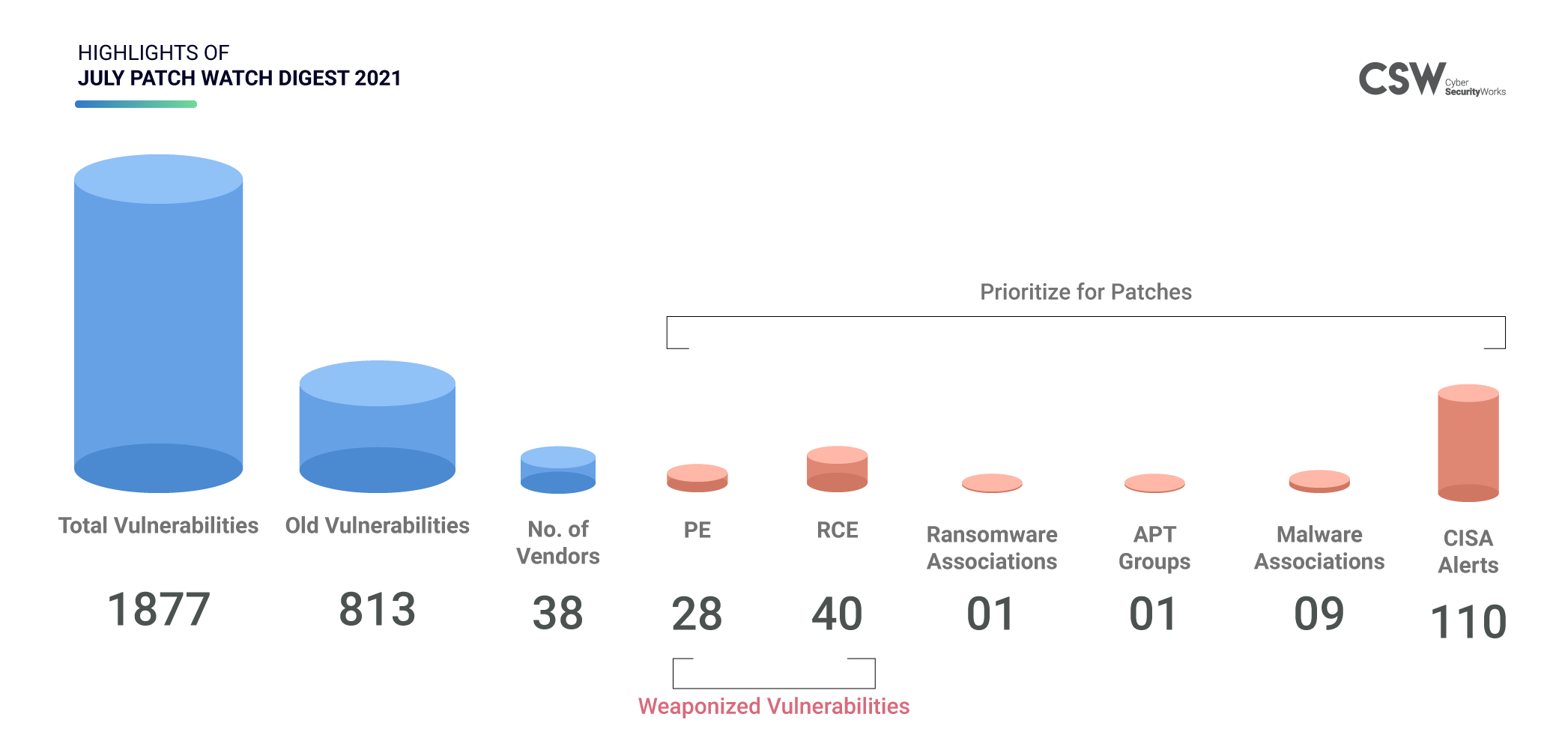
Highlights of July Digest
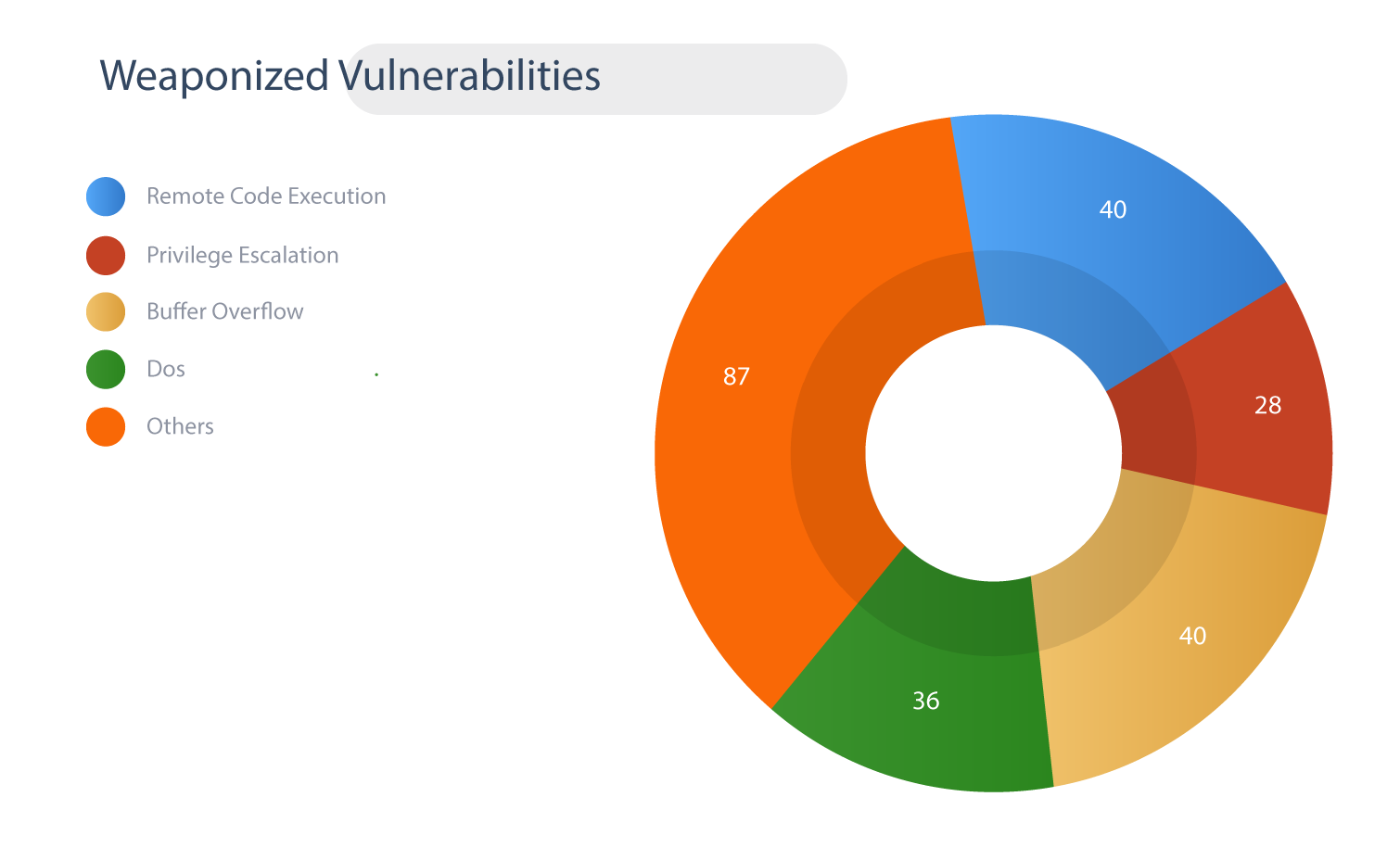
Weaponized Vulnerabilities
We have 231 vulnerabilities that are known exploits. Here is our analysis –
-
4 CVEs are associated with Maze Ransomware, APT 1, and 9 Malwares (OceanSalt, Auriga, Bangat, BISCUIT, MAPIGET, TARSIP, SEASALT, KURTON, and HELAUTO).
