Last week, Garmin fell prey to WastedLocker Ransomware attack. Malicious script masquerading as software updates was delivered through legitimate (but compromised) websites.
We have put together a list of compromised websites, IOCs, IP addresses, hashes, that were used to target Garmin. We recommend that you update your IPS (Intrusion Prevention System) and IDS (Intrusion Detection System) to avoid visiting these sites.
Courtesy: Symantec, nccgroup, Sentinel One, Cyberswachtakendra, IBM
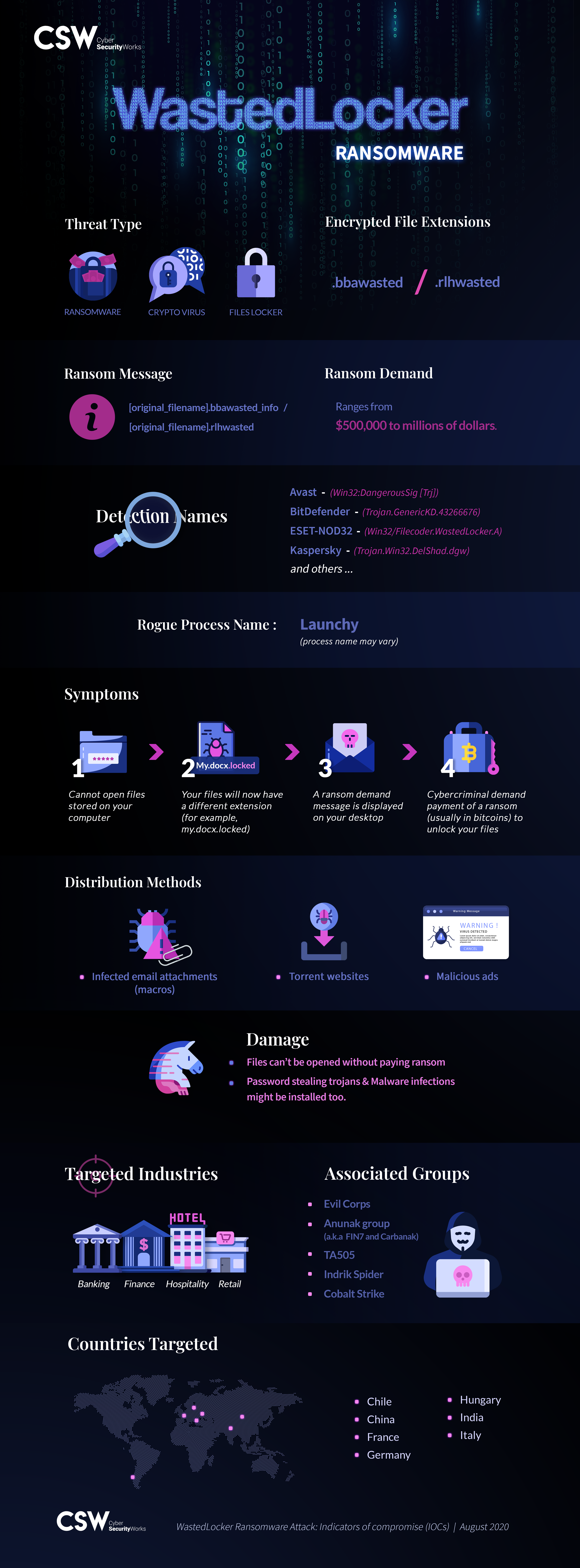
Ransomware attack on Garmin
On July 23, WastedLocker ransomware attacked Garmin, a global fitness wearable device company causing a five-day outage to its product users and call centers. Garmin’s website, mobile applications, and weather services applications were down, causing widespread disruption and chaos.
WastedLocker, a dangerous ransomware used by the Russian gang named Evil Corp targets US and European organizations and was earlier associated with Dridex, and BitPaymer ransomware attacks.
