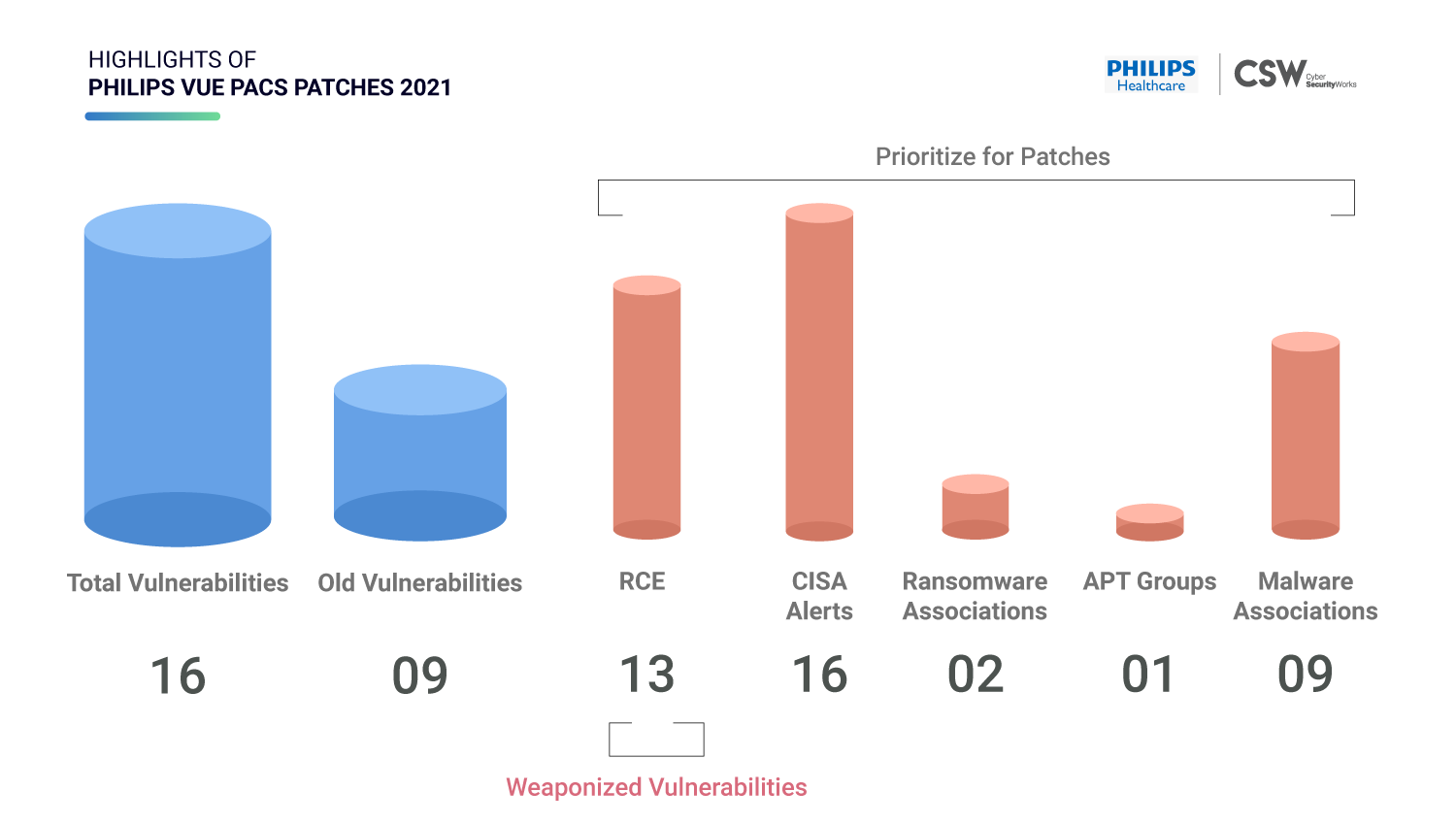
On 6 July 2021, Philips – a multinational healthcare association, released security patches for 16 serious vulnerabilities in their PACS Clinical Collaboration Platform. Picture Archiving and Communications System (PACS) software allows healthcare clinics and hospitals to digitally view MRIs, CT scans, and ultrasound images of the patients from several locations.
Storing medical images that belong to patients is an extremely sensitive process. However, the most likely reason for threat actors to break-in is that the PACS is employed as a gateway to the rest of the medical records, giving them the opportunity to shut down services and use it as a possible ransomware threat to demand money from the healthcare provider.
We analyzed 16 vulnerabilities in the Philips Vue PACS software and highlighted the ones that need to be prioritized for immediate patching.
