Nobelium, the APT group behind the infamous attack on SolarWinds, has resurfaced in two recent campaigns against US-based IT companies and government organizations. Check out Securin’s analysis of 18 vulnerabilities used by the group to exploit and infiltrate their targets.
In the last week of June 2021, the attackers behind the infamous SolarWinds supply chain incident were back again, targeting Microsoft’s corporate network. The group is said to have stolen credentials from one of its customer service agents and used the information to launch attacks against other Microsoft clients, compromising at least three customer accounts.
Earlier, in May 2021, the same group was identified impersonating a US government agency. The cyberattack piggybacked on a marketing email account of the US Agency for International Development (USAID) and managed to reach 3,000 email accounts across 150 different organizations. However, the White House claims that the intruding attempts were curbed, by and large, and the “noisy” campaign did not cause much damage.
Dubbed the Nobelium campaign, the attacks have been attributed to the Russian state-sponsored threat group Nobelium, which has been operational since 2008. The group is also known as APT29, Cozy Bear, The Dukes, and UNC2452 and has 11 other aliases.
More recently, in early July, the APT29 group was deemed responsible for an attack on the American Grand Old Party or the Republican Party.
Vulnerabilities in APT 29’s Radar
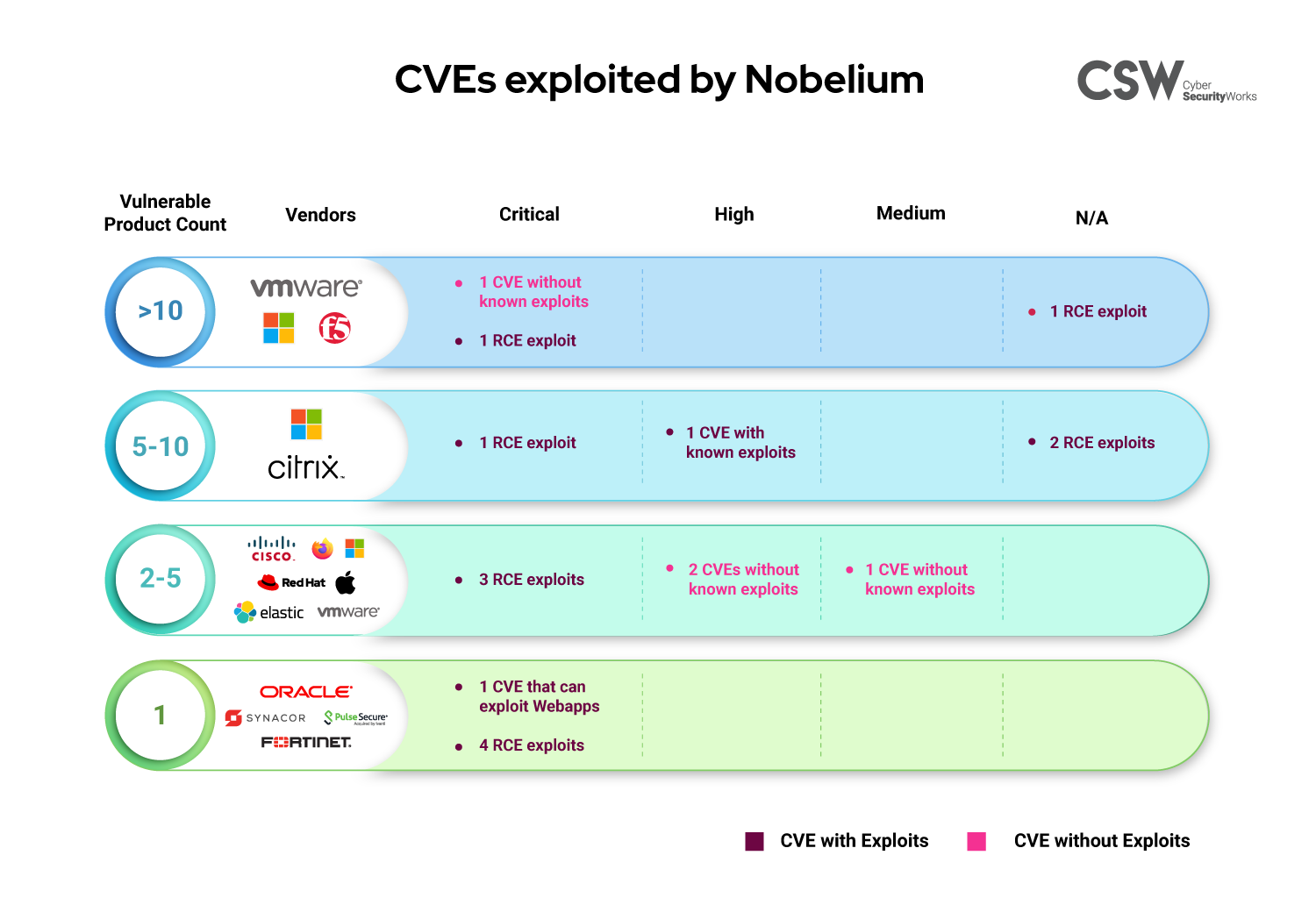
Securin’s dynamic threat database has mapped 18 CVEs to APT29, popularly called the Nobelium group. Here is our analysis of these vulnerabilities:
Exploits and Trends
-
Fourteen CVEs are capable of remote code execution, while eight CVEs have associated WebApp exploits, with a few having both capabilities.
