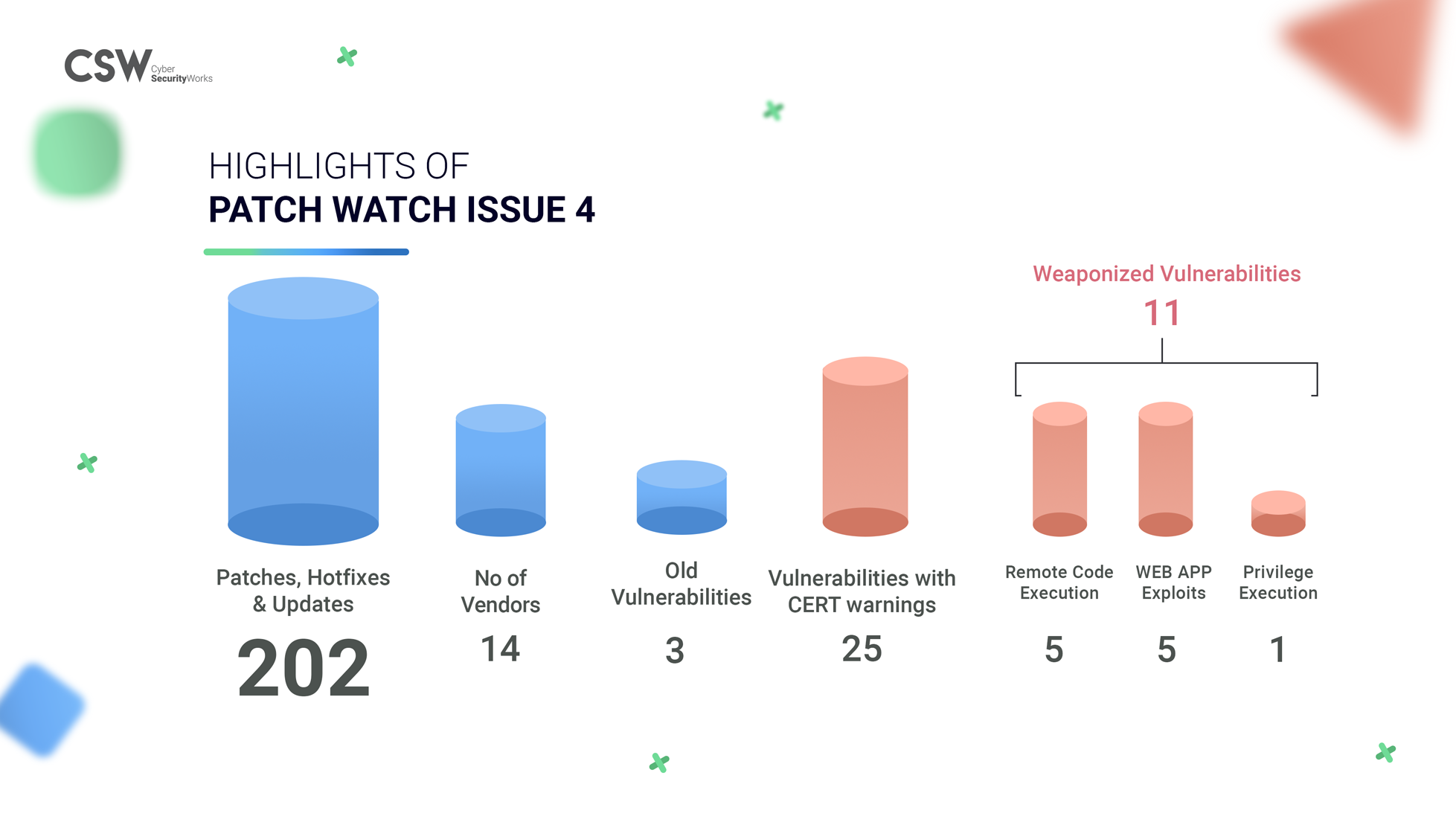
In this issue we have –
1. Microsoft plugged 87 bug fixes –
-
11 vulnerabilities were rated critical, 75 are high, and one is of medium severity.
-
These patched vulnerabilities include wormable TCP/IP with RCE flaws.
- None of these fixed vulnerabilities are currently being exploited, though six of them were previously publicly known.
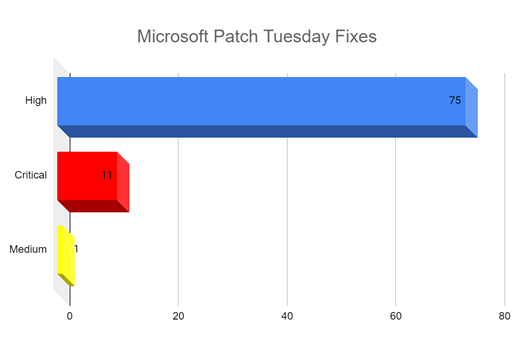
Table 1: Microsoft’s 11 critical vulnerabilities and their fixes
2. Our analysis of the 202 patched vulnerabilities shows us that there are –
- 54 Hotfixes, 17 Patches and, 131 Updates in this week
- 191 vulnerabilities are yet to be weaponized.
- 11 vulnerabilities have known exploits and are weaponized.
- 5 CVE’s are associated with Remote Code Evaluation (RCE) and allows attackers to execute arbitrary code with elevated privileges.
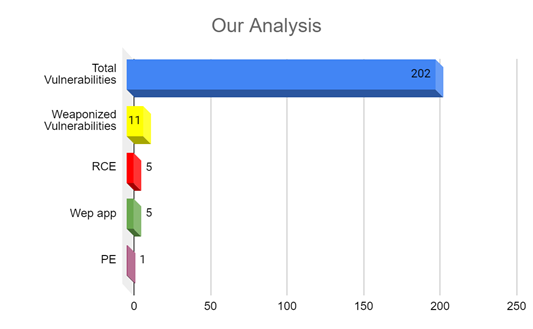
- Incidentally 5 CVEs from Checkpoint that have WEBAPP exploits have been fixed. Command injection flaws are often exploited by threat actors therefore patching these would be optimum.
- CVE-2020-14028 has Privilege Execution capabilities in which attackers can gain elevated access to resources that are typically protected. Click here for the patch.
3. This week only 3 CVEs are old vulnerabilities (out of 202), ranging from 2018 and 2019.
- CVE-2018-12463 is a web app exploit with a CVSS Score of 7.5 rating High severity.
- CVE-2019-19242 is a vulnerability in IBM Security Guardium with a CVSS v3 score of 5.9.
- CVE-2019-19705 is a vulnerability that exists in Realtek HD Audio Driver Package (deployed on PCs containing Realtek sound cards).
4. 25 vulnerabilities have been exploited by intruding more than 100 companies across the world, ranging from software vendors, video gaming companies, telcos, and more. A group of five hackers (APT41) sponsored by the Chinese state has been accused and filed charges by the US Government.
Table 2: 25 Vulnerabilities Exploited by (APT41) Group
In recent weeks, each vendor has been keeping a watchful eye on their flaws and have been releasing updates to ensure they are patched before they get weaponized. You can download all weaponized vulnerabilities that we have summarized above and patch them immediately.
Table 3: Weaponized Vulnerabilities
Vulnerabilities that are trending today were once overlooked and their patches missed. Today, the same vulnerabilities are being exploited to deliver ransomware and malware. Weaponized or not, it’s essential to cyber hygiene to patch all vulnerabilities.
Table 4: Vulnerabilities yet to be Weaponized
Happy Patching!