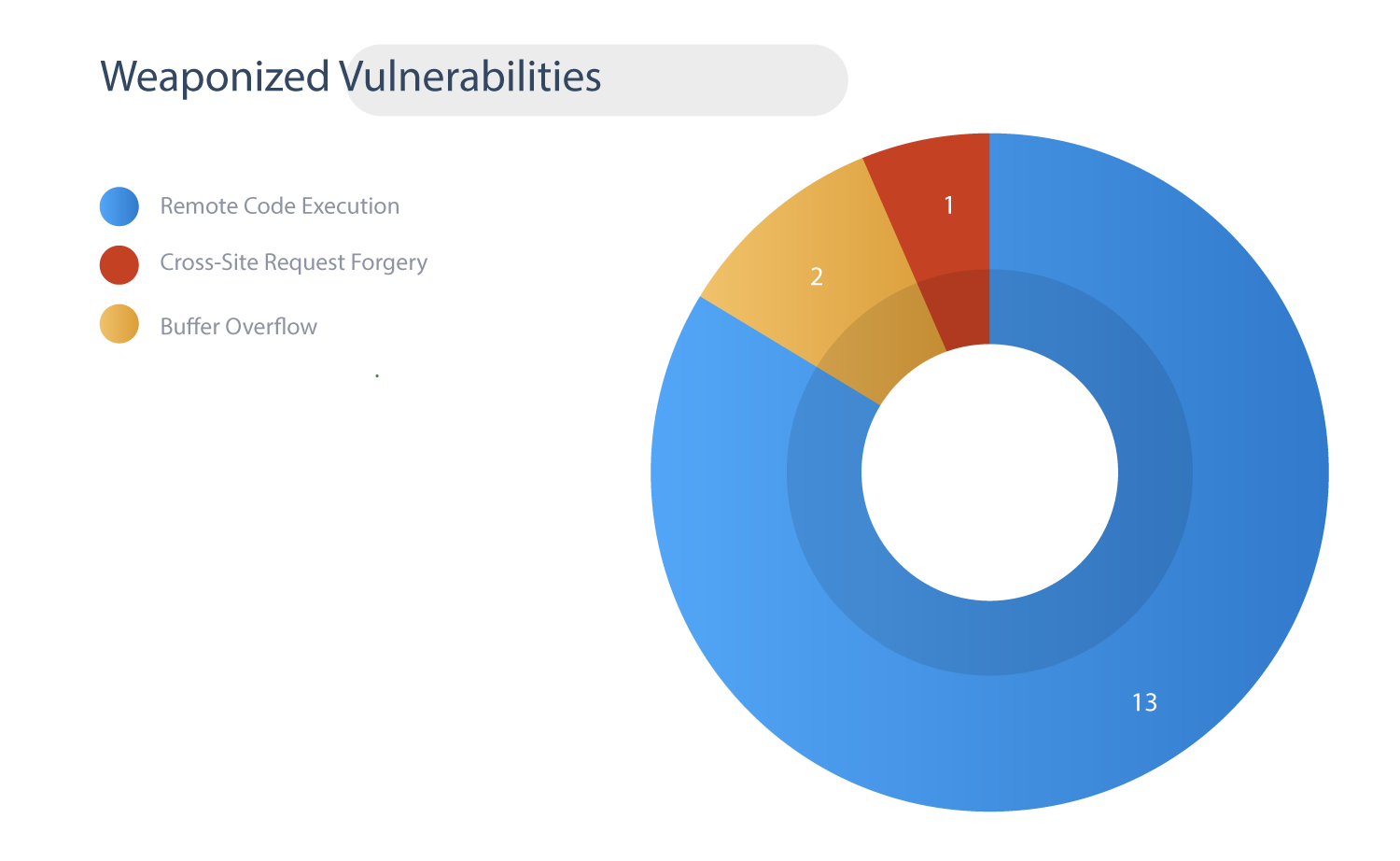
Weaponized Vulnerabilities
We have three vulnerabilities that are known exploits. Here is what we found –
-
Two CVEs are associated with Buffer Overflow and one is Remote Code Execution.
-
CVE-2018-10115 is linked to Stop ransomware.
-
All of the weaponized vulnerabilities are older ones with a CVSS v3 score ranging from 7.8 to 9.8.
-
All three CVEs have been red-flagged by CISA.
-
CVE-2018-12326 and CVE-2018-11218 have a CWE ID of CWE-119 (Improper Restriction of Operations within the Bounds of a Memory Buffer) and CWE-787 (Out-of-bounds Write) that falls under the 2020 Top 5 most dangerous software weaknesses.
-
Popular scanners such as Nessus and Qualys were able to detect these weaponized vulnerabilities.
Old Vulnerabilities
Nine Old vulnerabilities have been patched, ranging from the year 2012 to 2020.
-
Two CVEs are linked to Stop and Maze ransomware.
