Highlights of January Digest
-
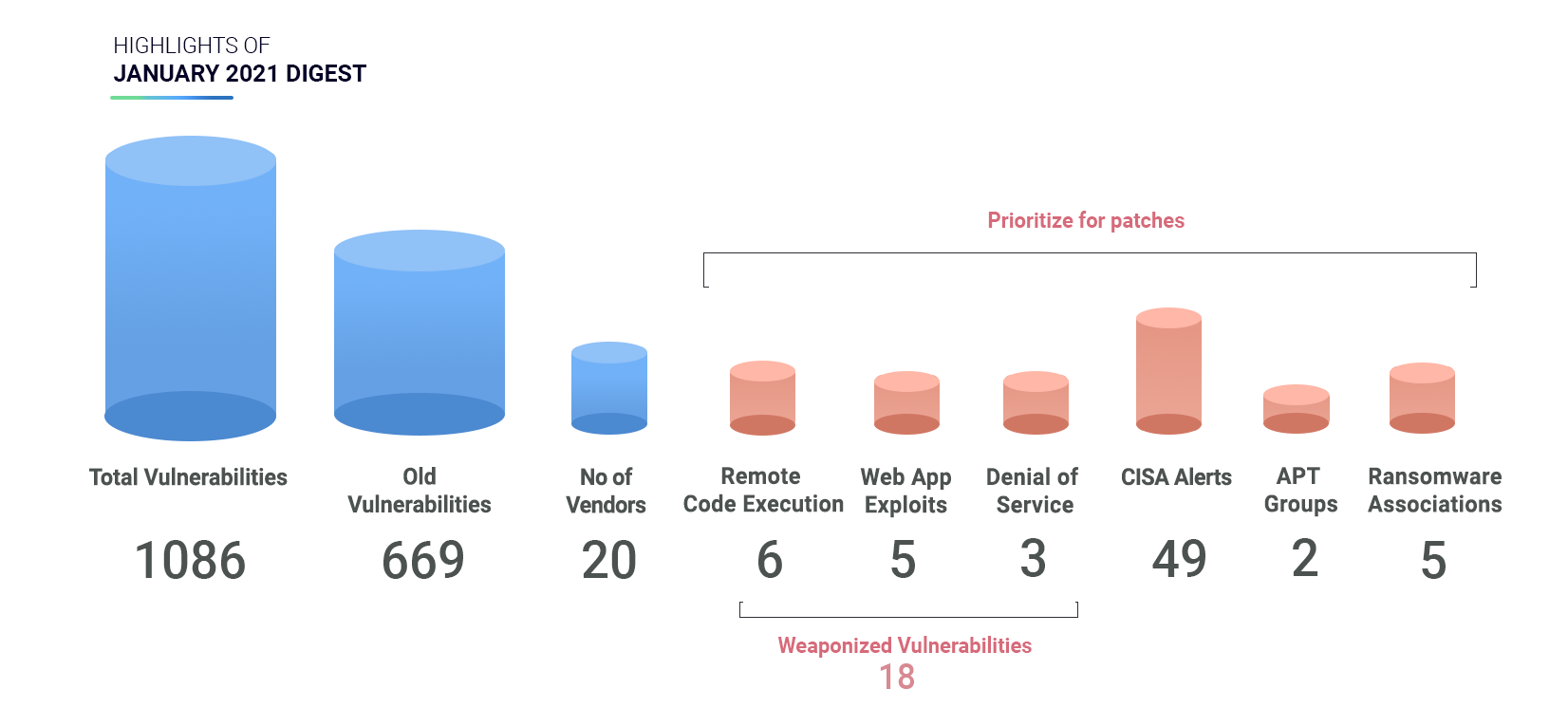
20 vendors released security updates for 1086 vulnerabilities. 18 CVEs had publicly known exploits.
-
49 vulnerabilities that got patched featured in CISA alerts.
