Did you know over 277K patient data was exposed using ZOLL gaps in 2018?
In June 2021, ZOLL Medical Corporation released six security patches for its defibrillator dashboard platform. Today, medical records are the most favorite target for cybercriminals because of the treasured personally identifiable information (PII) that could possibly lead to financial breaches. These records are a lot richer than credit card passwords and are valued up to $250 per data on the dark web.
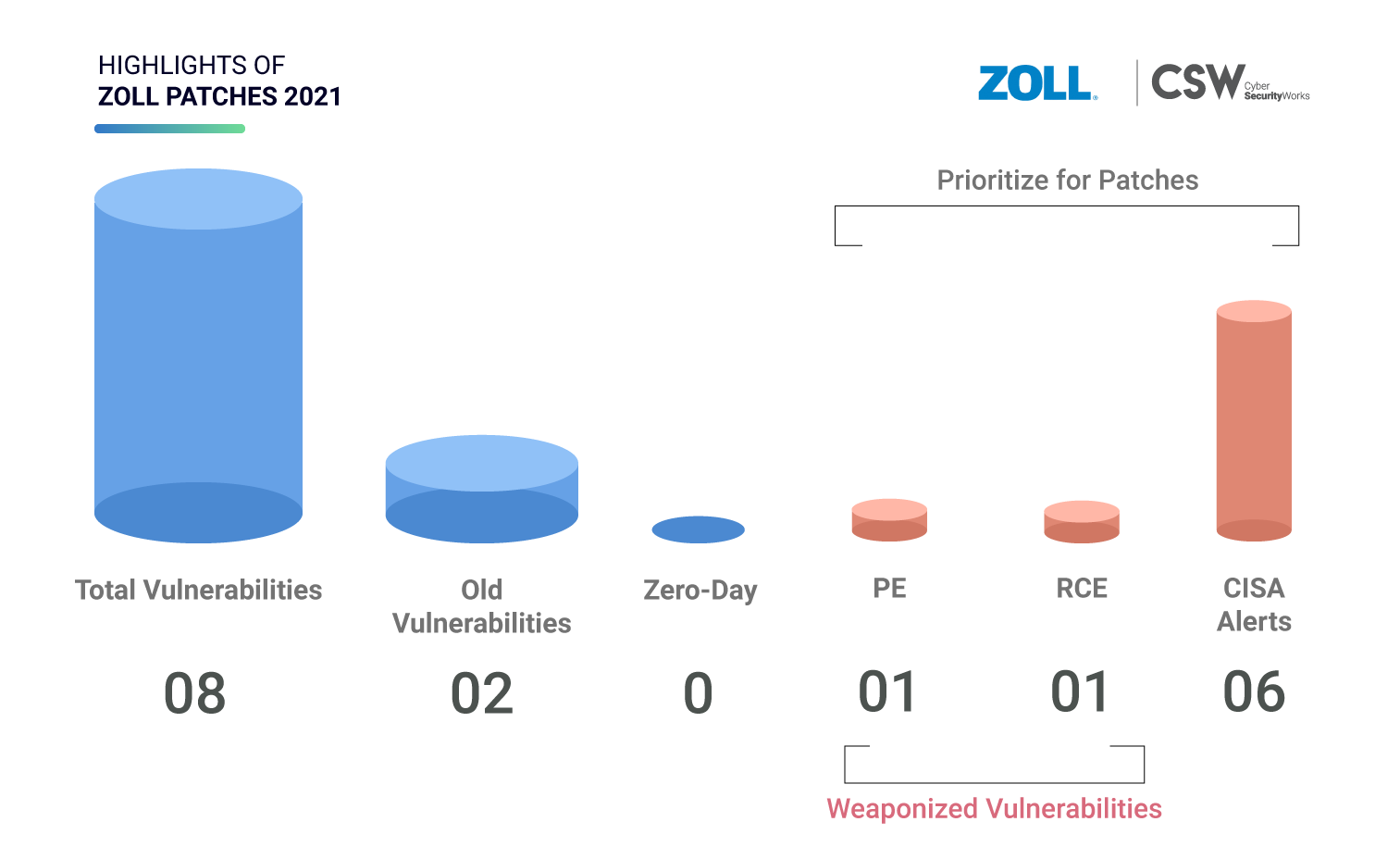
We examined eight vulnerabilities in the ZOLL defibrillator dashboard and highlighted the ones that need to be prioritized for immediate patching.
Why Is It Important to Patch These Vulnerabilities?
Securin’s researchers analyzed eight vulnerabilities; here are our findings.
-
One CVE is remote code execution, one is privilege escalation, two are denial of service, and four are theft-sensitive information bugs.
-
Leveraging these vulnerabilities, a nonadministrative user could obtain access to the application and achieve remote code execution to steal patient credentials impacting the confidentiality of the application.
-
On June 10, 2021, CISA issued a medical advisory for six CVEs urging all users to patch these vulnerabilities.
