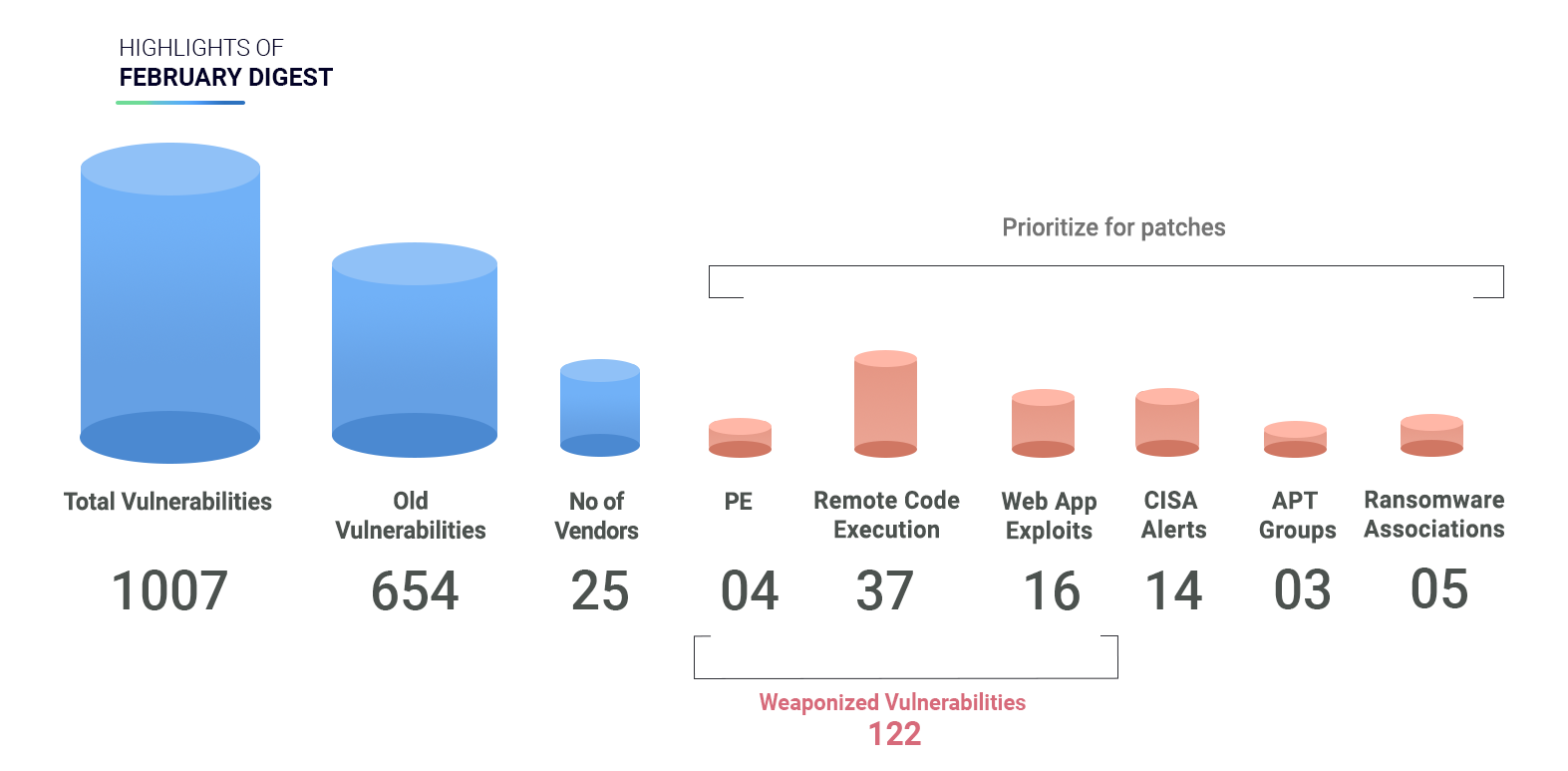
Highlights of February Digest
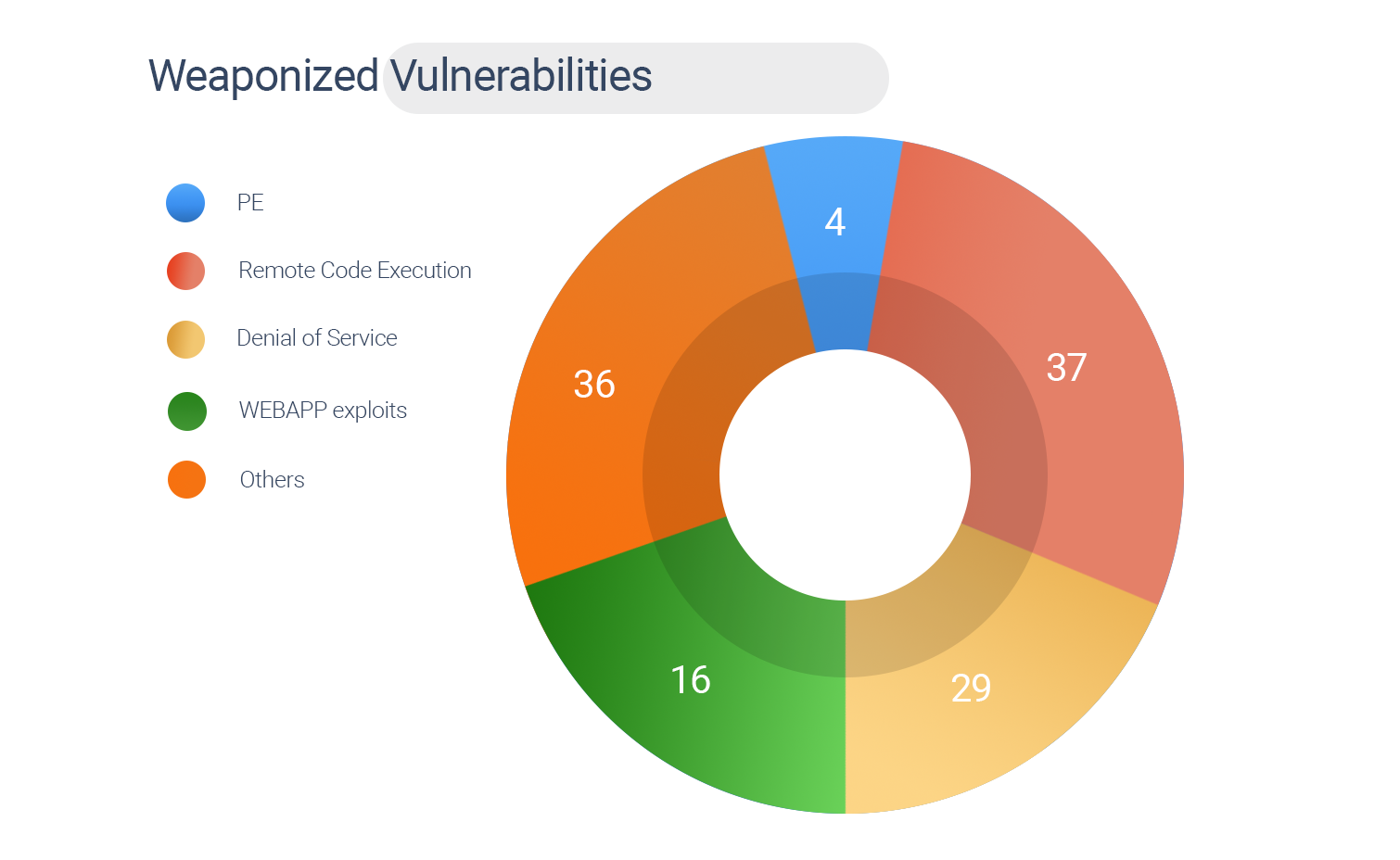
Weaponized Vulnerabilities
We have 122 weaponized vulnerabilities with known exploits. Here is our analysis –
-
21 CVEs are rated critical, and 40 are high severity.
-
1 CVE has been alerted by CISA.
-
4 CVEs have Privilege Escalation capabilities.
-
37 CVEs are associated with Remote Code Execution.
-
16 CVEs are Webapp exploits.
-
29 CVEs have Denial of Service.
Click here for our analysis and download patches.
Based on a survey, 60 percent of organizations suffered a data breach that exploited a known vulnerability for which a patch existed. Therefore, maintaining security hygiene is essential and patch management paramount.
