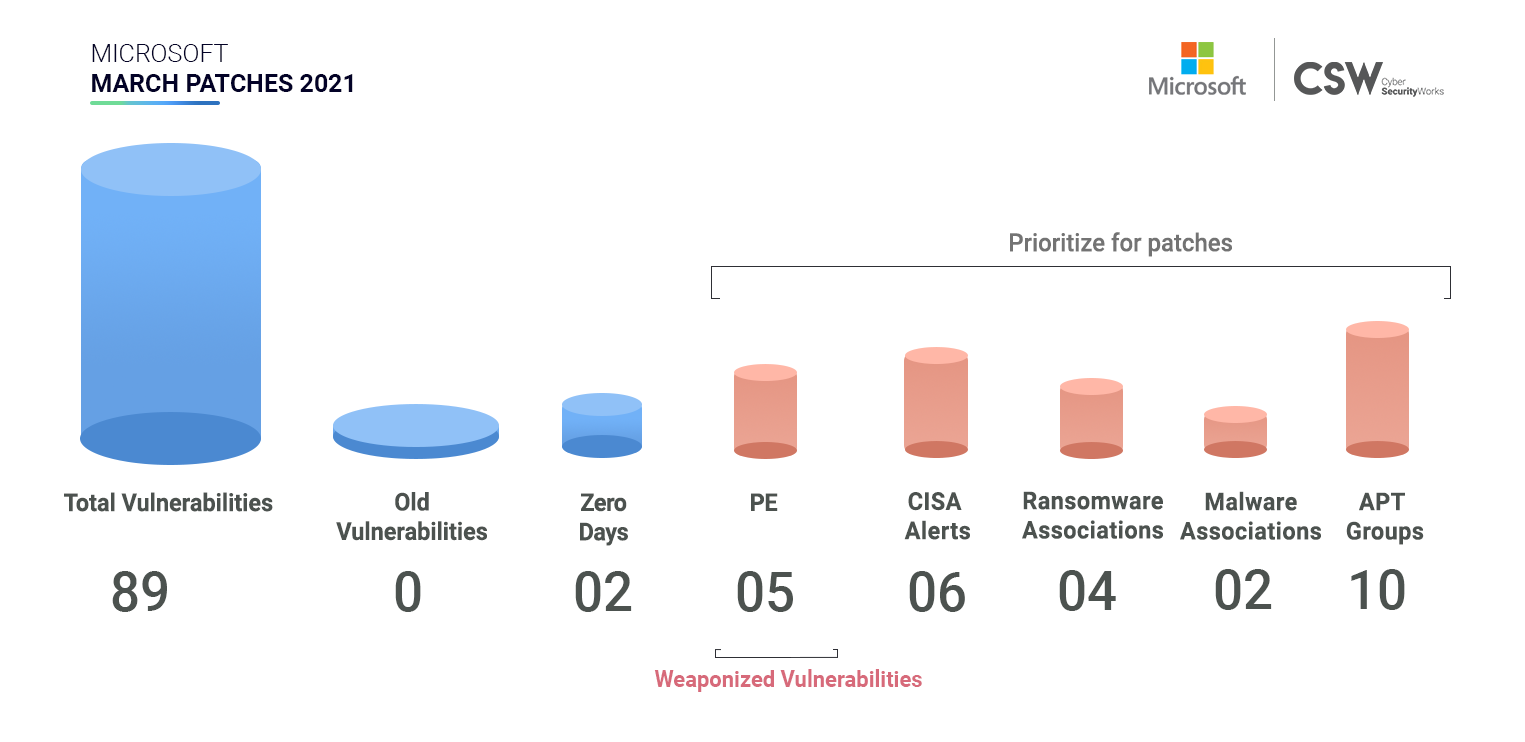
Microsoft patched 89 unique security vulnerabilities in March 2021. We analyzed these weaknesses and spotlighted important vulnerabilities that ought to be patched on priority.
Microsoft’s March Patches Overview
In March, Microsoft patched 89 vulnerabilities discovered in 2021 –
RCE/PE: Remote Code Execution and Privilege Execution are two of the most dangerous weaknesses that are most exploited by malicious actors. Microsoft has fixed –
-
45 CVEs that have been classified as RCE bugs
-
30 CVEs have Privilege Escalation capabilities
-
4 CVEs are linked to Denial of Service
Notably four CVEs (CVE-2021-27065, CVE-2021-26855, CVE-2021-26863, CVE-2021-21300) have publicly known exploits therefore patching them would be essential.
