On June 24, 2021, Dell released fixes for four BIOS connect vulnerabilities that expose over 30 million individual devices. These security flaws could allow unauthorized remote code execution in a pre-boot environment for 129 different Dell products by giving a high-level control of the operating systems (OS).
Reasons to Patch these Vulnerabilities
We examined the recently patched Dell vulnerabilities and here are our findings –
-
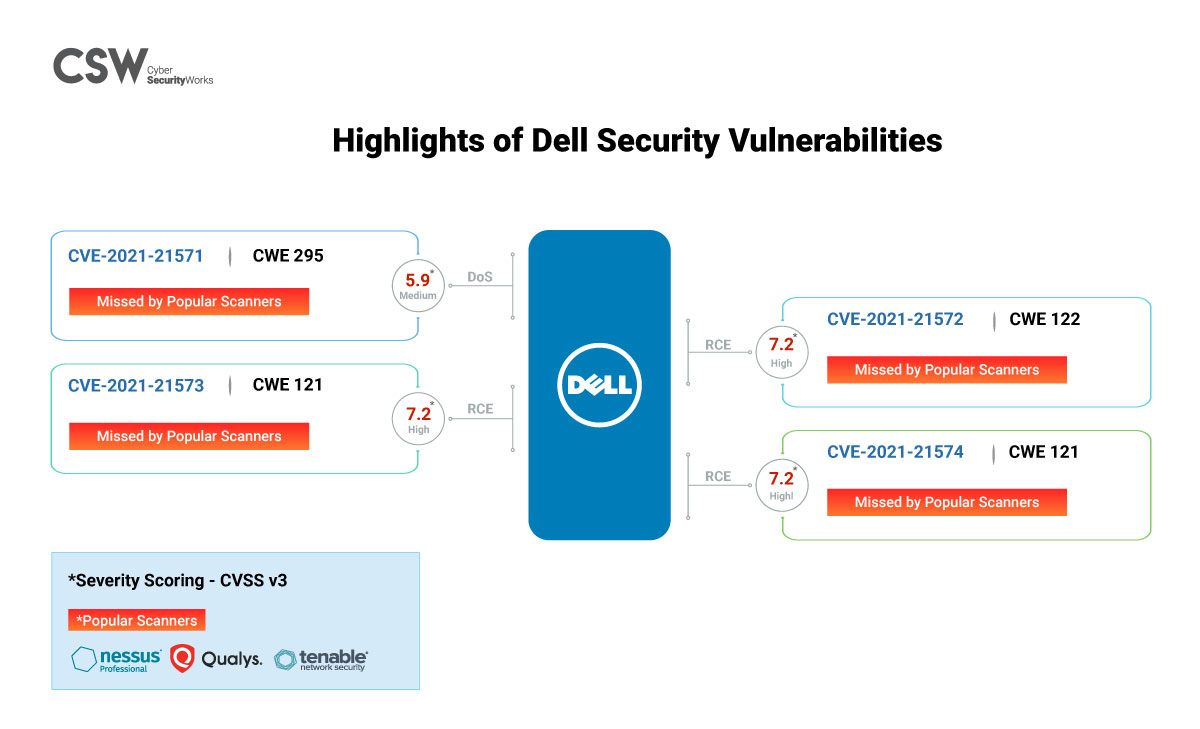
Three of the Dell vulnerabilities are Remote Code Execution possibilities and one is Denial of Service.
-
Successful exploitation of these Dell BIOSConnect and HTTPS Boot features could potentially lead to a supply chain attack leading to complete control of the system by attackers.