Old Vulnerabilities Patched in February 2021
654 Old vulnerabilities ranging from the year 2009 to 2020 have been patched.
-
5 CVEs are linked to ransomware strains.
-
2 CVEs are associated with the Mercury APT group.
-
5 CVEs have been alerted by CISA.
-
4 CVEs have PE capabilities.
-
29 CVEs are RCE bugs.
-
13 CVEs are Webapp exploits
-
27 CVEs have Denial of Service.
-
42 CVEs are critical and 167 of high severity.
Click here for our analysis and download patches.
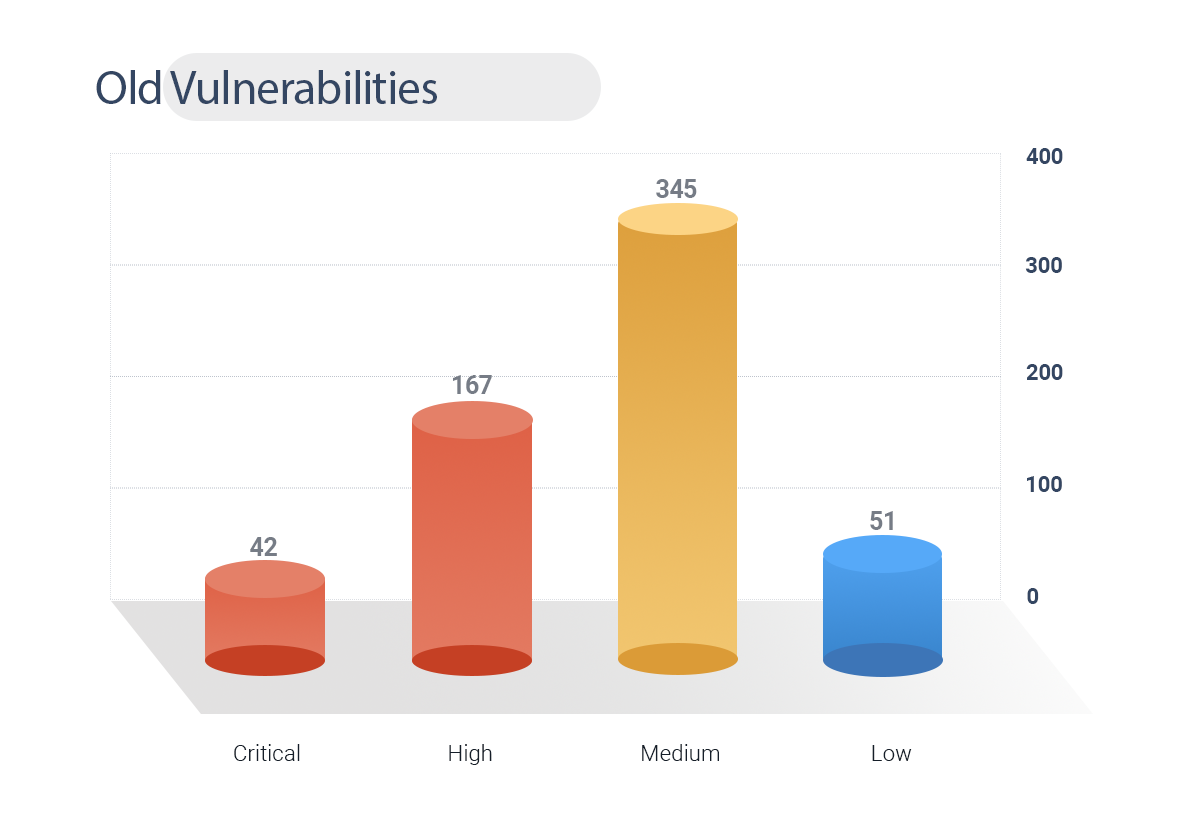
87% of the old vulnerabilities patched are weaponized. Organizations should pay attention to old vulnerabilities that exist in their software and immediately fix them.
