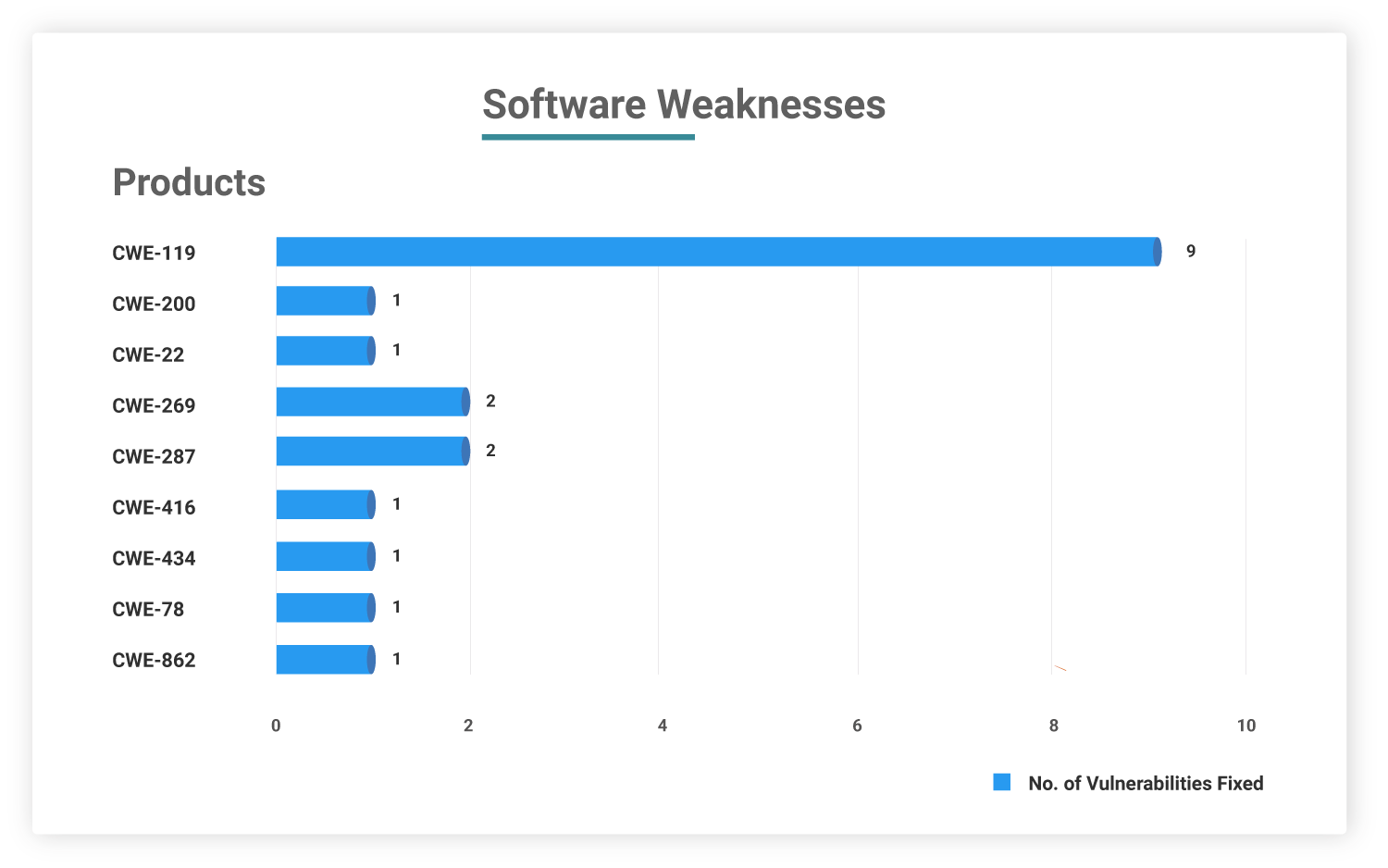
The US Cybersecurity and Infrastructure Security Agency (CISA) has again updated its Known Exploited Vulnerabilities (KEVs) Catalog which now contains 647 CVEs.
This blog brings you all the DHS CISA KEVs that need to be prioritized for patching this week (April 18 to April 24, 2022).
A total of 39 known exploited vulnerabilities from the DHS CISA catalog should be patched by federal agencies this week before April 18 and April 24, 2022. We further analyzed these 39 KEVs and found that –
Our ML and AI Model predict that 36 CVEs out of 39 are potentially 38 times more likely to be exploited. Therefore patch it immediately before you run for the cure.
