Rhysida ransomware emerged in May 2023 when it began targeting the education sector, critical manufacturing, tech industries and the government. They became more widely known in August 2023, after a series of attacks on healthcare and public health organizations. The Health Sector Cybersecurity Coordination Centre (HC3) put out an advisory about the new ransomware threat. By the end of January 2024, the group had listed 150+ victims spread across 25 countries.
Rhysida Ransomware: Vice Society Rebranded?
Though Rhysida ransomware leverages tactics, techniques and procedures (TTPs) that are eerily similar to Vice Society, there is still not enough proof to declare Rhysida ransomware as a rebrand of Vice Society ransomware. Ongoing monitoring and collaboration from the cybersecurity community can help to build a more complete picture of the Rhysida ransomware.
Rhysida Ransomware: Attack Vectors
Rhysida ransomware threat actors have been known to use legitimate software to infiltrate and compromise target networks.
- PowerShell to gain information about their users and systems within the network
- PSExec is used to schedule tasks and make changes to registry keys to maintain persistence
- AnyDesk is used for remote connections
- WinSCP helps them transfer files
- MegaSync is leveraged to exfiltrate data from victim machines
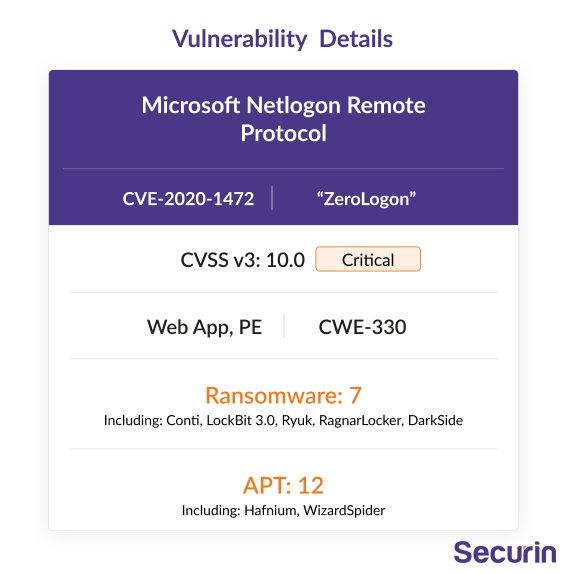
The vulnerability that was most often leveraged by Rhysida ransomware to gain access to target networks was a four-year-old flaw privilege escalation flaw in Microsoft’s Netlogon Remote Protocol, popularly referred to as ‘ZeroLogon’ (CVE-2020-1472) and was called out by Securin experts as far back as 2022, and by CISA in their KEV catalog in November 2021. The patch for the vulnerability was released in August 2020.
Rhysida Ransomware: Victim Patterns and Sectors Targeted
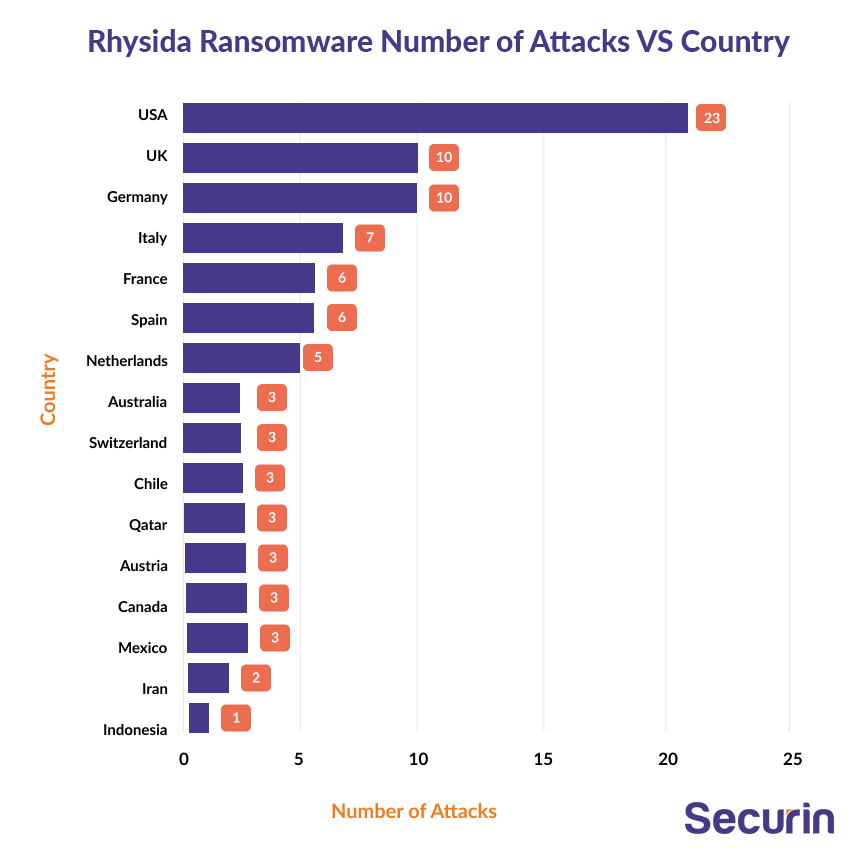
Rhysida ransomware has had a global impact, with a large concentration of incidents in North America, primarily in the USA, and a smattering of attacks in Asia, Australia, Europe and South America. The sectors most heavily targeted by Rhysida ransomware have been the Education sector, with 13 identified targets, the Critical Infrastructure and Manufacturing sector, with 9 targets, and the IT, Communications & Mass Media sector, with 7 targets.