-
40 CVEs are classified as Remote Code Execution.
-
28 CVEs have Privilege Escalation capabilities.
-
40 CVEs with Buffer Overflow.
-
36 CVEs are linked to Denial of Service.
-
87 CVEs fall into other categories.
-
Of these 231 CVEs, seven are alerted by CISA.
-
29 CVEs are rated critical and 73 are of high severity.
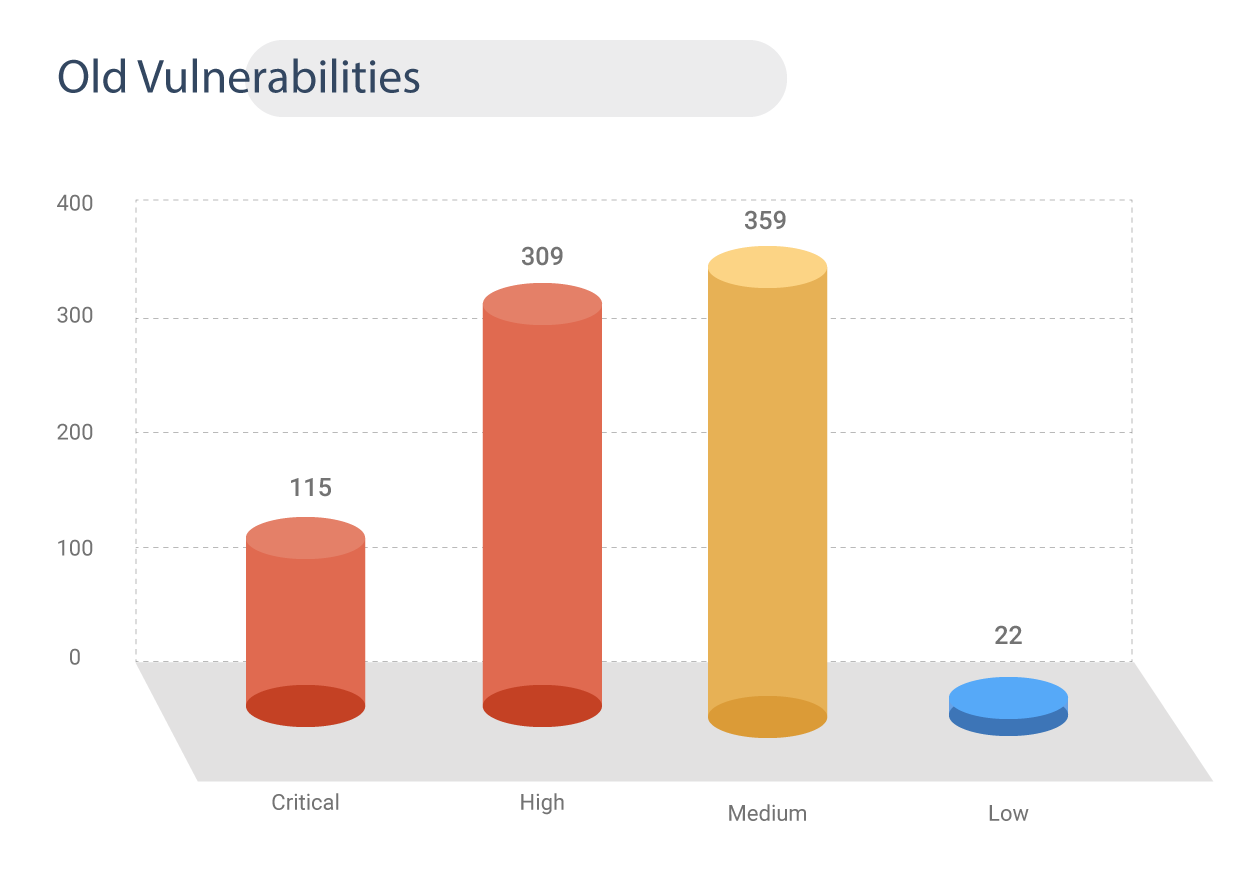
Old Vulnerabilities
Security updates for 813 old vulnerabilities (ranging from 2008 to 2020) have been released.