-
Seven CVEs are classified as RCE bugs, two are Buffer Overflow, and one is Cross-Site Request Forgery.
-
Interestingly, CVE-2015-9251 is associated with Maze ransomware, APT 1, and Malware threats (OceanSalt, Auriga, Bangat, BISCUIT, MAPIGET, TARSIP, SEASALT, KURTON, and HELAUTO).
-
These older CVEs have got a CVSS v3 score ranging from 6.1 to 9.8.
-
Eight out of nine old vulnerabilities were detected by Nessus and Qualys scanners.
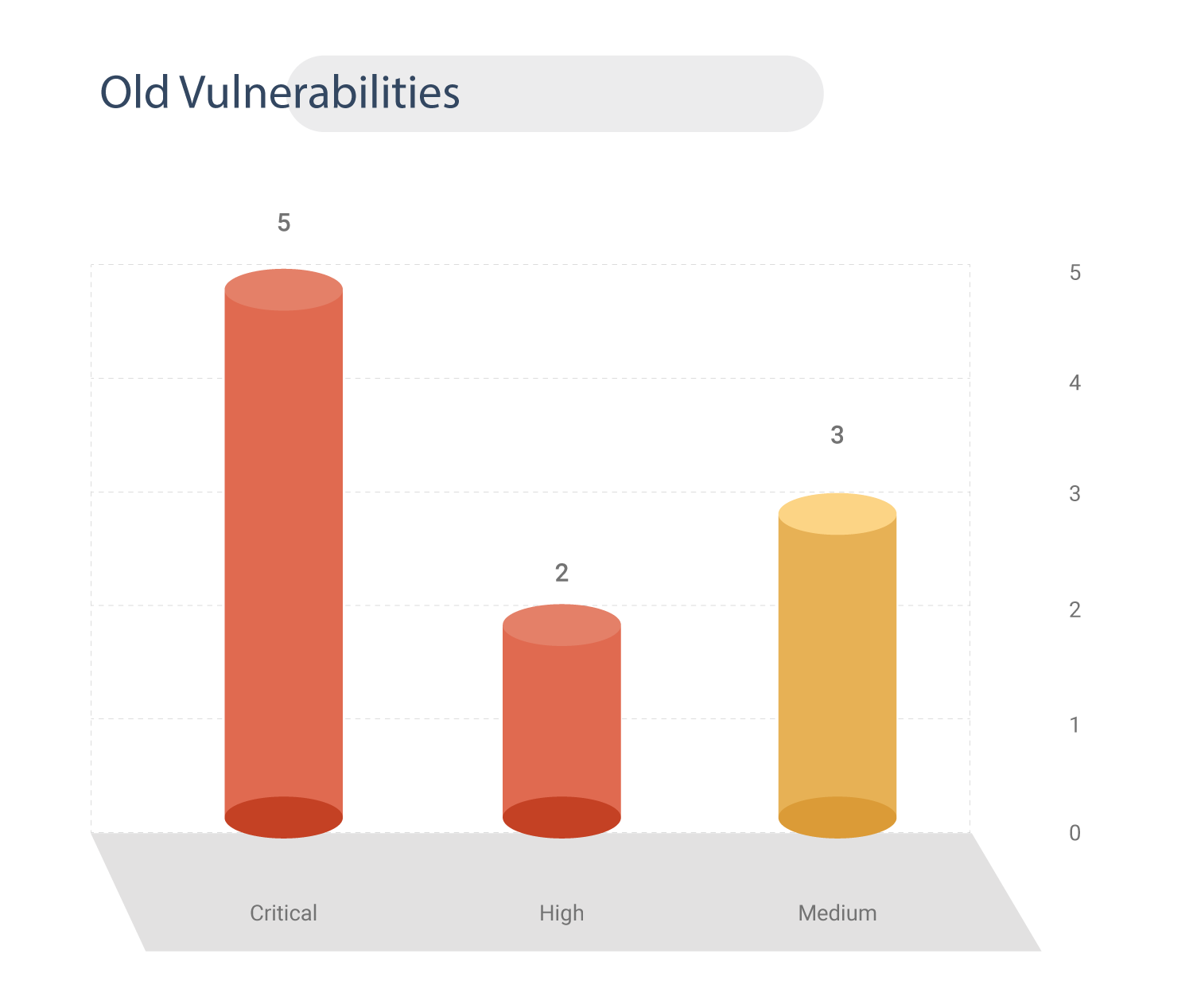
55% of these old vulnerabilities come under the category of 2020 Top 15 most dangerous software weaknesses.
CISA Alerts
On 6 July 2021, CISA issued an Industrial Controls Systems (ICS) Medical Advisory highlighting multiple vulnerabilities in Philips Vue PACS products.