-
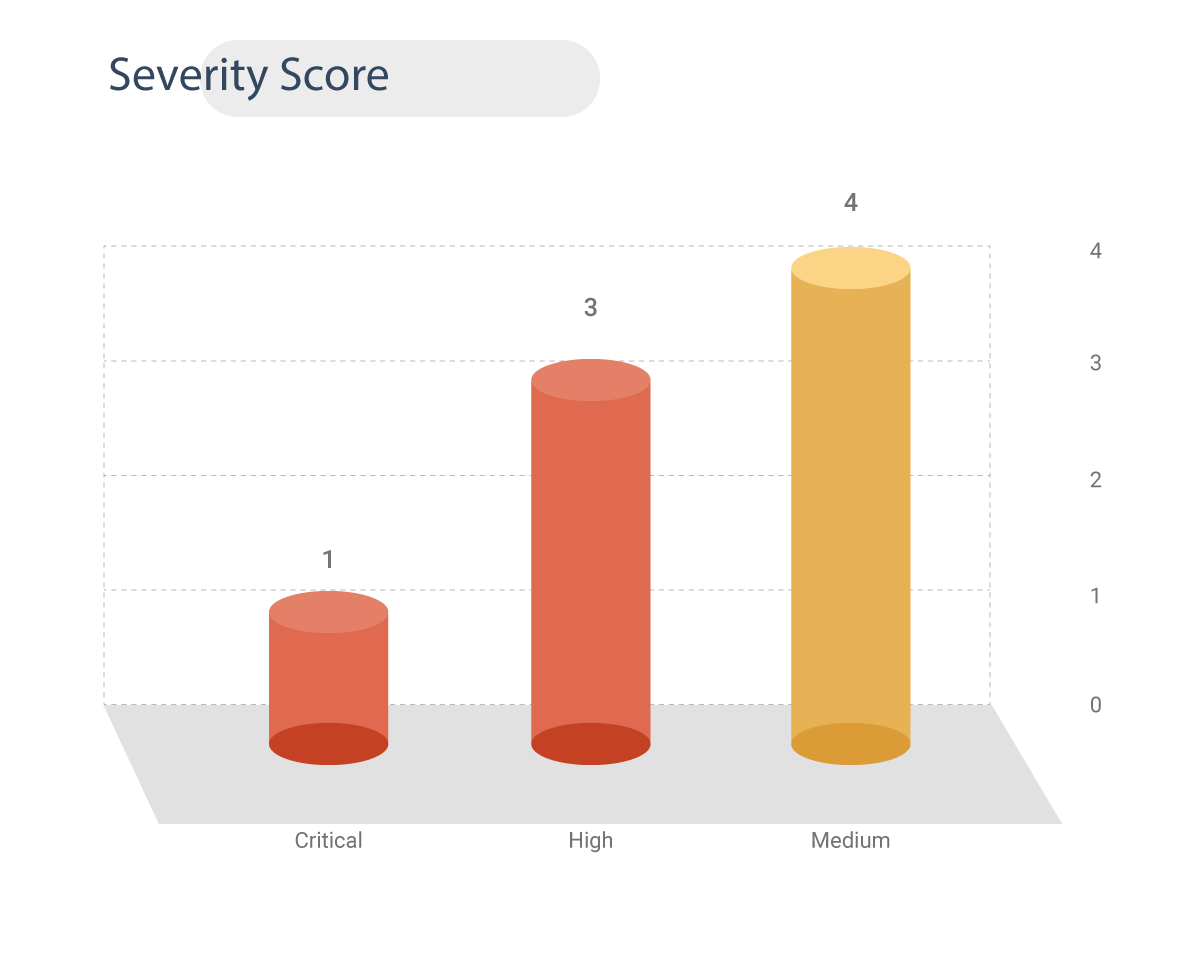
The CVSS V3 score provided for these vulnerabilities ranges from 4.6 to 9.1. One CVE is rated as critical severity, three are rated as high severity, and four are rated as medium severity.
-
CVE-2007-6756 and CVE-2013-7395 are older weaknesses that were discovered in 2007 and 2013 with a CVSS V3 score of 4.9 (medium).
-
Each of these vulnerabilities has got a Common Weakness Enumeration ID. These are CWE- 434, CWE – 312, CWE – 321, CWE- 79, CWE – 257, CWE -269, and CWE – 255, in which three of them fall under the Top 25 Most Dangerous Software Weaknesses published by MITRE.
-
All products prior to the ZOLL defibrillator dashboard version 2.2 are affected by these weaknesses.
-
A patch is available to fix these vulnerabilities and cut down medical risks.
-
As of writing, there are no publicly known exploits for these ZOLL vulnerabilities.
-
Interestingly, popular scanners such as Qualys, Nessus, and Tenable failed to detect these vulnerabilities.
RCE and PE Vulnerability
CVE-2021-27489 is a critical vulnerability that exists in the ZOLL defibrillator dashboard platform with Remote Code Execution capabilities. This CVE has been given a CVSS V3 score of 9.9 (critical) and leads to Unrestricted Upload of File with Dangerous Type, categorized under CWE – 434 that falls under Top 25 Most Dangerous Software Weaknesses published by MITRE.
CVE-2021-27485 is another vulnerability with Privilege Escalation possibilities. This CVE has a CVSS V3 score of 7.1 (high) that leads to Credentials Management Errors under CWE -255. An exploitation of this weakness could cause the execution of commands on the webserver without authentication.
Therefore, focusing on these two vulnerabilities for patching would be the priority.
Table: ZOLL Patches (Airtable)
We recommend to the health professionals that they immediately patch the ZOLL defibrillator dashboard to version 2.2 and perform frequent checks to confirm device readiness.
In the past weeks, security researchers have been witnessing increased attacks on health care sectors and services because of the high value and long shelf life of the PII. Threat actors can use such information to purchase prescriptions, receive treatment, or raise fake medical claims causing disruption and chaos for the victims.
To ensure security to the health care data, conduct the Health Insurance Portability and Accountability Act of 1996 (HIPAA) risk assessment that would help reduce the exposed assets that are most likely to be exploited.