-
7 CVEs are associated with Maze Ransomware, APT 1, and 9 Malwares (OceanSalt, Auriga, Bangat, BISCUIT, MAPIGET, TARSIP, SEASALT, KURTON, and HELAUTO).
-
156 CVEs have publicly known exploit code.
-
18 CVEs are Remote Code Execution bugs.
-
18 CVEs are classified as Privilege Escalation.
-
35 CVEs have been alerted by CISA.
-
115 CVEs are rated critical and 309 are of high severity.
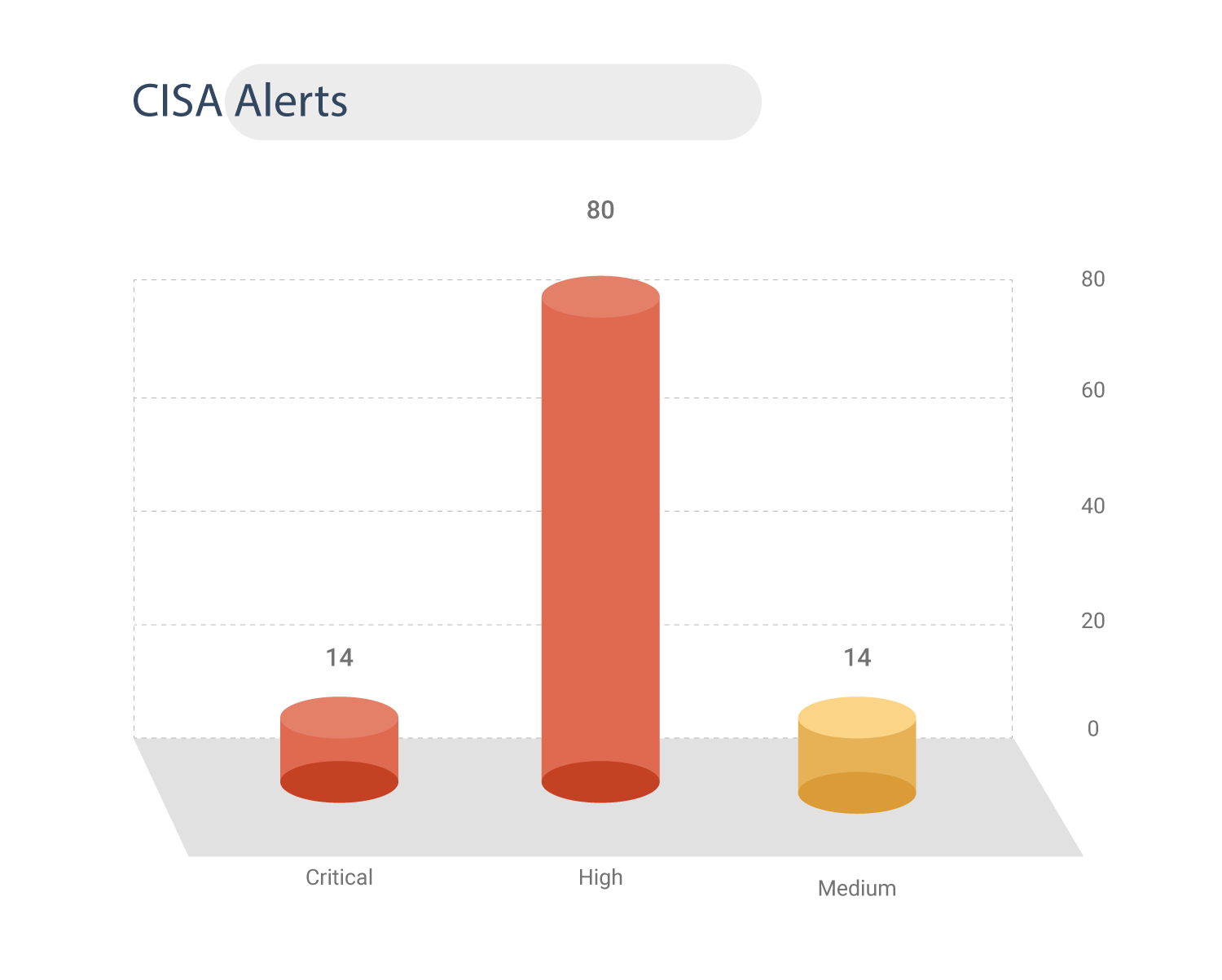
CISA Alerts
CISA has issued alerts for 110 vulnerabilities, including 14 publicly known exploits.
