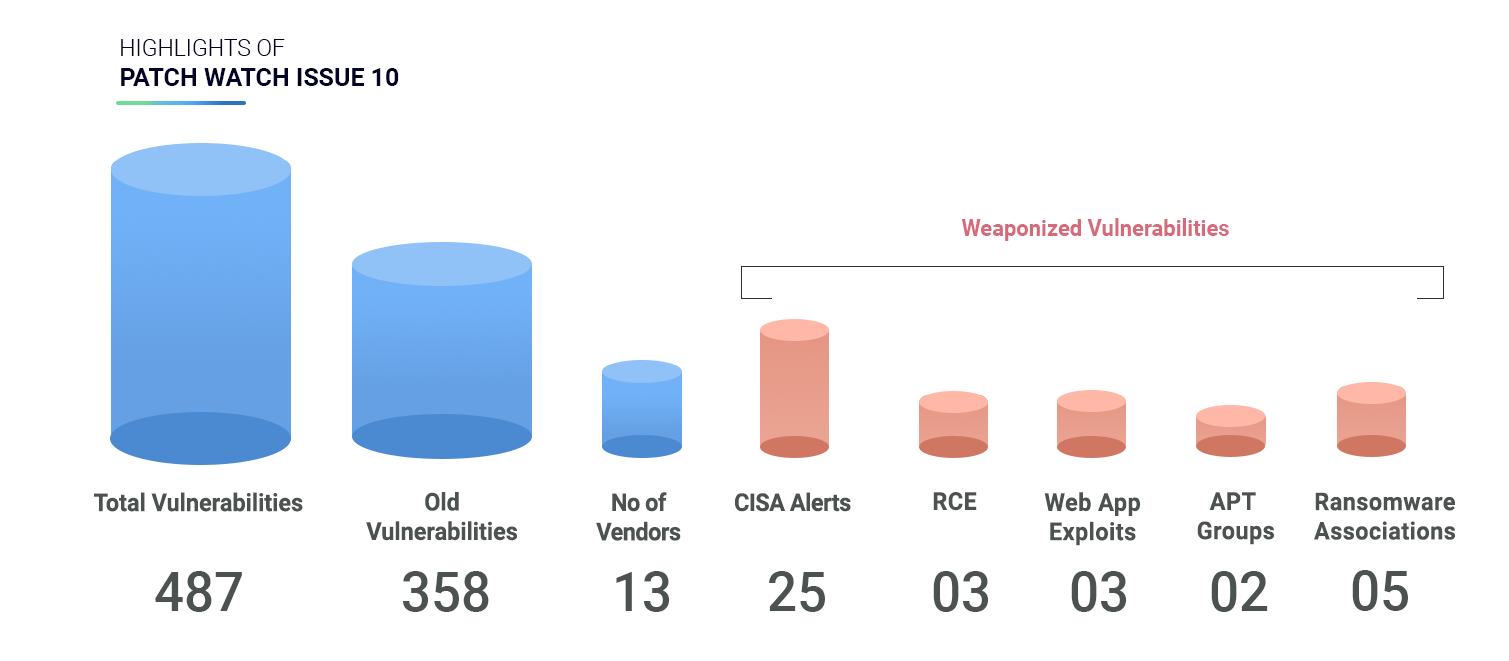
Highlights of Patch Watch Issue 10
We analyzed 487 vulnerabilities and found that –
-
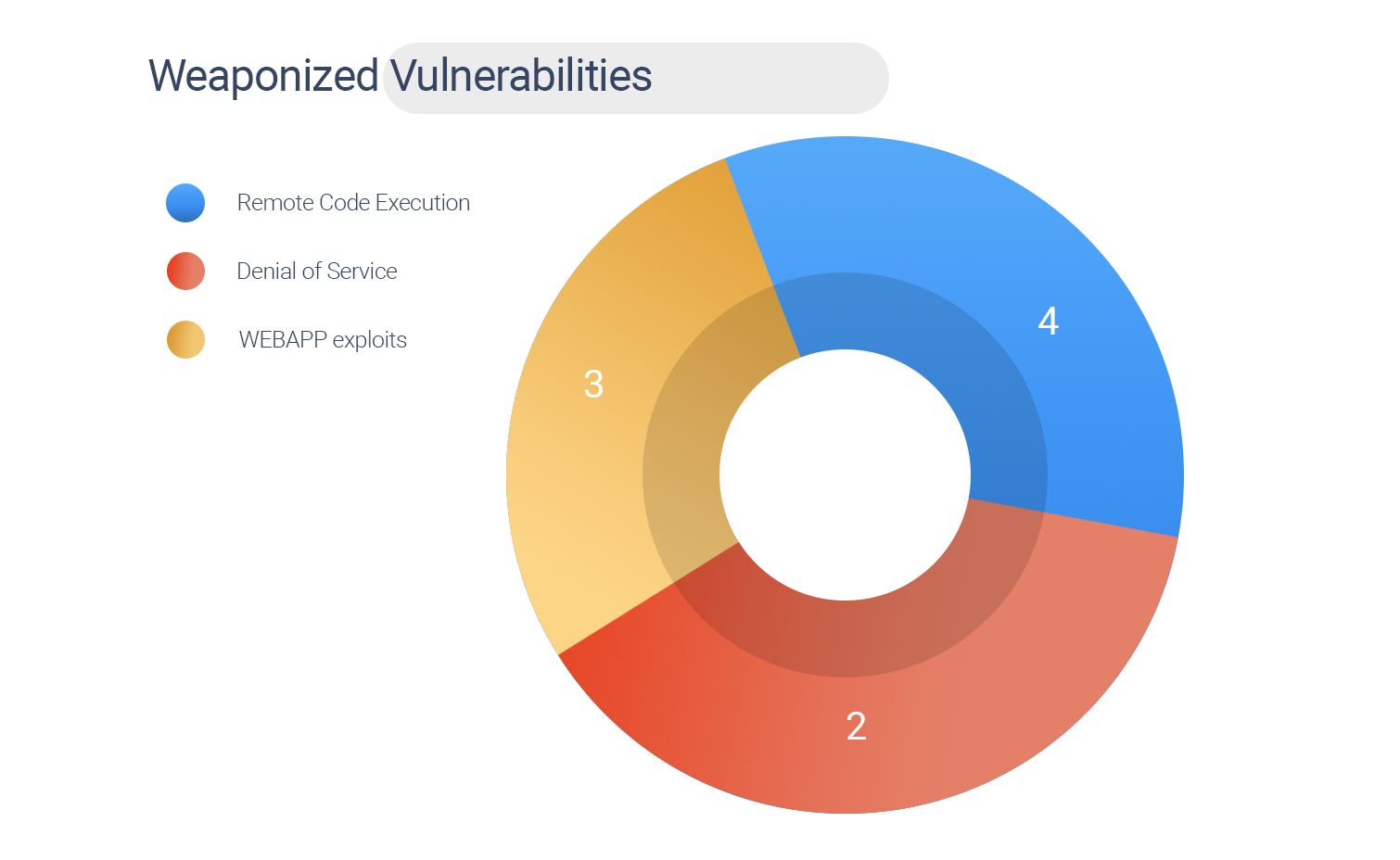
2 CVEs are associated with APT Groups
-
5 CVEs are associated with 5 different Ransomware families.
-