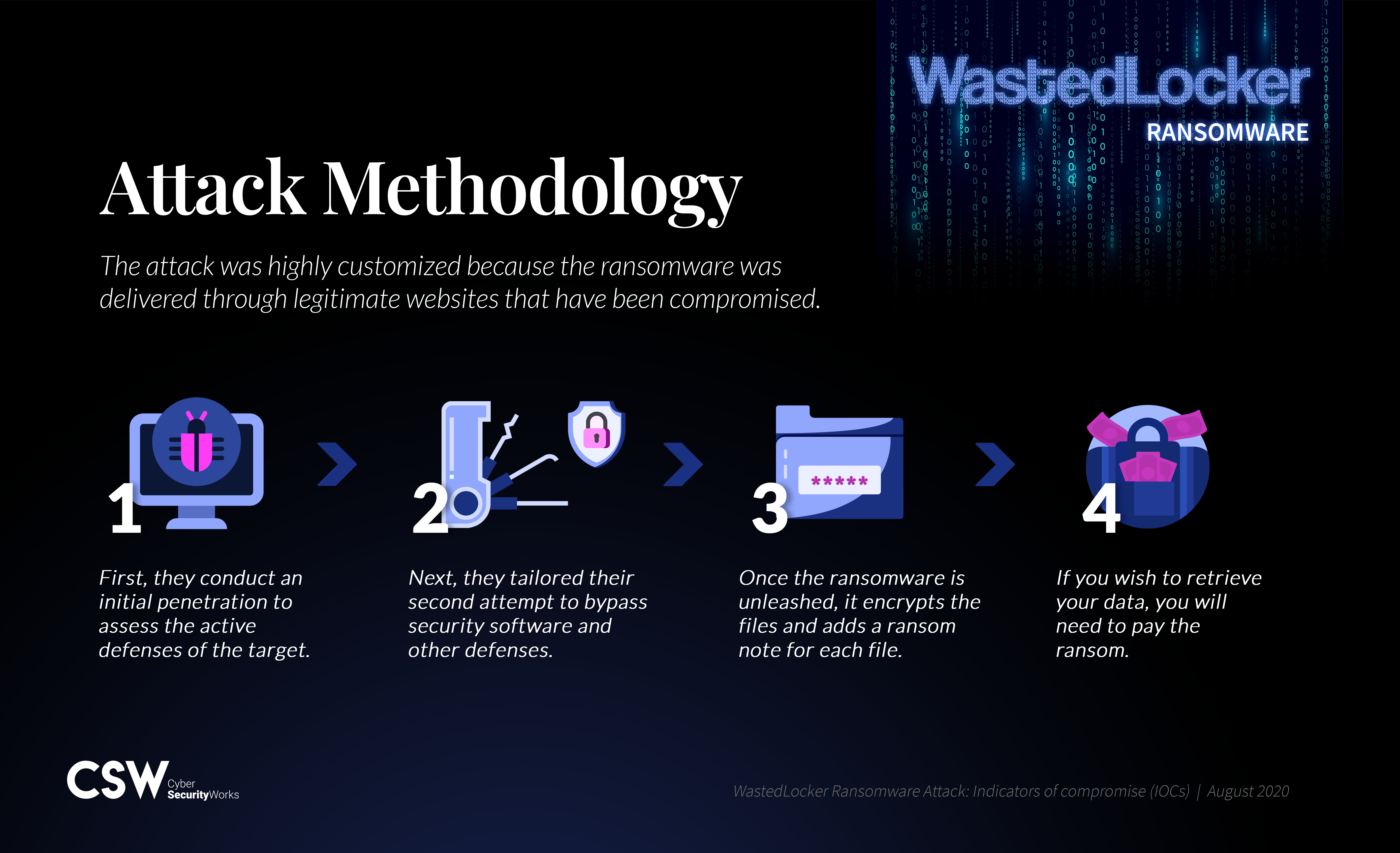
Attack methodology
The attack was highly customized because the ransomware was delivered through legitimate websites that have been compromised.
- First, they conduct an initial penetration to assess the active defenses of the target a
- Next, they tailored their second attempt to bypass security software and other defenses.
- Once the ransomware is unleashed, it encrypts the files and adds a ransom note for each file.
- If you wish to retrieve your data, you will need to pay the ransom.
How to avoid WastedLocker attack?
WastedLocker ransomware began its attack through 150 compromised websites that were disguised as software updates. Securin analysts have put together a list of domains that have been compromised. We recommend that you add them to your IPS (Intrusion Prevention System) and IDS (Intrusion Detection System) to avoid downloading malicious scripts that would trigger this attack. (Note: Scroll up to download this list)
The following protection protocols can be activated in your systems/devices to protect against this ransomware –
Over seven scanners are not detecting this ransomware. You can check them out here and switch to applications that do.
With ransomware attacks becoming more frequent and sophisticated in its payload, we believe that basic knowledge about email phishing and conducting awareness programs about cybersecurity is the need of the hour. And where this specific ransomware is concerned, having backup data in a non-connected environment would keep you safe.