-
Twelve of the associated vulnerabilities are recently trending CVEs, according to Google Trends.
-
The oldest vulnerability exploited by Nobelium is from 2009, and three CVEs were newly discovered this year.
Severity and Weaknesses
-
A severity analysis of the CVEs brings out 11 vulnerabilities that have been deemed critical by CVSS V3 scoring and three high-ranked ones.
-
Three CVEs have CVSS V3 scores lesser than eight, illustrating that low-scoring vulnerabilities are also ripe targets for exploitation.
-
Twelve weaknesses power these vulnerabilities, seven of which feature in MITRE’s Top 25 CWEs of 2020.
Products and Vendors
-
There are five vulnerabilities, including CVE-2020-0674 and CVE-2021-26855, across 35 different products from Microsoft that have been recently trending.
-
Other than Microsoft, the vulnerabilities are present across products of vendors, including Pulse Secure, Citrix, Fortinet, Cisco, Mozilla, Elastic, Redhat, Sycamore, Oracle, VMware, Apple, and F5.
-
Fourteen F5 products that provide multi-cloud security and application services are vulnerable to CVE-2020-5902, which can be exploited remotely.
Patches and Weaponization
-
All vulnerabilities have patches available. Considering the fact that these vulnerabilities led to the biggest cyberattack of recent times, organizations should prioritize them for patching immediately.
-
Interestingly, Securin called out CVE-2021-26855 in the Ransomware Spotlight report Q1 update for how rapidly it was weaponized and started trending in the wild.
Securin warned about seven (7) vulnerabilities in APT29’s collection in our Ransomware Reports published in February and May 2021.
| CVEs called out by Securin |
| CVE-2015-1641 |
| CVE-2018-13379 |
| CVE-2019-11510 |
| CVE-2019-19781 |
| CVE-2019-2725 |
| CVE-2020-5902 |
| CVE-2021-26855 |
APT29 has been identified as deploying the Maze ransomware while targeting victims.
APT29—Attack Methodology
The initial vector in the government agencies’ attack was a phishing campaign. The hackers masqueraded as the government body and sent emails to different accounts across international development, humanitarian, and human rights organizations. The attempt was majorly thwarted as automated systems detected unusual email activity and blocked them. However, the emails that did manage to get through contained beacon malware, which—when clicked—allowed for a system compromise.
The figure below shows a sample phishing email.
Image Source: https://www.microsoft.com/security/blog/2021/05/27/new-sophisticated-email-based-attack-from-nobelium/
In the case of the Microsoft attack, the group used password spraying and brute-force attacks to extract passwords that could help gain entry into customer accounts.