How Far Back Do They Go?
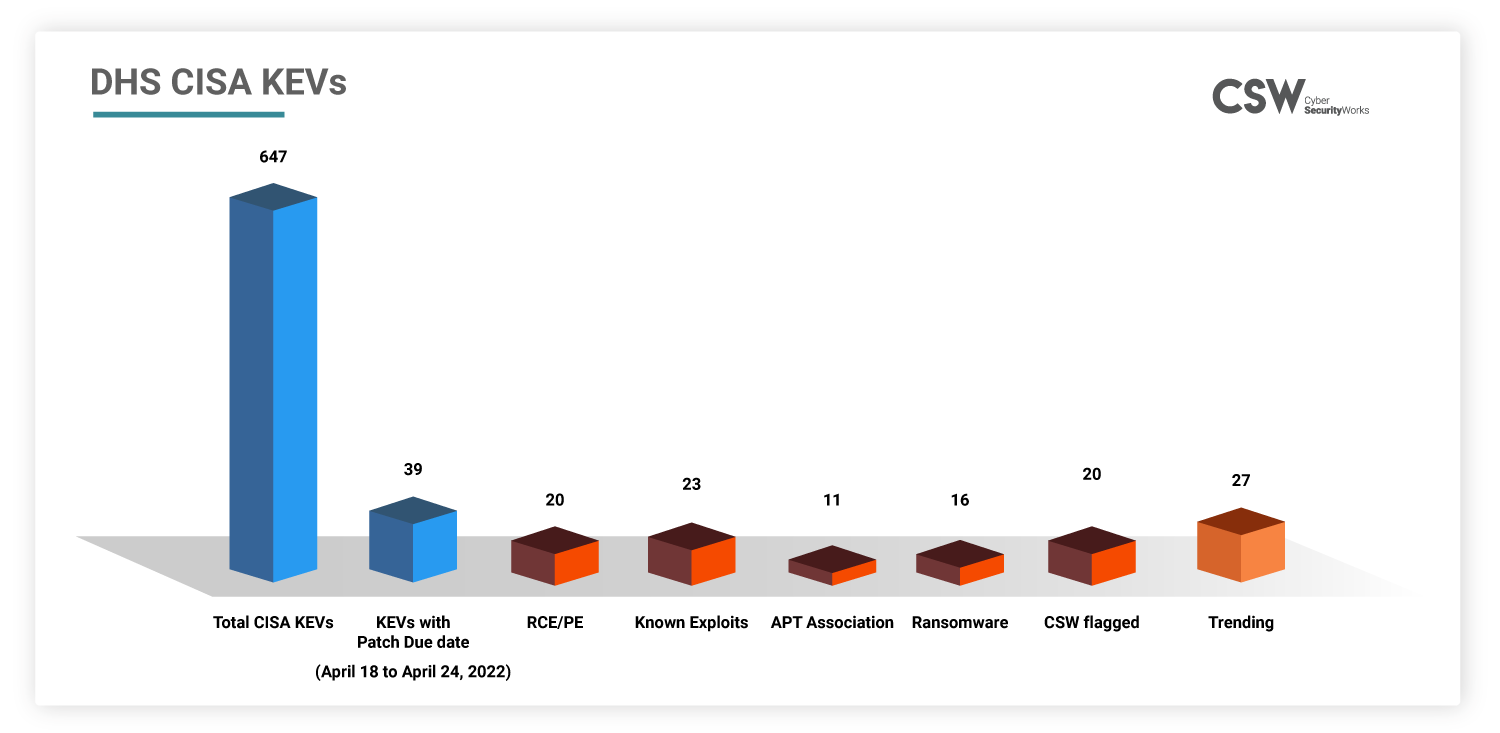
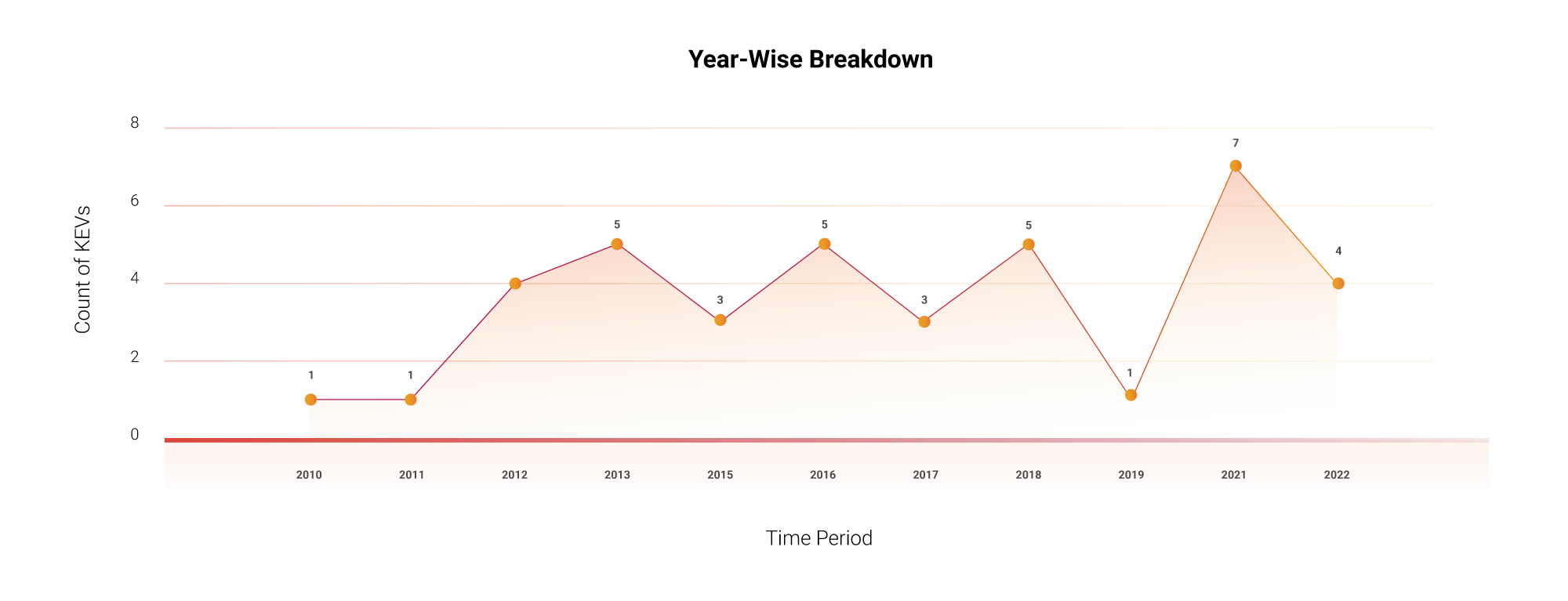
Of the 39 KEVs, 35 CVEs are old vulnerabilities dating from 2010 to 2021 with a patch deadline of April 18 and April 24, 2022. There are 22 KEVs that exist in Microsoft products, 3 KEVs found in Oracle 2 KEVs from Adobe and SonicWall each.
Ransomware and APT Associations
When we analyzed based on the threat risk associations, we found 11 KEVs associated with multiple APT threat groups and 16 KEVs linked to different ransomware strains. All these threats associated vulnerabilities are older vulnerabilities.
The inclusion of old vulnerabilities to the KEV catalog is due to the fact that they are used in new exploit chains that are applicable today, which suddenly makes them relevant again.
|
CVE |
Ransomware_Name |
APT_Name |
|---|---|---|
|
CVE-2010-4398 |
– |
FIN6 |
|
CVE-2011-2005 |
– |
FIN6 |
|
CVE-2012-5076 |
Urausy, Reveton |
– |
|
CVE-2013-2465 |