-
2 CVEs are associated with Maze Ransomware, APT 1, and 9 Malwares (OceanSalt, Auriga, Bangat, BISCUIT, MAPIGET, TARSIP, SEASALT, KURTON, and HELAUTO).
-
4 CVEs are classified as Remote Code Execution bugs.
-
3 CVEs with Privilege Escalation.
-
14 CVEs are rated critical and 80 are of high severity.
Oracle July Critical Patch Update 2021
Oracle plugged 342 security vulnerabilities in July.
-
57 CVEs have publicly known exploits.
-
49 CVEs are rated critical.
-
16 CVEs have been alerted by CISA.
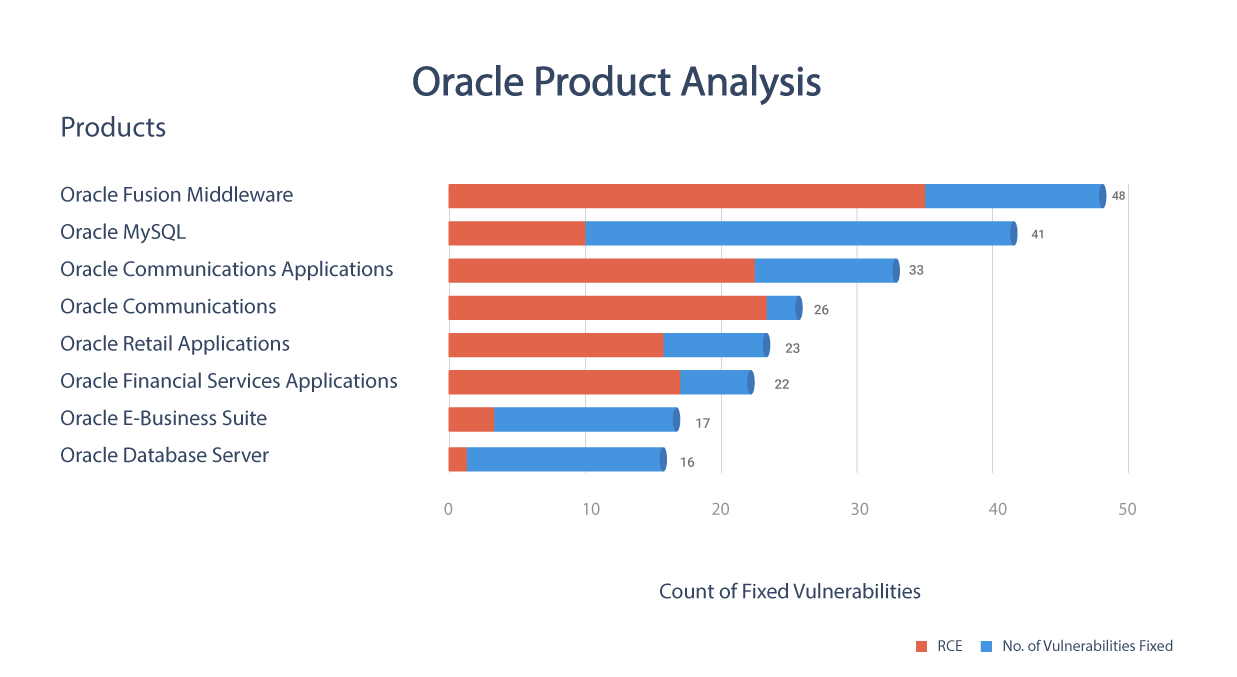
Check out our Oracle Critical Patch Update edition here.