Weaponized Vulnerabilities
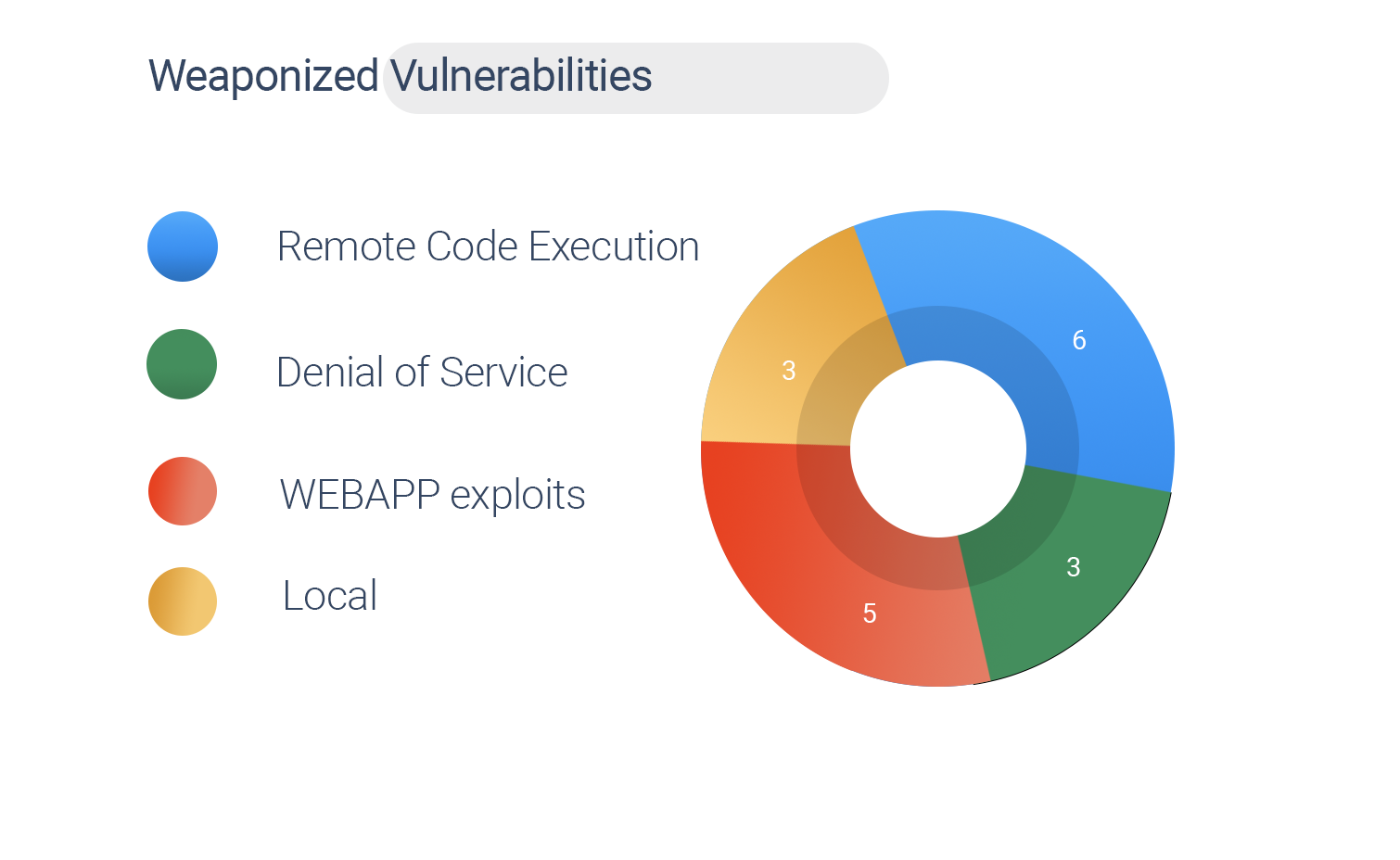
We have 18 vulnerabilities that are publicly known exploits, with 6 CVEs rated critical, 7 are high, and 5 of medium. Here is our analysis –
-
2 CVEs are linked with 3 ransomware families.
-
2 CVEs are associated with APT Groups.
-
6 CVEs are associated with RCE bug.
-
2 CVEs were alerted by CISA.
-
5 CVEs are webapp exploits.
-
3 CVEs with Denial of Service.
-
3 CVEs are local exploits.
Click here for our analysis and download patches.
Microsoft Patches for January 2021
Microsoft released security patches for 83 vulnerabilities.
-
10 CVEs are rated critical and 73 are high.
-
CVE-2021-1647 is a zero-day exploit with RCE capabilities.
-
This vulnerability existed within the Microsoft Malware Protection Engine version 1.1.17700.4 or later, a core component of Microsoft Defender that addresses malicious software.