9 CVEs have known exploits
-
478 CVEs are yet to be weaponized
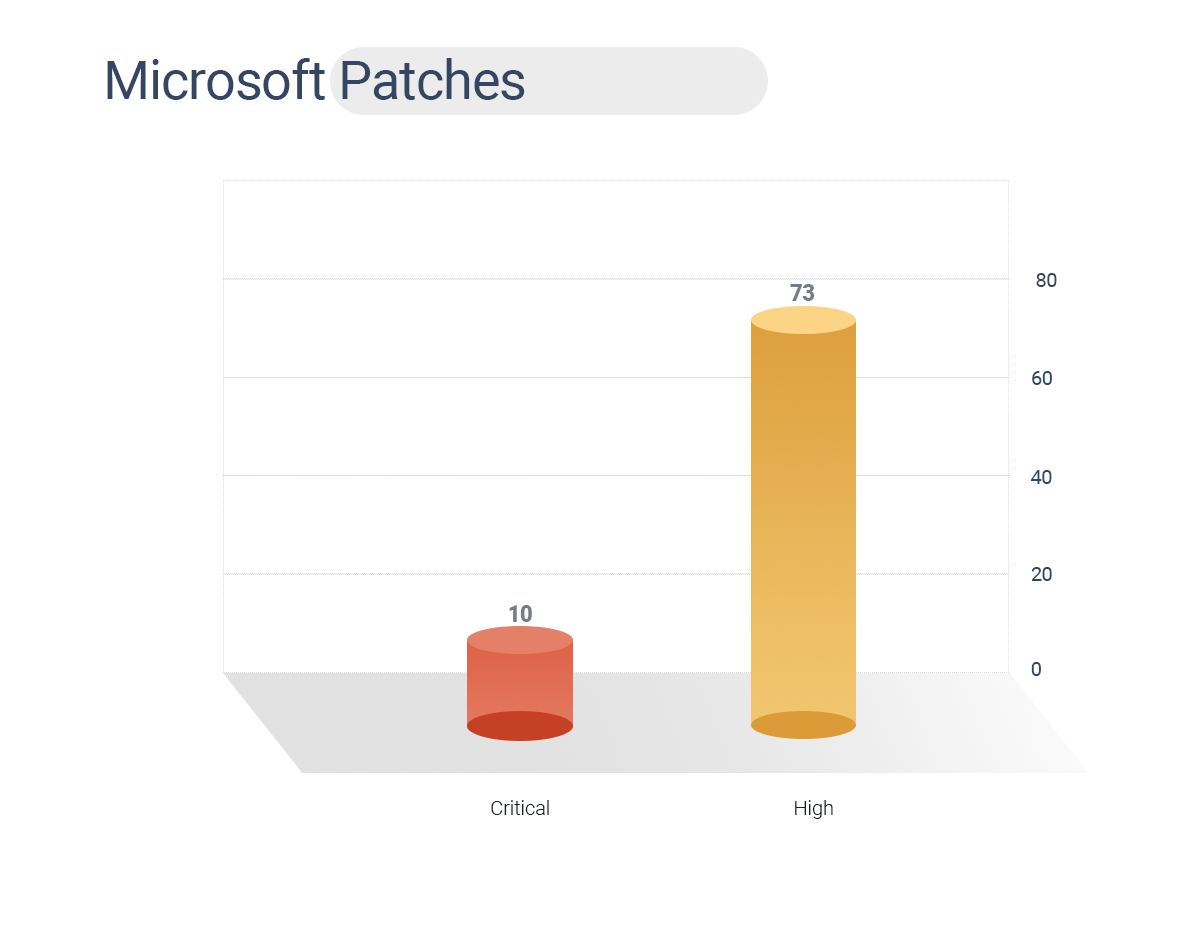
Microsoft rolled out 83 security patches for January.
-
10 CVEs are rated critical, and 73 are high.
-
CVE-2021-1647 is a zero-day exploit with RCE capabilities.
-
