending on the target’s security measures and the volume of attempts. Typically, attackers tend to target services with weak security measures to limit login attempts or detect unusual activity.
- Man-in-the-Middle Attacks (MITM): Attackers position themselves between the user and the target server, intercepting data and potentially altering or capturing login credentials and other sensitive information as they pass through the network. MITM attacks involve the use of specialized software tools that facilitate traffic interception, such as Wireshark, ettercap, or tools for setting up rogue access points (such as on an unsecured Wi-Fi network). Password attacks, whether they employ brute force, social engineering, or other methods, exploit specific vulnerabilities. These attacks are not isolated incidents; instead, they depend on the convergence of the following success-critical elements.
Key Factors for a Successful Password Attack
- Password Weakness and Predictability: Easy-to-guess passwords or those based on common patterns are more vulnerable than a robust 16-digit password containing various special characters and numbers.
- Computing Power and Speed: The attacker’s system capabilities influence the speed of password attempts. For instance, a powerful system allows quicker execution of brute force or dictionary attacks.
- Size and Quality of Dictionary File: A comprehensive dictionary file increases the chances of success in dictionary attacks.
- Attacker’s Determination and Patience: Persistent attackers willing to invest time have higher probabilities of success, especially through prolonged methods like brute force.
- Target’s Account Lockout Policies: If a system has lenient lockout policies, attackers can make multiple attempts without being significantly hindered.
- Size of the Rainbow Table: For hashed passwords, a larger rainbow table enhances the chances of finding matches.
- Strength of Password Hashing Method: Strong hashing methods pose a greater challenge for attackers, as they require more computational effort to crack.
- Uniqueness of the Salt: A unique salt adds complexity to hashed passwords, making them harder to crack, especially when it’s unpredictable.
- Weak or Out-of-Date Antivirus/Anti-Malware: Outdated or ineffective security software provides less resistance against malware, including keyloggers and password-stealing threats.
- Unencrypted Communication Channels: Insecure communication channels expose passwords during transmission, allowing attackers to intercept and compromise them.
Bolstering your passwords is crucial in fortifying the security of your valuable information. A weak password or the reuse of passwords across multiple accounts poses a significant risk, potentially compromising your personal and sensitive data. As password strength directly correlates with the security of your valuable information, it is essential to take the effort to create and store passwords well. Safeguard your digital presence by adhering to these essential password protection practices, mitigating the vulnerabilities associated with inadequate password practices and enhancing your overall cybersecurity posture. Here is a checklist of password protection practices that can help you improve your security posture.
Password Protection Checklist
-
Form complex, long, and memorable passphrases with a mix of alpha-numeric and special characters.
- Consider unconventional techniques, like misspelled words or reversed spellings for extra security.
- Enable Multi-Factor Authentication (MFA) for accounts whenever possible.
- Employ hardware tokens for sensitive accounts, while ensuring tokens are physically secure.
- Use a reliable password manager with a long and strong master passphrase.
- Utilize biometric authentication methods while ensuring the secure storage of biometric data.
- Regularly review account-related emails and notifications promptly to prevent unauthorized access.
- Customize security questions with memorable but false information, avoiding common and easily researched questions
- Implement account lockout policies to protect users by temporarily suspending access after multiple failed login attempts.
- Avoid using personal information in passwords, such as children’s names or birthdates.
- Never use default passwords or share passwords, even with friends or colleagues.
- Do not allow web browsers to save or autofill passwords.
- Always lock your devices and never leave them unattended in public, regardless of password strength.
- Diversify passwords for increased security. Avoid using the same password for multiple accounts.
- Understand account recovery procedures and regularly review and update stored passwords, especially for critical accounts.
- When feasible, periodically change passwords for high-value accounts to maintain security.
- Use up-to-date software, especially antivirus and anti-malware and enable firewalls.
- For advanced security, use salted and iteratively hashed passwords.
- Practice caution with email attachments and downloads. Be up to date about the latest phishing techniques and scams.
- Never share credentials in response to email requests.
- Always verify the sender’s email address and log in directly to websites such as Facebook or Instagram, not through email links.
In an era marked by accelerating technological advancements, the landscape of password protection is on the cusp of a major transformation. With cyber threats becoming increasingly sophisticated and the growth of IoT connected devices, we need to make use of evolving trends and cutting-edge technologies that will shape the future of password security.