Cerber, CryptoWall |
Corkow, Red Star, Sandworm Team |
|
CVE-2013-2551 |
Kovter, CryptoFortress, Princess Locker, TeslaCrypt, CryptoWall, CryptoLocker, Reveton |
Corkow |
|
CVE-2013-2729 |
CryptoWall 2.0 |
Winnti Group |
|
CVE-2013-3660 |
CryptoWall 2.0 |
FIN7, FIN6 |
|
CVE-2015-2419 |
Princess Locker, TeslaCrypt, Pony |
Lazarus Group |
|
CVE-2015-2426 |
Cerber, TeslaCrypt, CryptoWall, Locky |
– |
|
CVE-2016-0189 |
ITLock, Princess Locker, Cerber, Mole, Nemty, Matrix, Locky, Magniber |
Operation Earth Kitsune, PittyTiger |
|
CVE-2016-7200 |
Cerber |
– |
|
CVE-2016-7201 |
Cerber |
– |
|
CVE-2017-0037 |
Cerber |
– |
|
CVE-2017-0213 |
Ragnar Locker, NotPetya, Nefilim, WannaCry, Netwalker, Dharma |
APT29, Transparent Tribe, Winnti Group |
|
CVE-2018-10561 |
Muhstik |
Kelvin SecTeam |
|
CVE-2018-10562 |
Muhstik |
– |
|
CVE-2018-8440 |
GandCrab, GandCrab 5 |
– |
|
CVE-2021-28799 |
Qlocker, eCh0raix |
– |
|
CVE-2015-1770 |
– |
FIN7 |
Which Vendors Are Affected?