Microsoft July Patches 2021
Microsoft fixed 117 security vulnerabilities, including nine zero-days.
-
43 CVEs classified as RCE bugs.
-
1 CVE is alerted by CISA.
-
13 are of high severity.
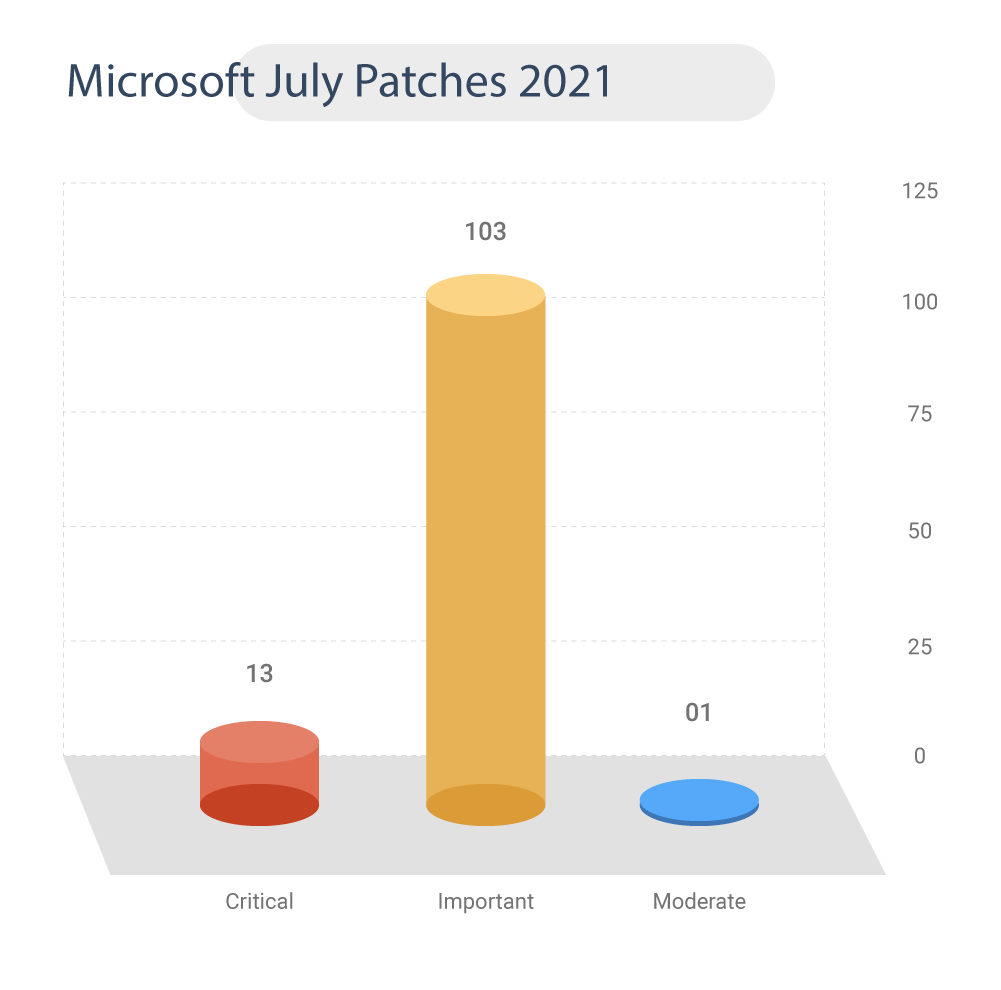
Check out our Microsoft patch watch edition here.
Table: July Security Patches 2021
We noticed 32% of the weaponized vulnerabilities discovered in 2021 were patched in July. The rate at which attackers release exploit code is rising all the time. Sometimes, however, the window of opportunity from the time a vulnerability is disclosed publicly to just before an attack hits is too short for patching to be feasible. Therefore, we recommend users to patch all July security vulnerabilities before malicious actor exploits.
Does your organization have a patch management program? Talk to CSW’s Experts to prioritize the threats that need immediate attention!