-
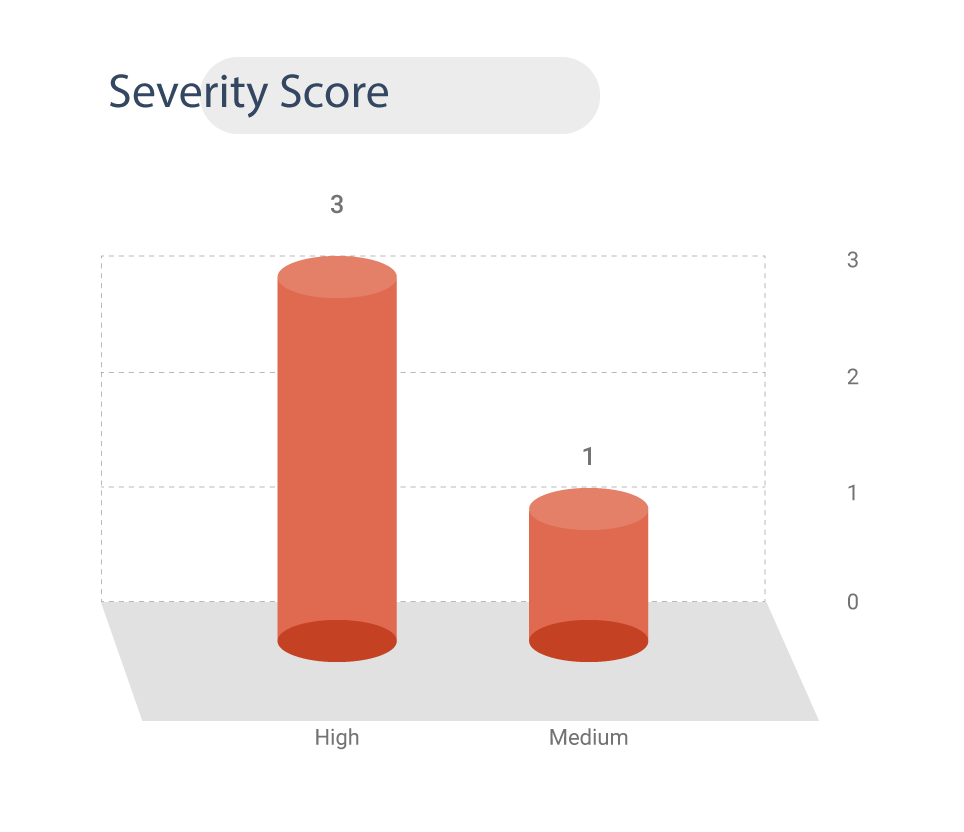
Three CVEs are rated high and one of medium severity.
-
The CVSS V3 score assigned to these vulnerabilities ranges from 5.9 (medium) to 7.2 (high).
-
This series of vulnerabilities lead to Improper Certificate Validation and Buffer Overflow classified under CWE-295, CWE-122, and CWE-121.
-
A patch is available for these vulnerabilities, which reduces the risk posed by threat actors.
-
Yet, there are no publicly known exploits for these CVEs.
-
All the popular scanners failed to detect these four vulnerabilities.
Severity Scores
Timeline
| Date | Description |
| March 2, 2021 | Eclypsium discovered four vulnerabilities in Dell. |
| March 3, 2021 | Dell acknowledged the vulnerabilities. |
| June 18, 2021 | Dell remediated two of the issues and published the advisory. |
| June 24, 2021 | Dell issued an enhanced update to all four issues. |
| June 24, 2021 | Vulnerabilities updated in NVD Database. |
It’s worth noting that these vulnerabilities were discovered on March 2, 2021, and it took 118 days to develop a patch for these issues. Therefore, Organizations should continuously work to fix the issues in their product and quickly provide users with either a significant update to the version or a patch.
