{Update}: Pulse Secure has issued an emergency patch for six vulnerabilities in Pulse Connect Secure (PCS) system software. These vulnerabilities have Remote Code Execution capabilities and have CVSS v3 scores ranging from 7.6 to 9.1 (high to critical). Researchers have confirmed that these vulnerabilities are a bypass of the patch for CVE-2020-8260 which was fixed back in October 2020, albeit, ineffectively. Hence, we encourage all Pulse Secure users to update to the latest version of 9.1R12.
On April 15th, CISA issued an alert to organizations about Pulse Secure vulnerabilities being used to disrupt critical services in the United States. In a joint statement, organizations such as the NSA, FBI, and CISA called out five vulnerabilities. One was a popular weakness in Pulse Secure and was discovered in 2019. Till date, 388 devices worldwide are vulnerable to this weakness. Check out more about this in our blog here.
New Vulnerability Found in Pulse Connect Secure:
On May 14, 2021 a high severity vulnerability (CVE-2021-22908) was identified in Pulse Connect Secure with a buffer overflow weakness, which allows an attacker to execute code as a user with root privileges. This vulnerability affects PCS versions 9.0Rx and 9.1Rx and has been accredited a CVSS V3 score of 8.5. To resolve this situation, Pulse Secure has issued an out-of-cycle patch and a workaround to mitigate the affected versions.
In this Patch Watch edition, CSW researchers analyzed 93 security vulnerabilities in 16 Pulse Secure products and spotlight what weaknesses need to be addressed immediately and why.
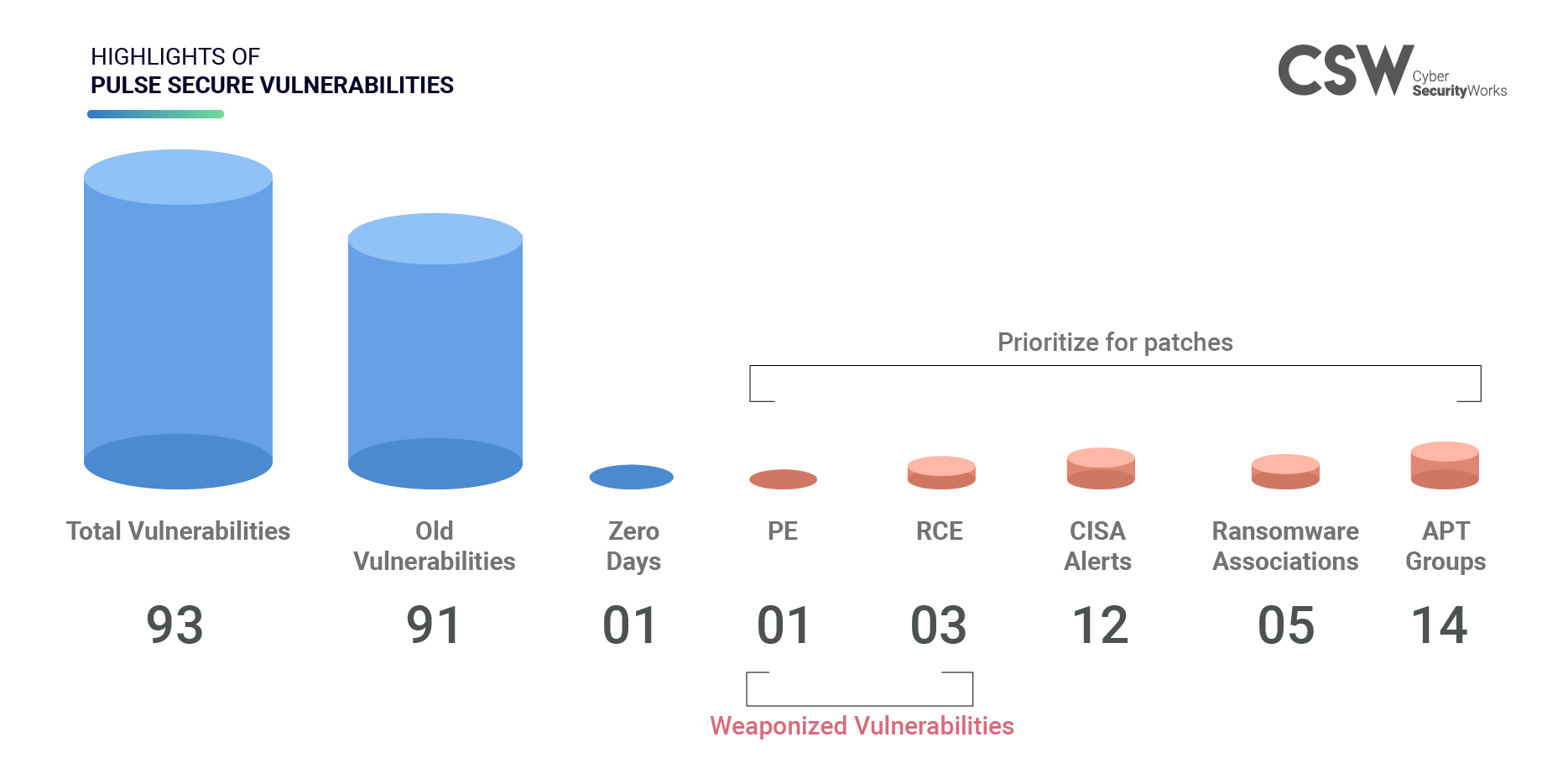
Weaponized Vulnerabilities
Remote Code Execution (RCE) is the most severe type of vulnerability as they allow threat actors to remotely deploy code leading to the execution of additional malware payloads. We identified three CVEs as RCE bugs (CVE-2019-11510, CVE-2019-11539, CVE-2020-8260) with a CVSS V3 score ranging from 6.5 – 10 (high – critical), and one CVE has PE capabilities with a CVSS V3 score of 1.9 (low).