This vulnerability existed within the Microsoft Malware Protection Engine version 1.1.17700.4 or later, a core component of Microsoft Defender that addresses malicious software.
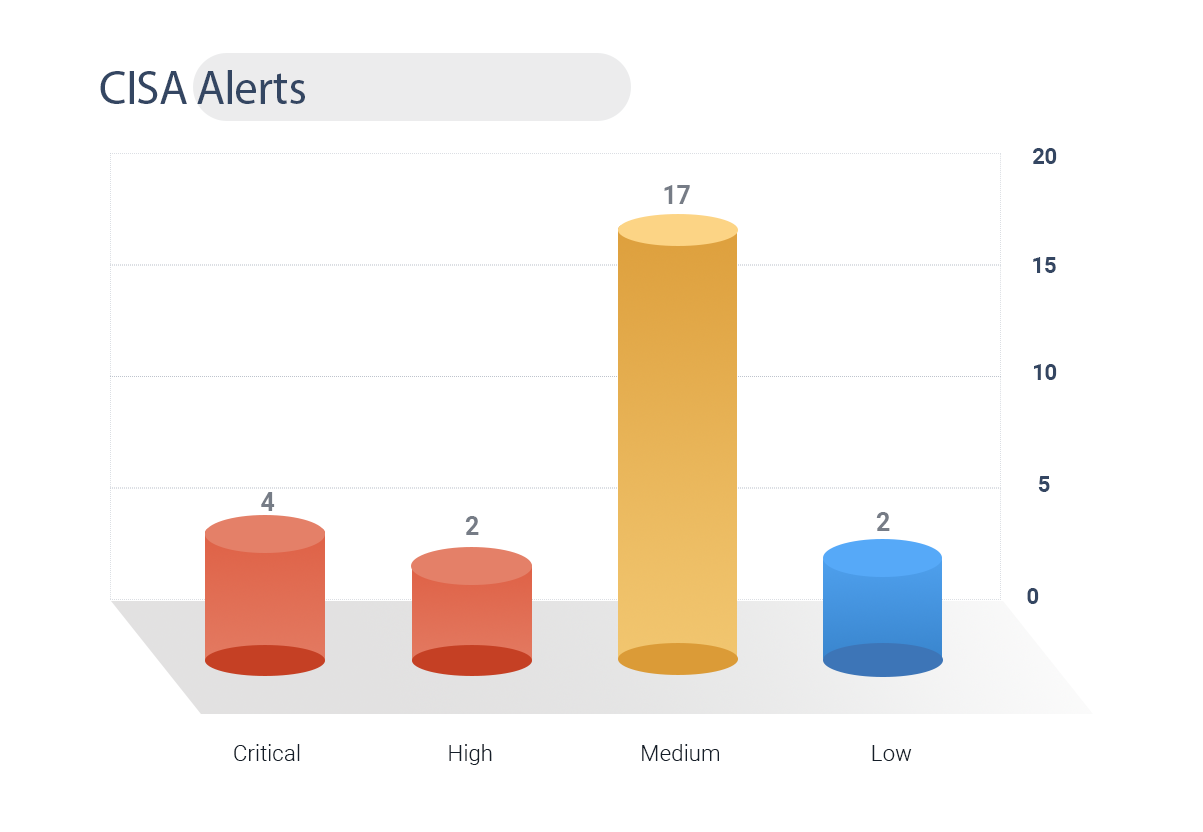
CISA has issued a warning alert for 25 vulnerabilities.