-
Microsoft also patched a publicly disclosed Microsoft splwow64 Elevation of Privilege vulnerability tracked as CVE-2021-1648, which was previously disclosed by Google Project Zero in September 2020 under CVE-2020-0986.
Click here for our analysis and download patches.
Oracle Patches for January 2021
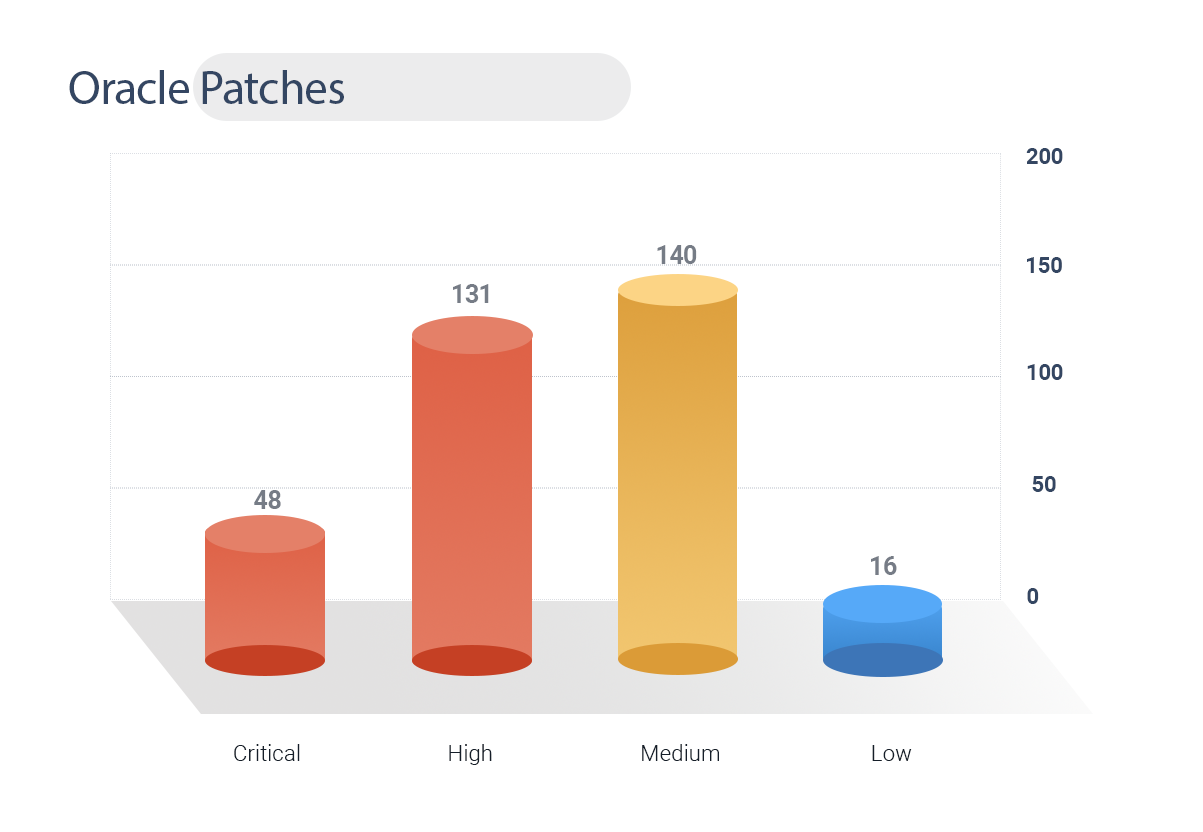
Oracle rolled out security patches for 329 vulnerabilities.
-
January 2021 critical patch update fixes included CVE-2020-14750, an exploited vulnerability in WebLogic Server, which Oracle addressed with the release of an out-of-band update.
-
4 CVEs are known exploits.
-
48 CVEs are rated critical and 131 are high.
Click here for our analysis and download patches.
Product Based Analysis
We further analyzed Microsoft patches based on the product and found that – Out of 83 CVEs, 23 have RCE and 32 have PE capabilities.
When Oracle products were analyzed, 171 CVEs were associated with RCE flaws out of 329.
Table 1: Product Analysis
Old Vulnerabilities Patched in January 2021
669 Old vulnerabilities have been issued security updates ranging from the year 2013 to 2020.
-
5 CVEs are associated with five different ransomware families such as BitPaymer, Petya, Cerber, DoppelPaymer, and Redkeeper.