CVE-2019-11510 that exists in Pulse Connect Secure with a CVSS V3 score of 10 (critical) was found to be trending lately. This arbitrary file reading vulnerability is capable of enabling unauthenticated threat actors to access private keys and user passwords. Interestingly we red-flagged this vulnerability in our Cyber Risk in VPNs in 2020.
CVE-2019-11510, CVE-2019-11507, and CVE-2019-11539 are connected to five ransomware strains (Sekhmet, Mailto, Maze, Sodinokibi, Black Kingdom) and 14 APT Groups (TA2101, APT1, APT29, Anonymous, AnonSec, FIN6, Pinchy Spider, GOLD SOUTHFIELD, APT29, APT33, APT34, APT39, APT41, APT5) leading to hijack of a system or remote tampering into critical organizations.
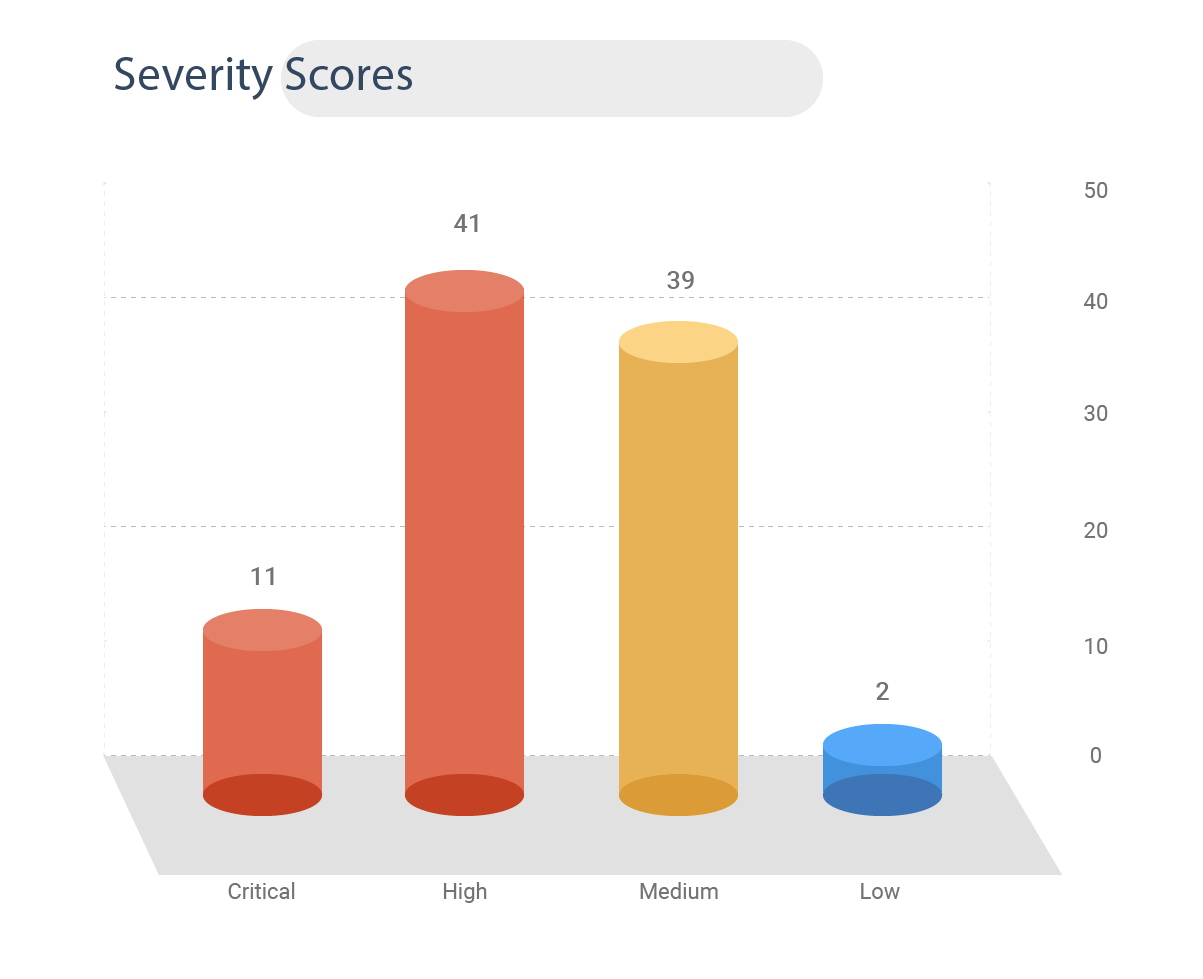
Severity Scores
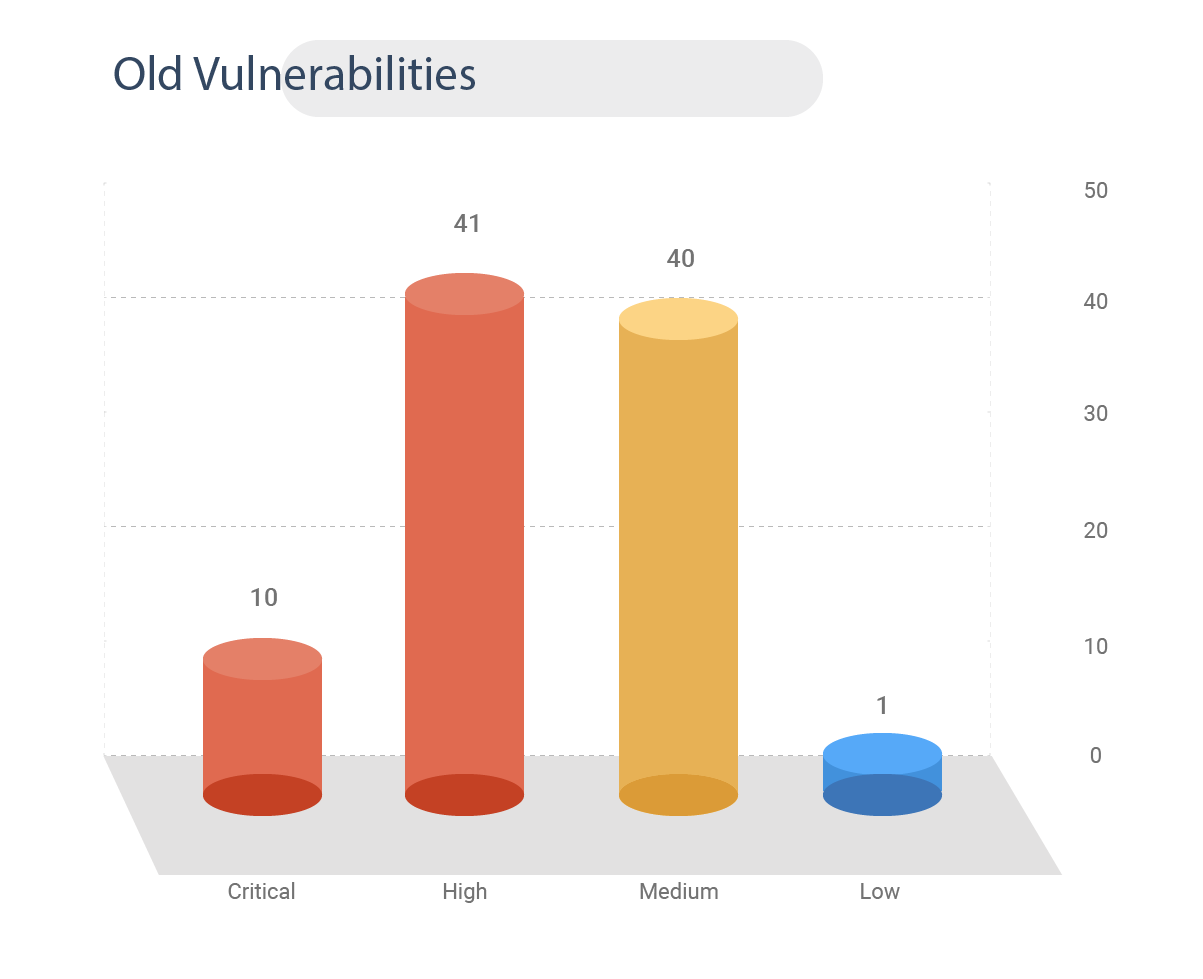
Old Vulnerabilities
99% of the vulnerabilities are older weaknesses ranging from the year 2016 – 2020. All the seven weaponized vulnerabilities are old weaknesses. Therefore, patching these vulnerabilities on priority is essential.