The heat map provides an insight into the workings of the ransomware group and which sectors must remain vigilant towards possible cyber incursions and therefore consolidate their weak network endpoints.
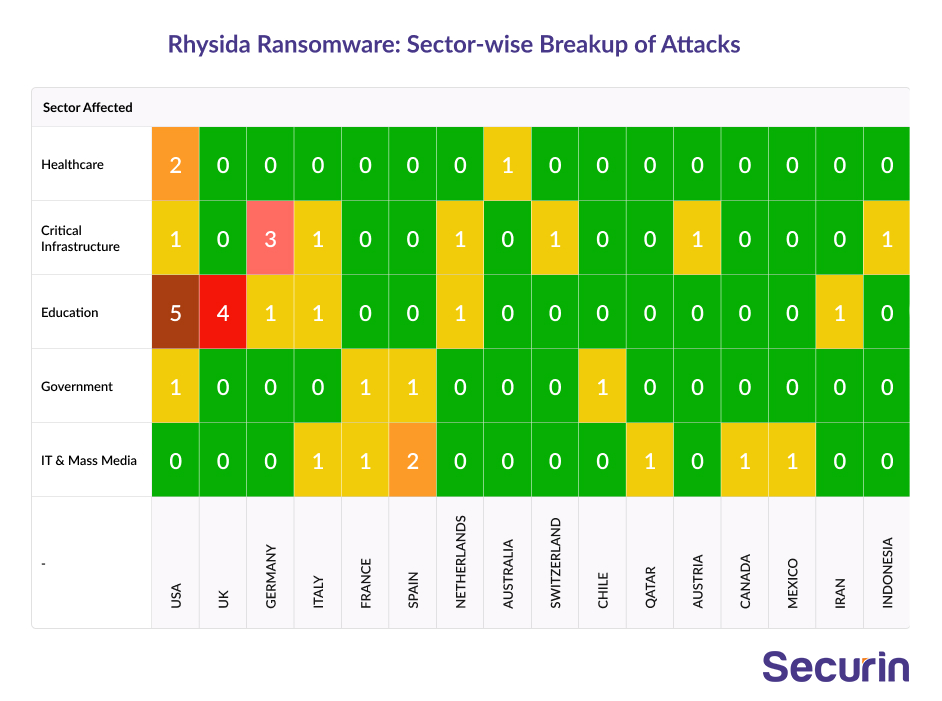
By analyzing this data, businesses can prioritize their cybersecurity efforts and focus on shoring up the weaknesses in their network endpoints to better defend against potential attacks. This insight enables proactive measures to be taken, such as implementing robust security measures, conducting thorough vulnerability assessments, and enhancing overall resilience to mitigate the impact of possible ransomware attacks.