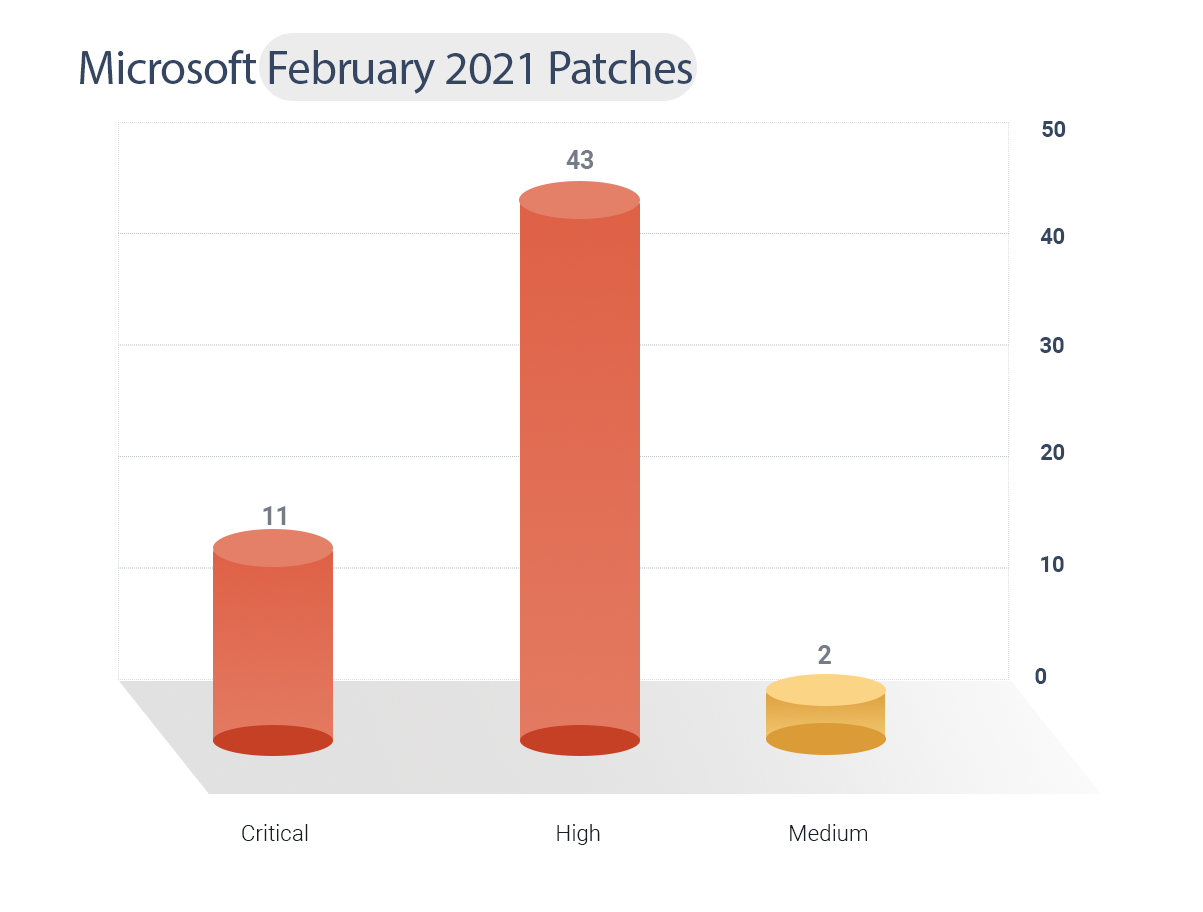
Microsoft February Patches 2021
Microsoft issued patches for 56 security vulnerabilities, including a zero-day(CVE id) that was exploited for the past seven months.
-
11 CVEs are critical, 2 as medium, and 43 are important.
-
CVE-2021-1732 – a Windows zero-day bug with privilege escalation weakness in Win32k, a core component of the Windows operating system.
-
This CVE was exploited the day before the patch release, which is believed to be employed by the Bitter APT group.
-
Exploit code of 6 CVEs was posted online just before the patch was released. The vulnerabilities are CVE-2021-1721, CVE-2021-1733, CVE-2021-26701, CVE-2021-1727, CVE-2021-24098, and CVE-2021-24106.
-
Microsoft published a blog post warning about three vicious vulnerabilities in Windows TCP/IP stack, which allows the operating system to connect to the internet.
-
A second round of security update has been issued for Zerlogon vulnerability CVE-2020-1472, that witnessed active exploitation back in September 2020.