-
2 CVEs are linked to Lazarus and Kelvin SecTeam APT Group.
-
17 CVEs are known exploits.
-
24 CVEs are issued an alert by CISA.
-
CVE-2017-5638 – This RCE vulnerability exists in Apache given the CVSS Score of 10(critical) and CWE – 20, which tops 3 in the Top 25 Common Weakness Enumeration. This CVE is associated with the Lazarus APT group and Ceber ransomware.
-
CVE-2019-0708 is an RCE bug that exists in Microsoft provided the CVSS Score of 10 and CWE – 416, which topped 8 in Top 25 Common Weakness Enumeration. This is also associated with Kelvin SecTeam APT Group and DoppelPaymer and Redkeeper ransomware.
-
70 CVEs are rated critical, and 144 are high.
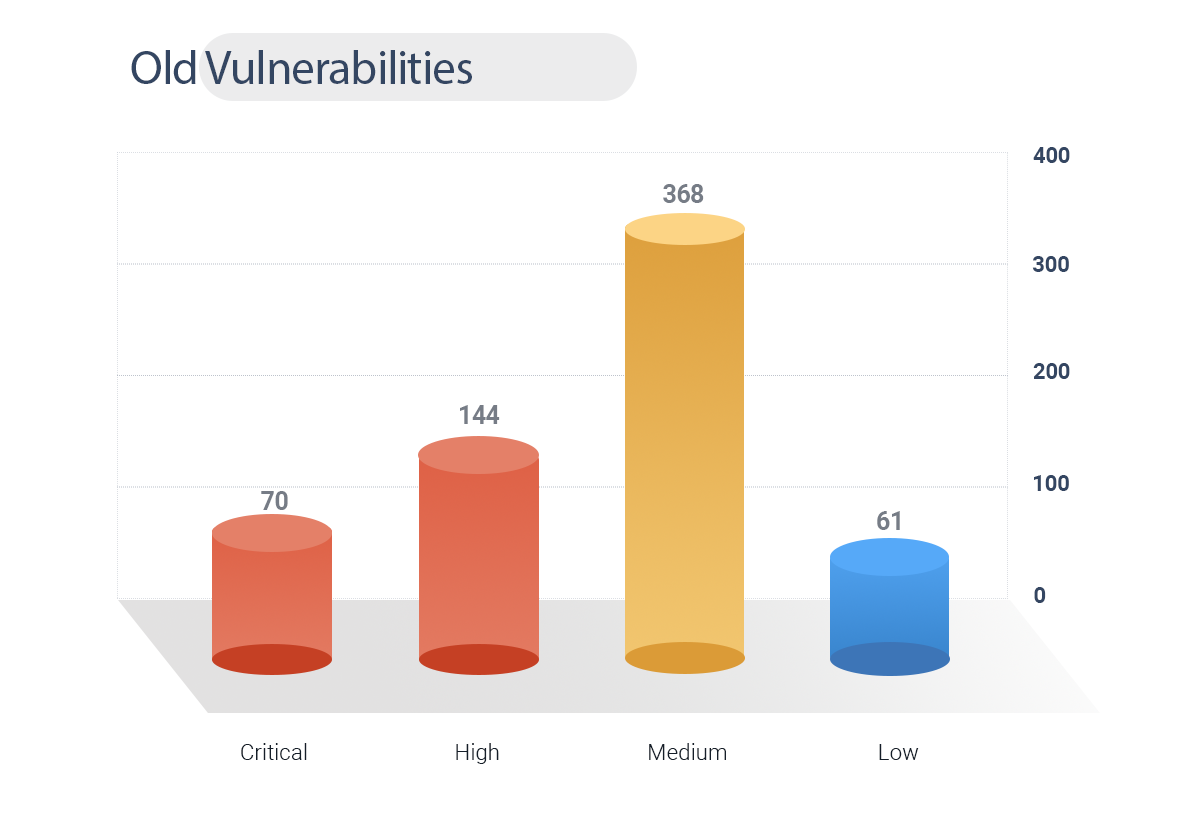
Old vulnerabilities are still a problem to everyone that raises stakes to ransomware attacks. From the above analysis of vulnerabilities, out of 18 known exploits, 17 comes under old vulnerabilities, which also includes 5 ransomware associations and 2 APT Groups. This clearly proves that old vulnerabilities potentially fall target to ransomware attacks and massive disruptions.