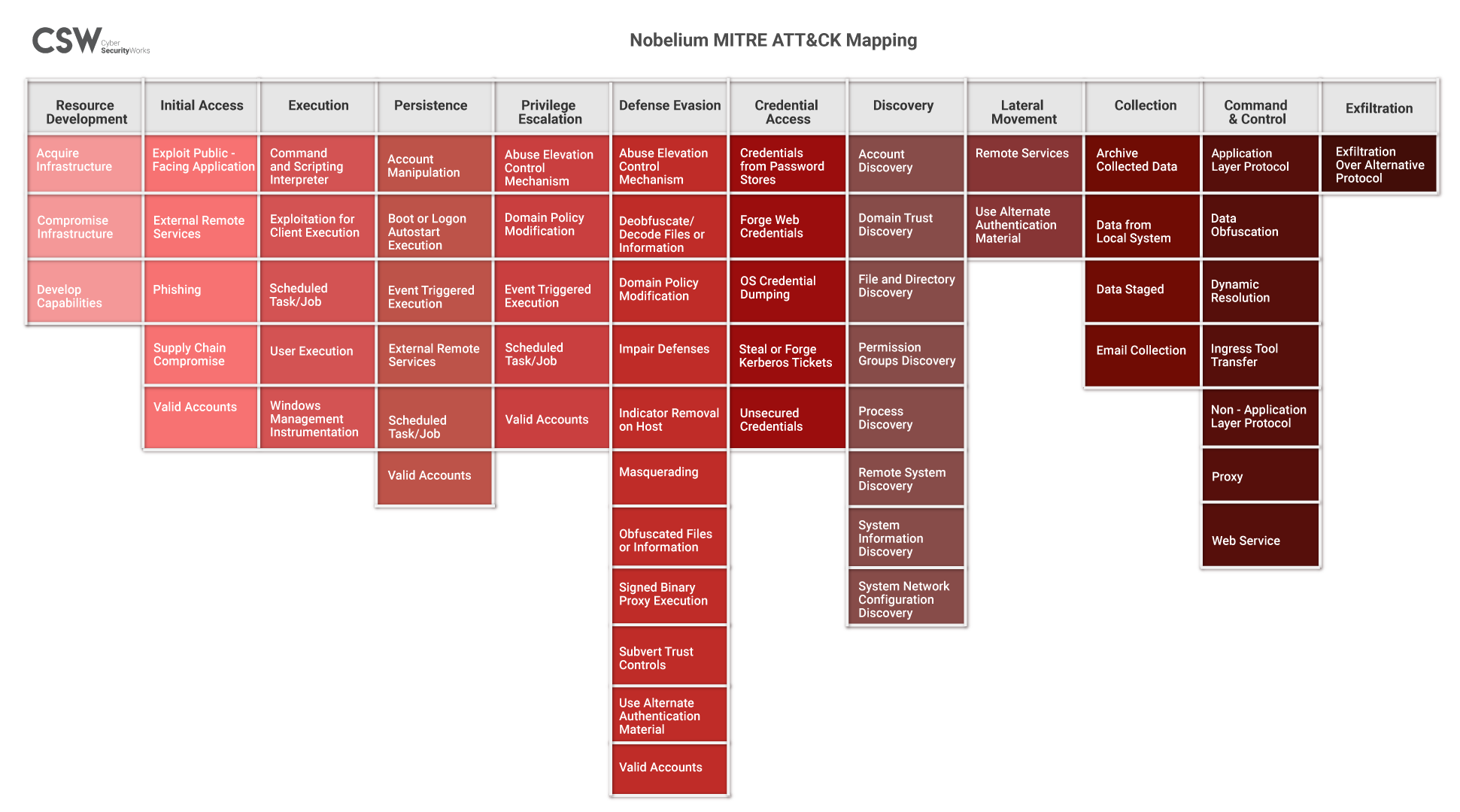
MITRE ATT&CK and Mapping
We have listed the tactics adopted by the APT29 group in the Nobelium campaign.
IOCs (SHA 256)
A4B790DDFFB3D2E6691DCACAE08FB0BFA1AE56B6C73D70688B097FFA831AF064
65495D173E305625696051944A36A031EA94BB3A4F13034D8BE740982BC4AB75
58D8E65976B53B77645C248BFA18C3B87A6ECFB02F306FE6BA4944DB96A5EDE2
83014AB5B3F63B0253CDAB6D715F5988AC9014570FA4AB2B267C7CF9BA237D18
0C5AD1E8FE43583E279201CDB1046AEA742BAE59685E6DA24E963A41DF987494
F622D031207D22C633CCEC187A24C50980243CB4717D21FAD6588DACBF9C29E9
FD3969D32398BBE3709E9DA5F8326935DDE664BBC36753BD41A0B111712C0950
E3D6057B4C2A7D8FA7250F0781EA6DAB4A977551C13FE2F0A86F3519B2AAEE7A
F3AF394D9C3F68DFF50B467340CA59A11A14A3D56361E6CFFD1CF2312A7028AD
E329607379A01483FC914A47C0062D5A3A8D8D65F777FBAD2C5A841A90A0AF09
DD3DA0C596FD699900CDD103F097FE6614AC69787EDFA6FA84A8F471ECB836BB
D7E7182F498440945FC8351F0E82AD2D5844530EBDBA39051D2205B730400381
BEC1981E422C1E01C14511D384A33C9BCC66456C1274BBBAC073DA825A3F537D
C1A0B73BAD4CA30A5C18DB56C1CBA4F5DB75F3D53DAF62DDC598AAE2933345F3
B75A5BE703D9BA3721D046DB80F62886E10009B455FA5CDFD73CE78F9F53EC5A
A3CA47E1083B93EA90ACE1CA30D9EF71163E8A95EE00500CBD3FD021DA0C18AF
A117B2A904C24DF62581500176183FBC282A740E4F11976CDFC01FE664A02292
A03A71765B1B0EA7DE4FBCB557DCFA995FF9068E92DB9B2DADA9DD0841203145
93E9383AE8AD2371D457FC4C1035157D887A84BBFE66FBBB3769C5637DE59C75
953B5FC9977E2D50F3F72C6CE85E89428937117830C0ED67D468E2D93AA7EC9A
92A856A2216E107496EE086E1C8CFE14E15145E7A247539815FD37E5A18B84D9
8749C1495AF4FD73CCFC84B32F56F5E78549D81FEEFB0C1D1C3475A74345F6A8
84B846A42D94431520D3D2D14262F3D3A5D96762E56B0AE471B853D1603CA403
797159C202CA41356BEE18C5303D37E9D2A43CA43D0CE02E1FD9E7045B925D11
7C39841BA409BCE4C2C35437ECF043F22910984325C70B9530EDF15D826147EE
4C8671411DA91EB5967F408C2A6FF6BAF25FF7C40C65FF45EE33B352A711BF9C
5CA4A9F6553FEA64AD2C724BF71D0FAC2B372F9E7CE2200814C98AAC647172FB
49BFFF6B91EE71BBF8FD94829391A36B844FFBA104C145E01C92732ADA52C8BA
2DABA469F50CD1B77481E605AEAE0F28BF14CEDFCD8E4369193E5E04C523BC38
21129AD17800B11CDB36906BA7F6105E3BD1CF44575F77DF58BA91640BA0CAB9
2285A264FFAB59AB5A1EB4E2B9BCAB9BAF26750B6C551EE3094AF56A4442AC41