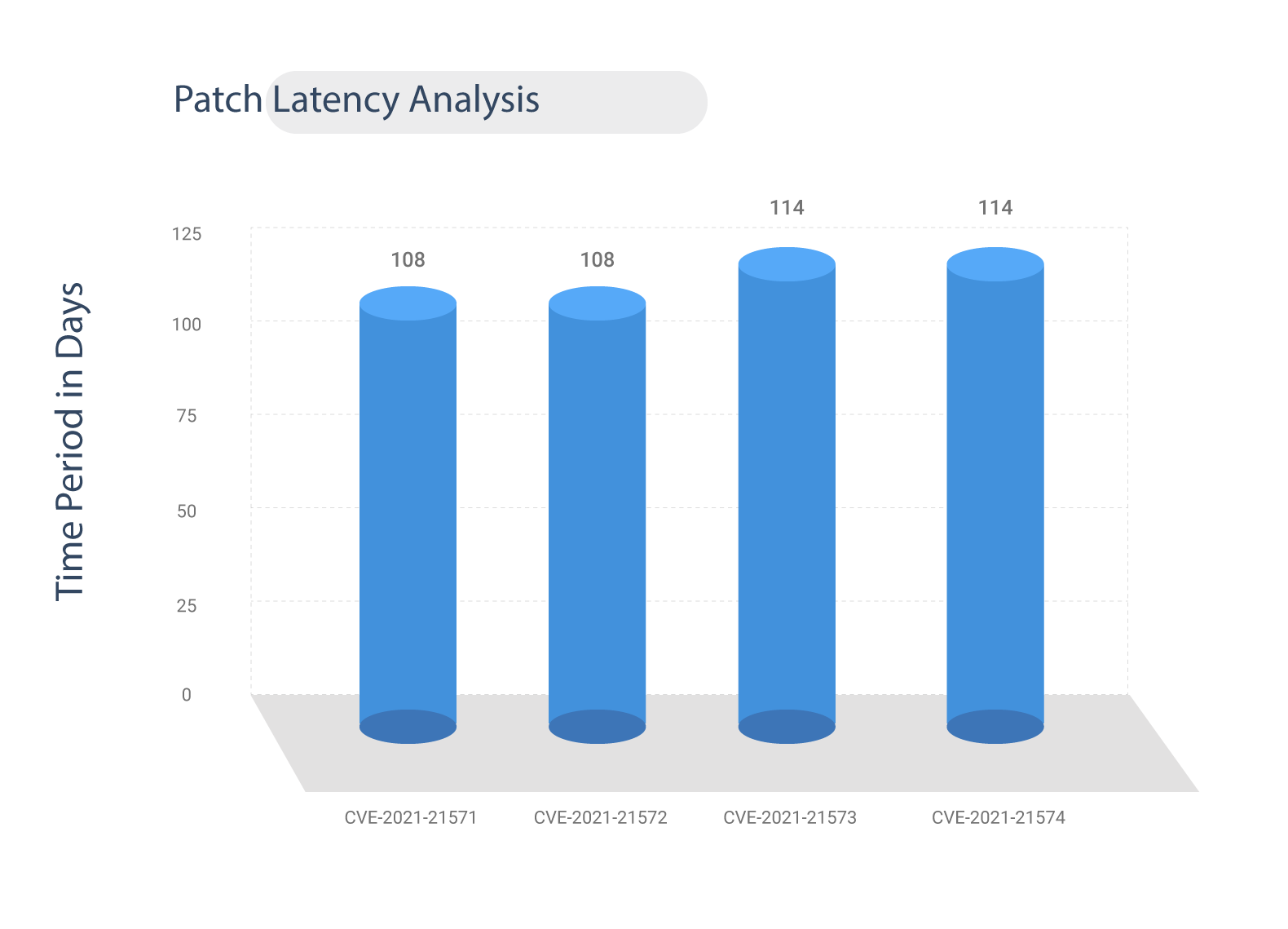
Table: Dell Patches
Dell had stated that CVE-2021-21573 and CVE-2021-21574 were remediated on the server-side on May 28, 2021, and these weaknesses require no additional customer action. Alternatively, CVE-2021-21571 and CVE-2021-21572 that exist in Dell Client BIOS need to be addressed for prompt patching.
We recommend all Dell users to upgrade to its latest version and secure their devices from attackers.