Therefore, it is necessary to prioritize the unpatched old security vulnerabilities first and ensure all the systems have the latest patches.
Click here for our analysis and download patches.
CISA Alerts
CISA issued a warning alert for 49 vulnerabilities.
-
1 CVE is associated with the Kelvin SecTeam APT Group.
-
1 CVE with DoppelPaymer and Redkeeper ransomware families.
-
2 CVEs are Known exploits.
-
2 CVEs are rated critical and 2 are high.
Click here for our analysis and download patches.
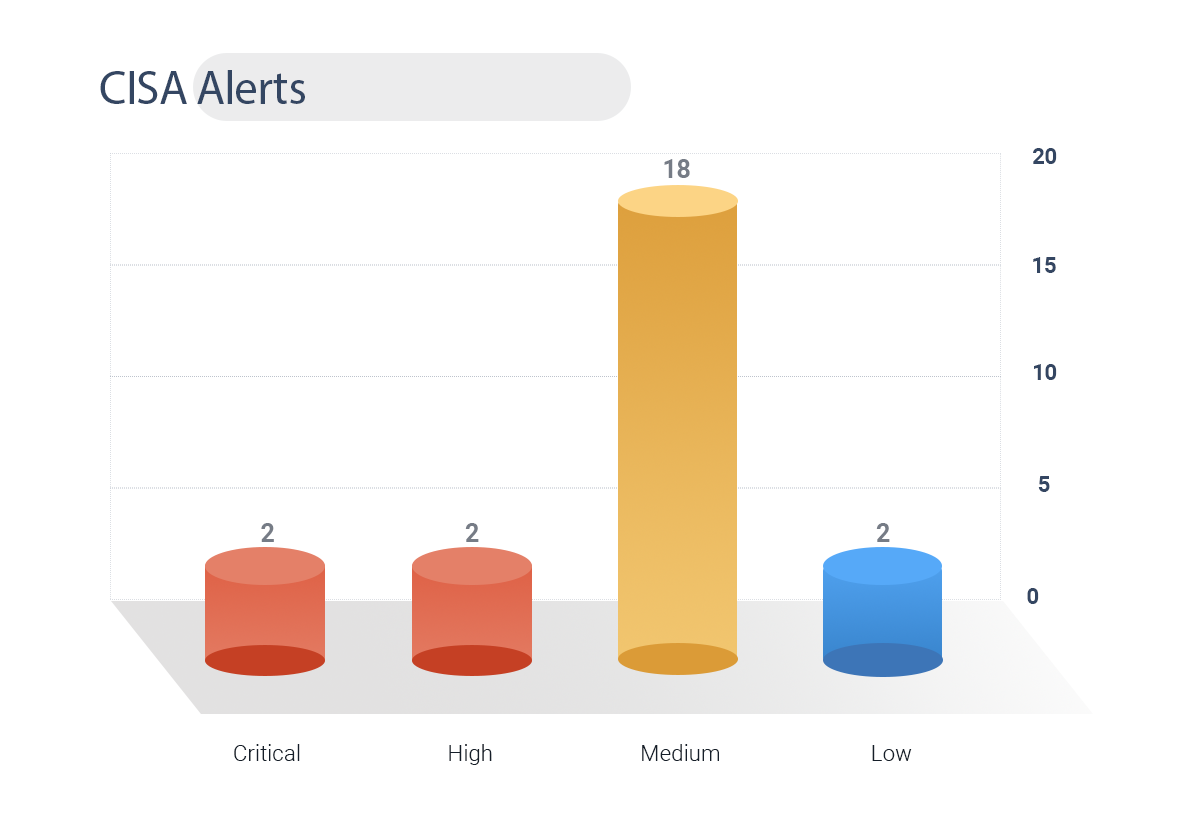
Table 2: January 2021 Security Patches
Patching is vital. Organizations today face the trade-off between speed and perfection. It has become unrealistic to delay a software release until the product is perfect. Therefore, security is compromised and the product gets shipped with vulnerabilities.
The only solution is to be more proactive and properly remediate vulnerabilities using risk-based vulnerability management and deploy a secure product. Be cyber smart by adopting attack surface management for patching instead of battling the attacks.
Worried about a cyber breach?
Get a complete Attack Surface Management Service. Talk to us.