An attacker can exploit these vulnerabilities to take control of an affected system and process to eavesdrop, view or modify data, gain system access, perform code execution, and install unauthorized software. Therefore, patching these vulnerabilities should be a top priority.
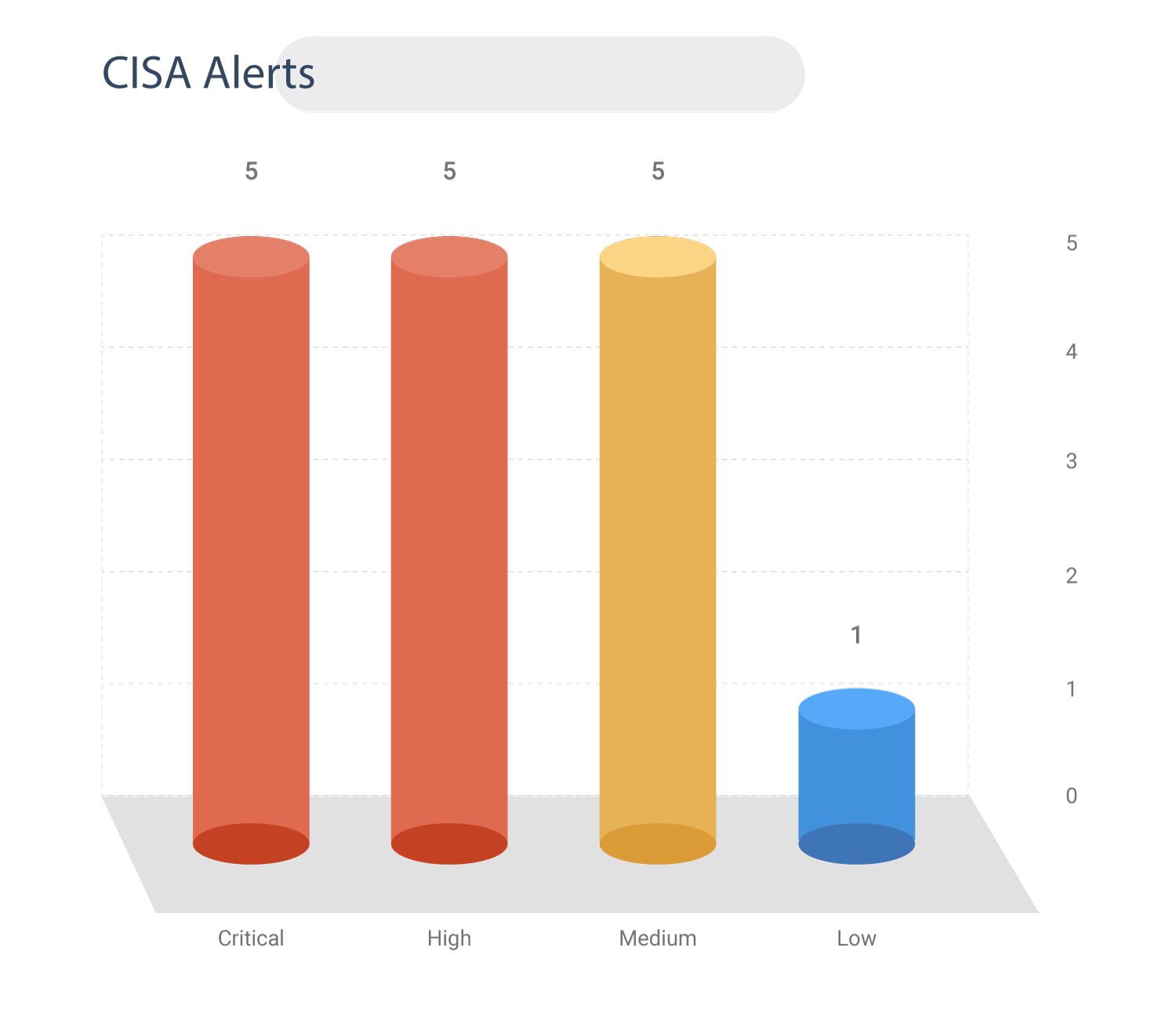
Table: Philips Vue Security Patches
As healthcare enters a new era of increased data vulnerability, radiologists should be aware that they may be working with tampered data. If pixel manipulation is suspected in the images, redundancy in datasets should be used to confirm it. Therefore, we suggest radiologists and radiology administrators include possible security measures in equipment specifications and purchase contracts.
All the Philips Vue systems prior to versions 12.2.x.x in Speech, MyVue, and PACS are affected. Therefore, we recommend Radiographers to upgrade to the newest Philips Vue PACS software, which runs on Windows Operating System 2019 and enables security patching processes to get timely security upgrades.
Need a HIPAA risk assessment?