Zero Day Vulnerabilities: Microsoft has released out-of-band patches for four Zero Day Vulnerabilities ( CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, and CVE-2021-27065).
These weaknesses exist in Microsoft exchange server and have been associated with Hafnium, Winnti Group, Tick, LuckyMouse, Websiic, Calypso, Tonto Team, Mikroceen, and Vicious Panda APT group.
These CVEs are also being exploited by DearCry Ransomware and are being delivered through PlugX and ShadowPad malware.
CISA Alerts
Six CVEs have featured in recent CISA alerts (CVE-2021-26869, CVE-2021-27065, CVE-2021-26857, CVE-2021-26855, CVE-2021-26858, CVE-2021-26867)
These CVEs have been red flagged by security agencies primarily because these vulnerabilities are associated with DearCry ransomware and APT groups (Hafnium, Winnti Group, Tick, LuckyMouse, Websiic, Calypso, Tonto Team, Mikroceen -Vicious Panda Group) are exploiting it to mount cyber attacks.
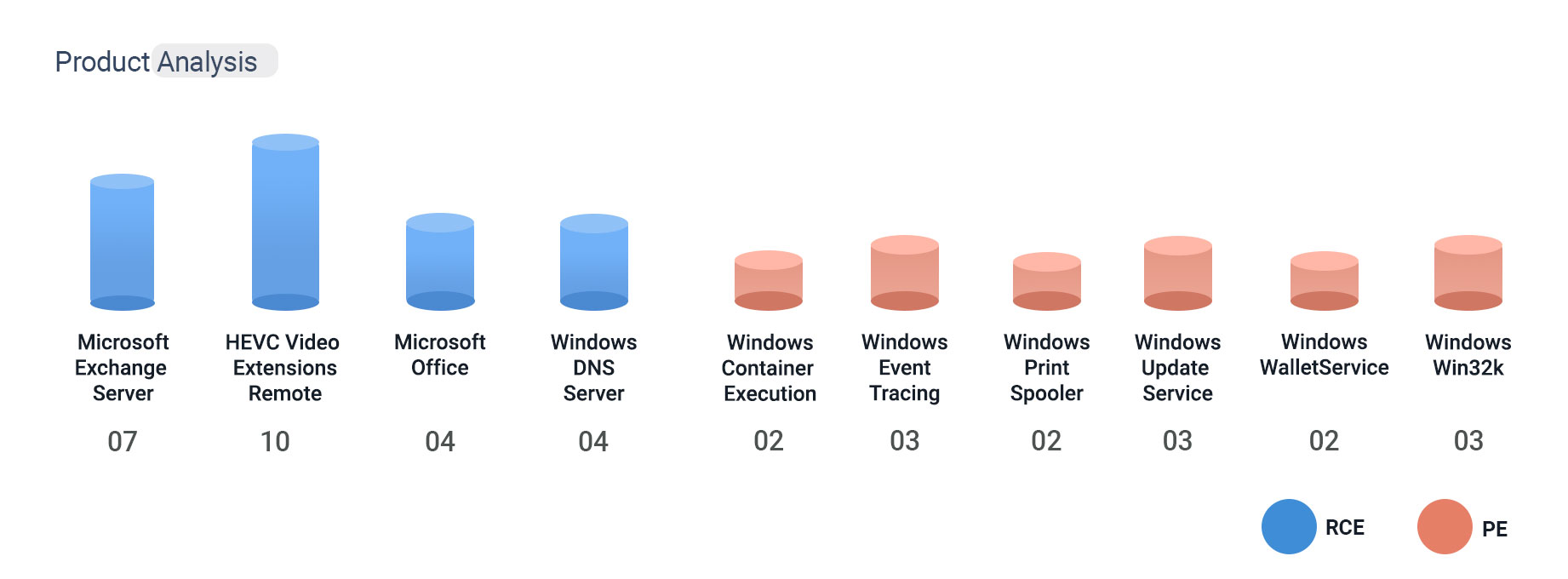
Product Analysis
Patches are released for 47 different Microsoft products.
Severity Scores
Table: Microsoft March Patches 2021
Newly discovered vulnerabilities are fast becoming weaponized and are becoming arsenal for ransomware families and APT groups. Prioritize your patching and shrink your attack surface.