14E9B5E214572CB13FF87727D680633F5EE238259043357C94302654C546CAD2
1FED2E1B077AF08E73FB5ECFFD2E5169D5289A825DCAF2D8742BB8030E487641
0B8E6A11ADAA3DF120EC15846BB966D674724B6B92EAE34D63B665E0698E0193
03E9ADAE529155961F1F18212FF70181BDE0E3DA3D7F22961A6E2B1C9DA2DD2E
0322C4C2D511F73AB55BF3F43B1B0F152188D7146CC67FF497AD275D9DD1C20F
00654DD07721E7551641F90CBA832E98C0ACB030E2848E5EFC0E1752C067EC07
4DEC3EEEFCEC013F142386D5C54099D3DAA2B48D559434DB1D4F2078D704DA1B
0F04F199327D0D076815190DC024F4A6B0F27899D50D28E94662820AB9C945D2
478B04C20BBF6717D10EE978B99339B7C4664FEBC8BCFDAF86C3F0FBFC83A5C5
85E72976B9448295034A8D4C26462B8F1EBE1CA0A4E4B897C7F2404D0DE948C2
11DF3B7B4EE24E1EBC8901058EC0A7EEF7CDF79227A2E3B4E5ED31A110B94ED7
B132579DA1340654277945EBA64EC9E93D058E4B2057BDC4410F3B583009002C
398B112EF1BD32C81A49BED31AE7216D3C1DA89924755B0A478A1CDB1B4E0A6D
07F9076BF3499974883F4344FDAF51B2261B20D992B069378C4D16F4BFC93AF6
1A8D8A209D46ADA8966ED371EE2E28079B9DCEF0B37E85C8024D86C427E1017B
B77FF307EA74A3AB41C92036AEA4A049B3C2E69B12A857D26910E535544DFB05
68B2524160410A18CD61BA66D9699CDFDE6A4C7FFC207667D20C90FA84A03A87
D0D626DEB3F9484E649294A8DFA814C5568F846D5AA02D4CDAD5D041A29D5600
4E8F24FB50A08C12636F3D50C94772F355D5229E58110CCCB3B4835CB2371AEC
6B01EEEF147D9E0CD6445F90E55E467B930DF2DE5D74E3D2F7610E80F2C5A2CD
CB80A074E5FDE8D297C2C74A0377E612B4030CC756BAF4FFF3CC2452EBC04A9C
E9DDF486E5AEAC02FC279659B72A1BEC97103F413E089D8FABC30175F4CDBF15
EC5F07C169267DEC875FDD135C1D97186B494A6F1214FB6B40036FD4CE725DEF
F2A8BDF135CACA0D7359A7163A4343701A5BDFBC8007E71424649E45901AB7E2
7E05FF08E32A64DA75EC48B5E738181AFB3E24A9F1DA7F5514C5A11BB067CBFB
BBD16685917B9B35C7480D5711193C1CD0E4E7CCB0F2BF1FD584C0AEBCA5AE4C
B9A2C986B6AD1EB4CFB0303BAEDE906936FE96396F3CF490B0984A4798D741D8
611458206837560511CB007AB5EEB57047025C2EDC0643184561A6BF451E8C2C
9B33EC7F5E615A6556F147B611425D3CA4A8879CE746D4A8CB62ADF4C7F76029
Targeted Sectors and Countries
An analysis of the Nobelium campaign shows multiple sectors being targeted: Pharmaceuticals and Biotechnology, Aerospace and Defense, Media and Entertainment, Telecommunications, Energy and Natural Resources, Law, Information Technology, Consulting, Healthcare, Healthcare Providers, Finance, Education, and Research.