Of these 39 KEVs that have a patch deadline of April 18 and April 24, 2022, affect major vendors such as Microsoft, Oracle, Adobe, Atlassian, and Dell.
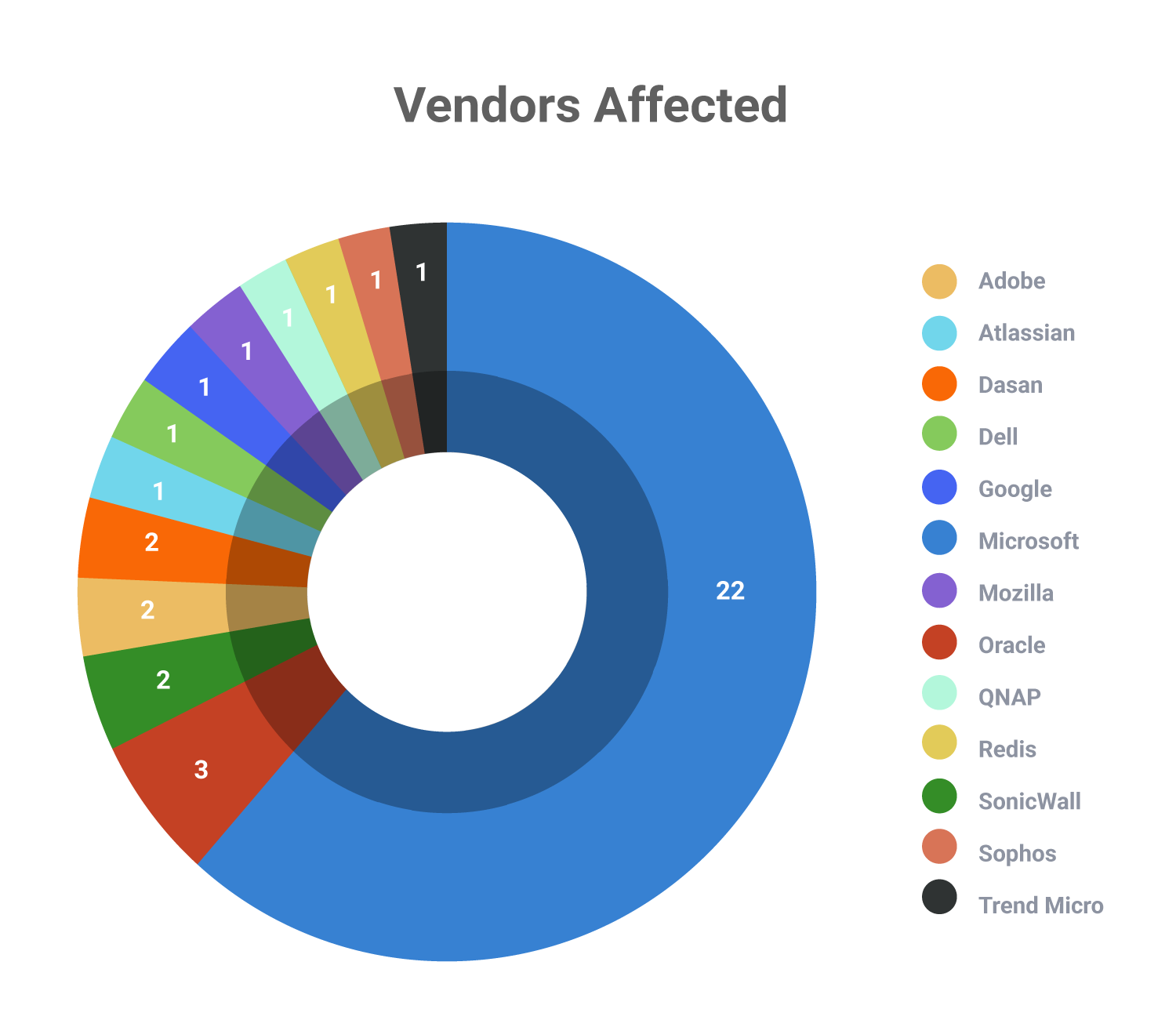
Software Weaknesses
The analysis of these KEVs revealed that 59% of the KEVs with a patch due date of April 18 and April 24, 2022, fall under the Top 40 Most Dangerous Software Weaknesses as well 39% of KEVs categorized under KEVs fall OWASP Top 10:2021.