-
2 CVEs have known exploits
-
CVE-2019-0708 is associated with Kelvin SecTeam APT Group and DoppelPaymer and Redkeeper ransomware families given the severity rating of 10.
-
4 CVEs are rated critical, and 2 are high.
358 Old vulnerabilities have been patched.
-
2 CVEs are associated with Kelvin SecTeam and Lazarus APT Groups.
-
4 CVEs are associated with 5 Ransomware families such as Bitpaymer, Petya, Cerber, DoppelPaymer, and Redkeeper.
-
CISA has issued alerts for 24 vulnerabilities.
-
4 CVEs are rated critical, and 2 are high.
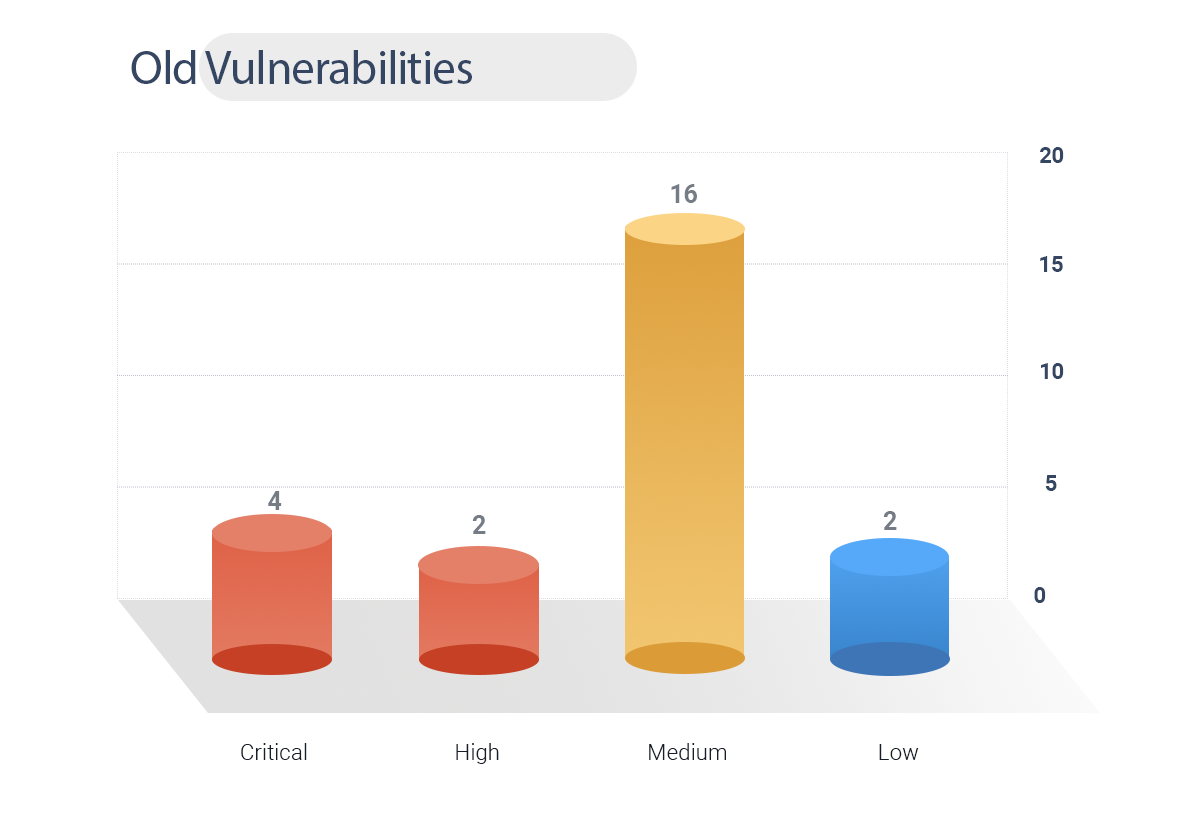
Table: January 2021 Patches
Organizations today need multi-faceted solutions combined with accurate data that factors in trending analytics and latest information. Keeping pace with a steady stream of patches is tough. Vendors patch thousands of vulnerabilities every week but what should you patch first and why? Why should some patches be prioritized and others not?
The need of the hour today is a dynamic attack surface management platform that integrates patch information prioritized by threat context so that organizations know why they should patch some vulnerabilities first.