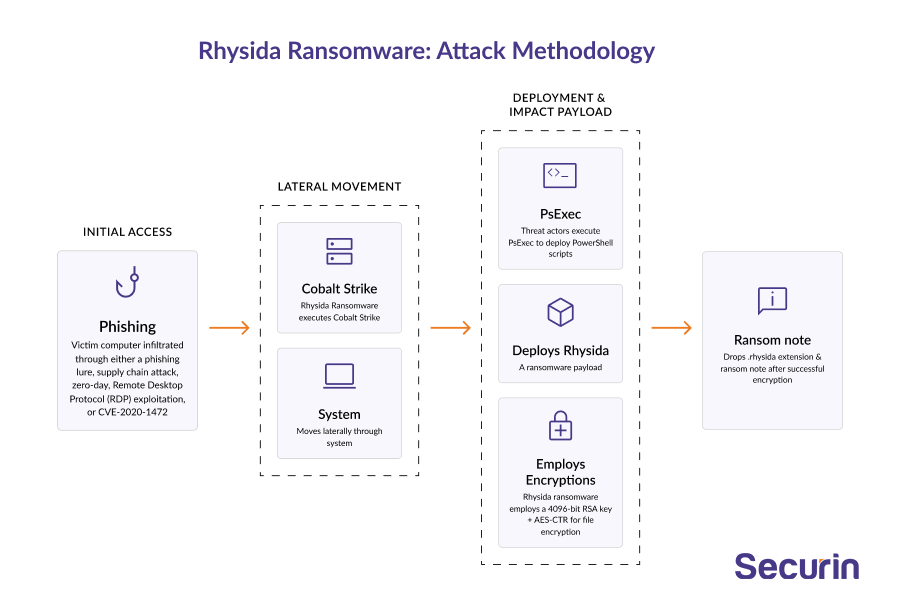
Rhysida Ransomware: Attack Methodology
Rhysida ransomware typically spreads through malicious email attachments or downloads from compromised websites. Once it infects a system, it encrypts files and demands a ransom in exchange for the decryption key.
Rhysida Ransomware: MITRE Mapping
MITRE ATT&CK mapping involves aligning cybersecurity techniques and tactics with the globally-accessible knowledge base known as ATT&CK, developed by MITRE. This framework categorizes tactics, techniques, mitigations, and campaigns, offering a comprehensive view of cybersecurity threats and defenses.
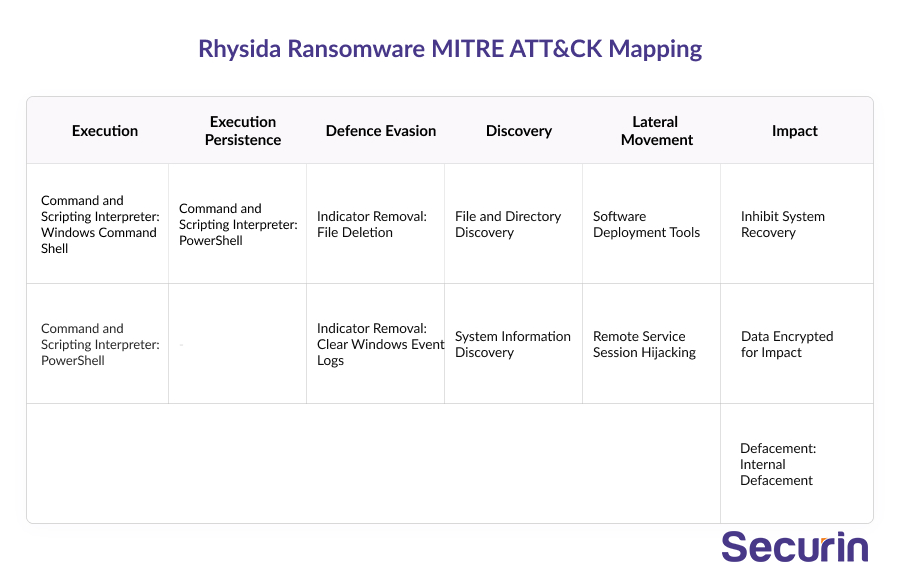
This is particularly relevant in the case of Rhysida ransomware, as its attack mapping helps organizations understand the specific techniques used by this ransomware group. With this information organizations not only gain insights into Rhysida’s attack techniques but also enhance their readiness and response capabilities against this specific threat and similar ones.
Securin Recommends
Given that the critical Zerologon vulnerability has attracted the attention of not only the Rhysida ransomware group but also the LockBit 3.0 and RagnarLocker ransomware groups in the past, it is crucial for organizations to take proactive measures. To enhance cybersecurity defenses, it is strongly advised that organizations prioritize patching the CISA KEV vulnerability to safeguard vulnerable endpoints effectively. In addition to patching known vulnerabilities, organizations are encouraged to integrate secure-by-design and secure-by-default principles into their systems and processes. By adopting these principles, organizations can proactively mitigate the impact of ransomware techniques, thereby fortifying their overall security posture and reducing the likelihood of successful cyberattacks.