Severity Scores
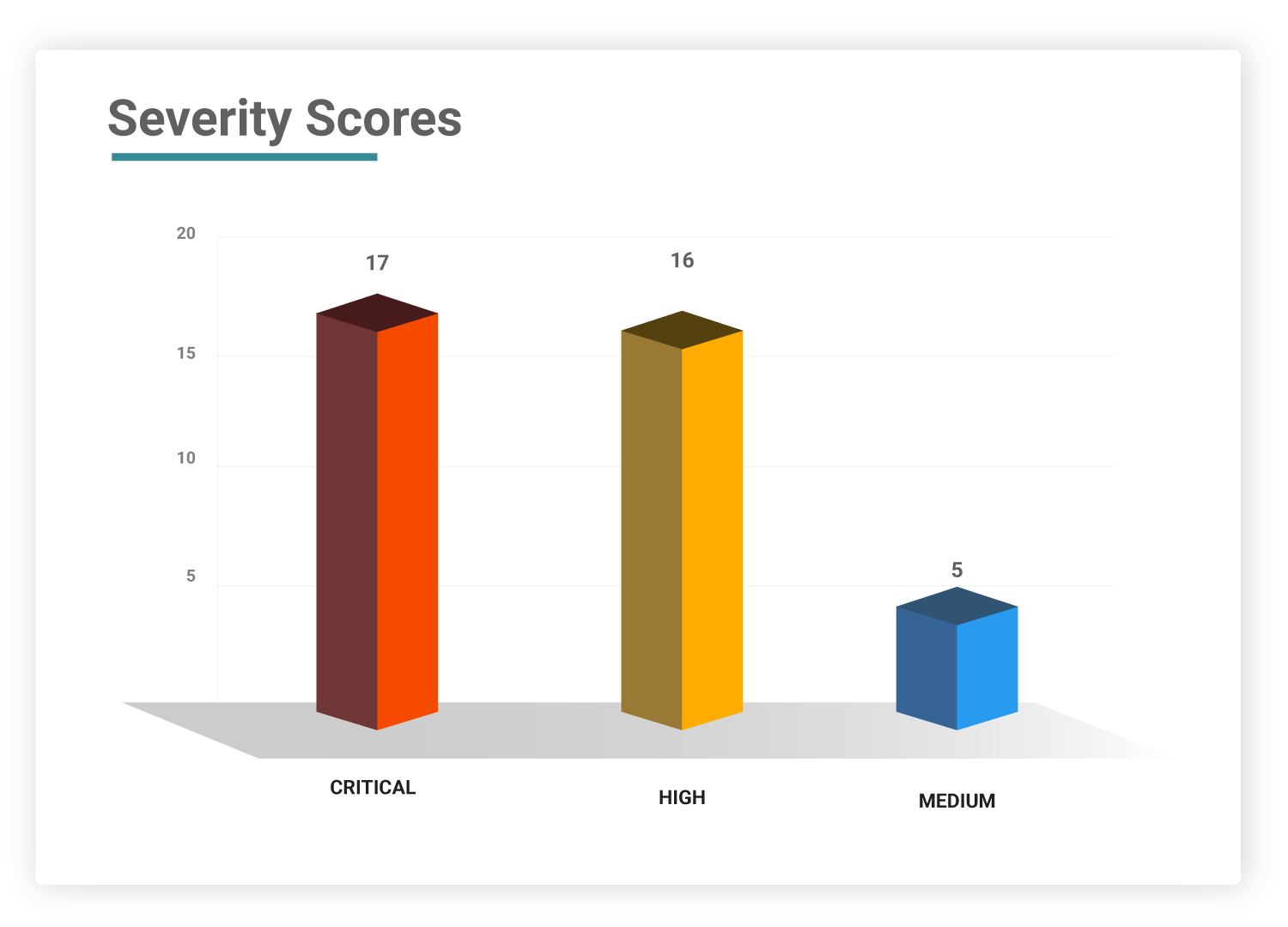
Table: DHS CISA KEVs April Patches
Clock is Ticking!
In order to balance the practical constraints of system administration with best security practices, CISA is likely to publish new sets KEVs with intervals between them. The CISA catalog also demonstrates how quickly threat actors begin to target a vulnerability once a vendor discloses it. Hence, it is important for admins to apply security updates as soon as possible to prevent their exploitation.
Click here to know our detailed analysis of all the DHS CISA KEVs and download their patches.