The campaign was carried out across Belgium, Israel, Italy, the United States, Turkey, India, Luxembourg, the United Kingdom, Canada, Chile, France, Mexico, Germany, Thailand, Switzerland, Denmark, the United Arab Emirates, Bulgaria, Spain, Ireland, and Singapore.
Exposure
The following are the results of the Nobelium vulnerabilities that have a direct CVE exposure, according to Shodan. Cumulatively, these amount to over 20,000 exposed instances where attackers have a clear advantage.
| CVE-2020-5902 (F5 vulnerability) | CVE-2019-19781 (Citrix vulnerability) |
| CVE-2019-1653 (Cisco vulnerability) | CVE-2019-11510 (Pulse Secure) |
| CVE-2021-26855 (Exchange server RCE) | |
Given the history of APT29, CISA published a warning by Microsoft on May 27, 2021, describing the campaign as sophisticated, one that evolved over the course of five months.
Increasing Attacks Demand a Change in the Cybersecurity Strategy
While the recent Nobelium campaigns seem to have been subdued compared to the SolarWinds impact, we can see increasing attacks on organizations in the US by Russia-backed actors and associated ransomware groups. Beginning with the impactful Colonial Pipeline attack, followed by the Ireland Health Service Executive (HSE) attack, the JBS attack, the Nobelium campaign, the SolOriens attack, and the recent Microsoft campaign, Russian APT groups are directly or indirectly linked to this flurry of high-profile cyberattacks. Propelled by these findings, cybersecurity was discussed as a priority in the recently concluded summit between Russian President Vladimir Putin and US President Joe Biden.
Today’s cybercrime activities are moving toward high-impact attacks, posing a high risk to all organizations alike, including federal entities. Organizations need to shift from a defensive mindset to an offensive approach to stay ahead of threat actors. This calls for a rigorous analysis of an organization’s risk exposure, backed by a well-informed database that enables the organization to evaluate looming threats and deal with the ones that matter the most.
We urge all organizations to patch the vulnerabilities on priority in order to avoid another supply chain attack.
Read on to learn more about our analysis of the group and patch the associated vulnerabilities before it is too late.
{Update September 03, 2021}: Autodesk, a US-based software company known for its 3D computer-aided design and modeling tools software AutoCAD, has revealed that one of its servers was backdoored with the Sunburst malware during the SolarWinds supply chain attack in December 2020. Clearly, attacks are becoming more sophisticated, with organizations realizing the breach only months later and its impact being felt a long time after the attack.
{Update September 30, 2021}: After being associated with the WellMess malware in July 2021, the Nobelium group has now been identified as deploying two new backdoors, Tomiris and FoggyWeb. These have been recently trending, giving us enough reasons to believe that the threat group is slowly developing its techniques and tactics.
{Updated November 02, 2021}: On October 24, 2021, researchers noticed new tactics and techniques being used by the Nobelium group. The Nobelium group is trying to replicate an older approach that targets companies integral to the global IT supply chain. The intention is to attack resellers and other service providers who customize, manage, and deploy cloud services on behalf of the customer. The attack campaigns targeting resellers and service providers observed thus far have not exploited any software vulnerability but are using well-known techniques, such as password phishing and spraying, to steal legitimate credentials in the hope of gaining privileged access.
{Updated on February 08, 2022}: The threat actor behind the SolarWinds supply chain attack, Nobelium, has been continually expanding its malware arsenal, with the newest additions being two sophisticated malware families—GoldMax, a Linux variant and TrailBlazer, a new implant—that were recently discovered on a victim network.
Securin can help organizations improve their security posture!