Zero-Days
A recent zero-day (CVE-2021-22893) found in Pulse Connect Secure product, got the CVSS V3 score of 10 (critical), is being actively exploited in the wild by hackers. We urge Pulse Secure VPN users to patch this newly disclosed vulnerability that allows an unauthenticated user to perform remote arbitrary file execution on the Pulse Secure Connect gateway.
CISA Alerts
11 CVEs have been red-flagged by CISA and worryingly, two CVEs in Pulse Connect Secure plus and one CVE in Steel-Belted Radius remain unpatched, and seven CVEs are marked as high severity.
On 21 July 2021, CISA has issued an alert disclosing their findings on 13 malware samples related to exploited Pulse Secure devices.
CWE Analysis
Based on Common Weakness Enumeration, 17 CVEs have been categorized under CWE-79 (Improper Neutralization of Input During Web Page Generation) – a weakness category that ranks number 1 CWE on MITRE’s Top 25 dangerous CWEs.
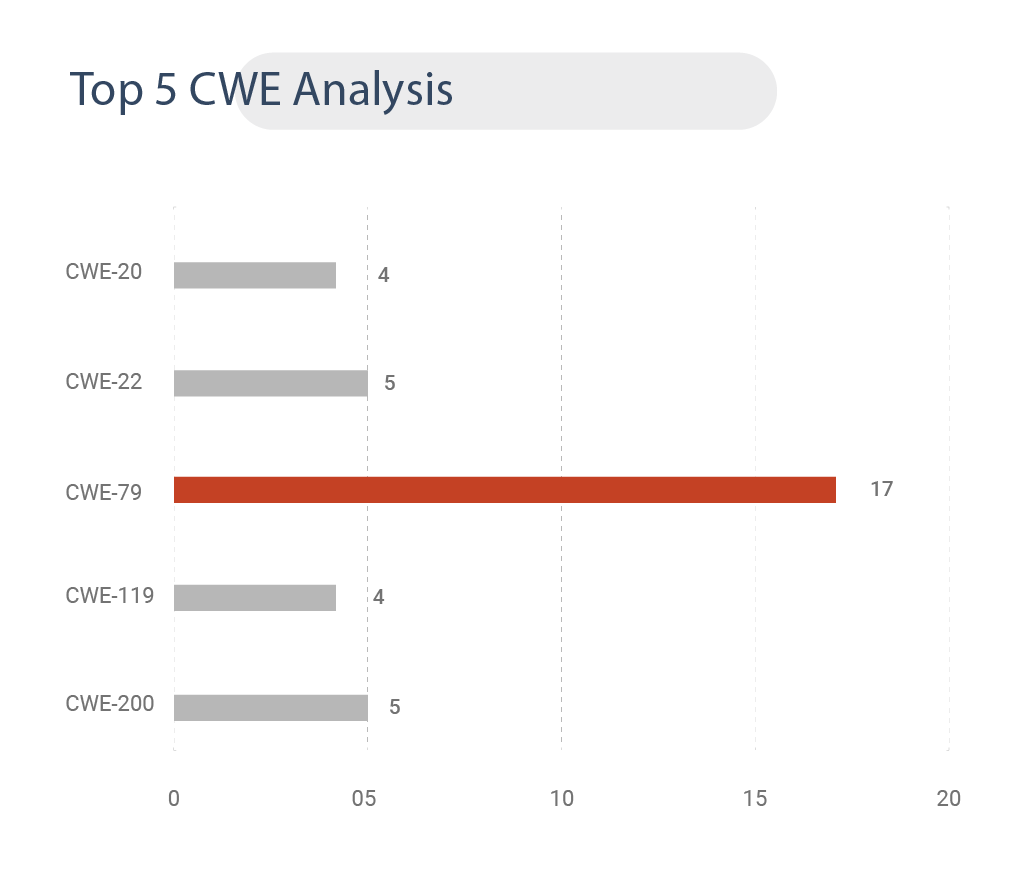
Table: Patches for Pulse Secure Vulnerabilities
A new Pulse Connect Secure Integrity Tool has been released to help customers check if they are vulnerable to Pulse Secure weaknesses. Organizations are recommended to implement the guidelines affirmed by Pulse Secure and provide a strong password to all VPNs. We also urge you to apply the latest patches for all the Pulse Connect Secure products, which is version 9.1R11.4.
Out of 93 vulnerabilities, patches for 80 vulnerabilities is available. We urge you to patch them on priority and watch this space for more Patch Watch blogs”
Related Blogs:
NSA Validates CSW’s warning on two critical vulnerabilities
Vulnerable to Cyber Breaches?