Product Analysis of Microsoft Patches
Let’s take a closer look at the product analysis of this month’s patches. We observed Microsoft patches and found that 21 CVEs were associated with RCE and 12 with PE.
Table: Product Based Analysis
Click here for our analysis and download patches.
CISA Alerts
14 vulnerabilities have been issued a warning alert by CISA
-
1 CVE has been weaponized.
-
1 CVE is rated critical, 1 of high, and 5 of medium severity.
Click here for our analysis and download patches.
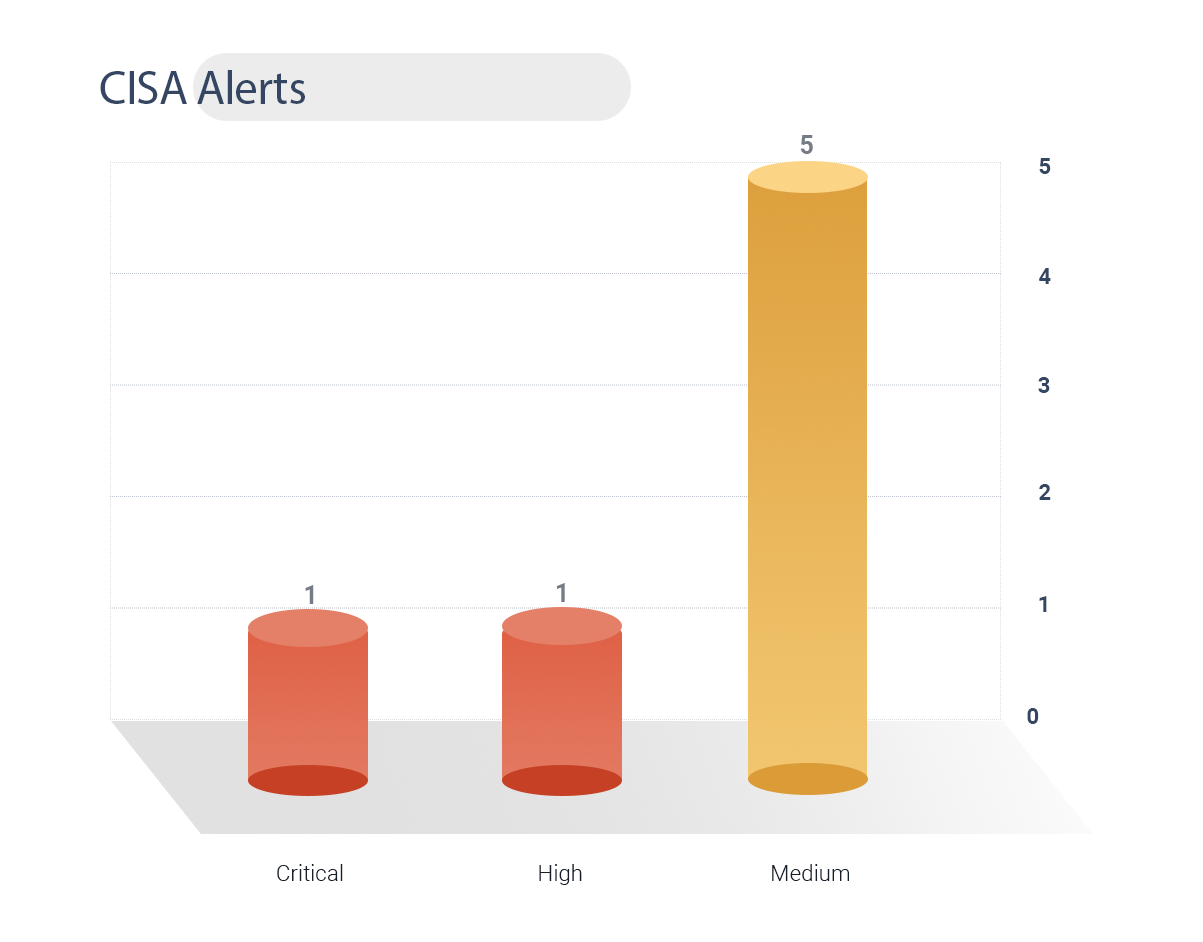
Table: February 2021 Security Patches
In today’s ever-increasing threat surfaces, patching cannot be an afterthought. It is essential to implement a risk-based vulnerability strategy and secure your environment from cyber attacks.