In May 2020, Securin warned the industry of two critical vulnerabilities in Pulse Secure VPN and Citrix’s Remote Desktop solution that could be used by Ransomware or APT groups.
The digital response to the COVID-19 crisis has also created new security vulnerabilities. Attackers seek to exploit the gaps opened when remote employees use insecure devices and networks. Threat actors are using known attack techniques to exploit vulnerabilities in remote access services and VPN technologies.
Organizations are realizing they have to fundamentally change the way they work. For security and risk management leaders, this means grappling with the best course of action to understand the latest attack techniques and assessing defenses against those types of attacks is critical to improving your cybersecurity posture of large-scale modern remote access.
One year after our warning, NSA, FBI and CISA validated the same.
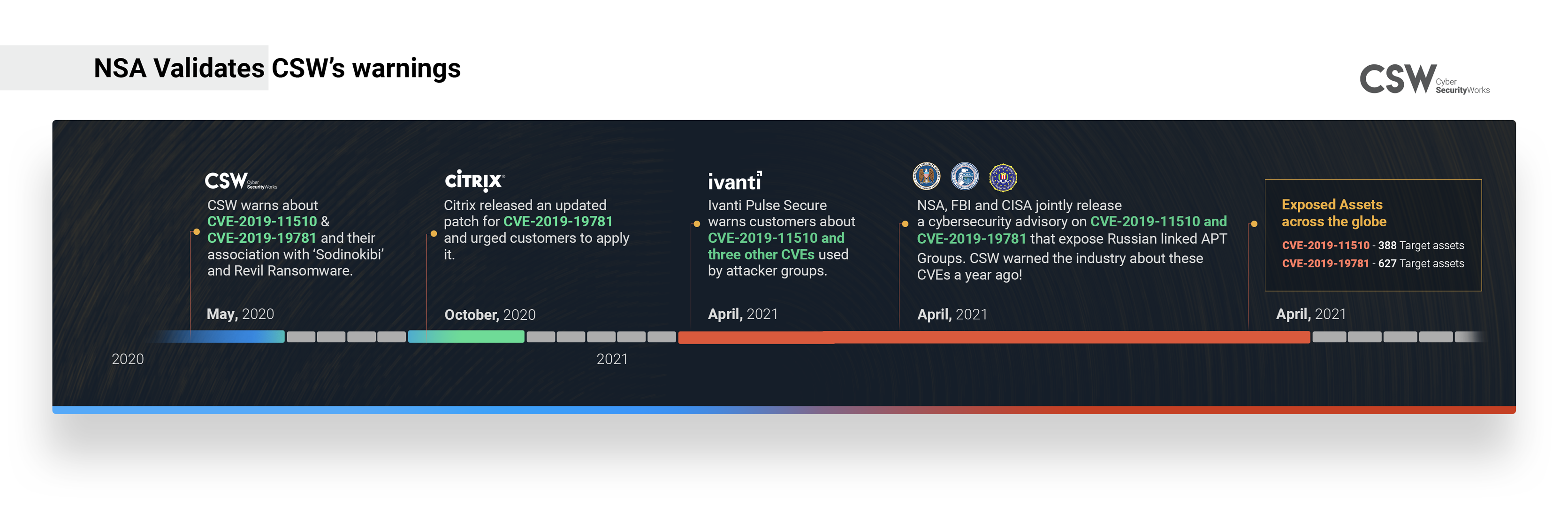
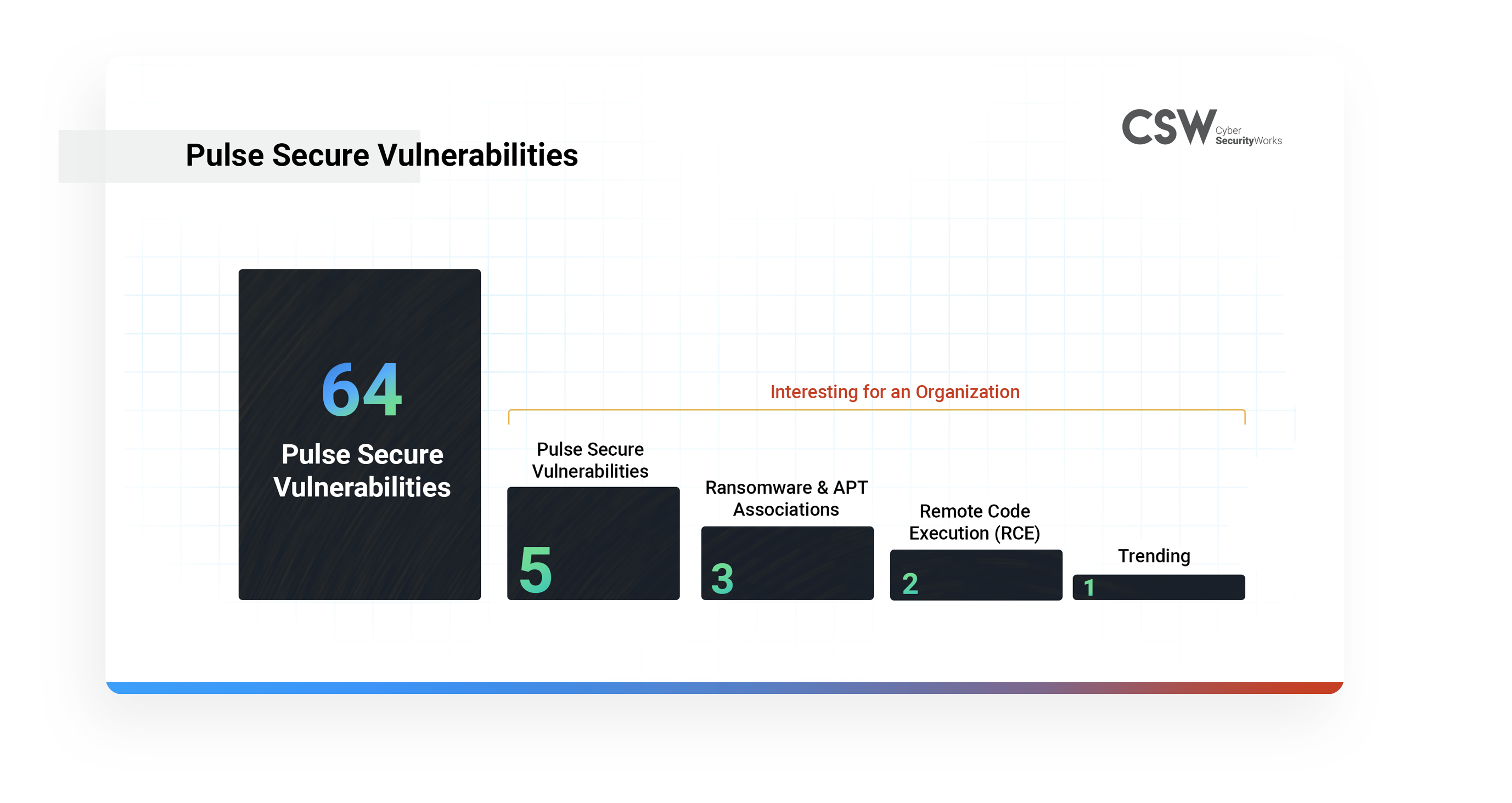
Last year Securin analyzed 44 and 25 vulnerabilities in Pulse Secure and Citrix respectively. We red flagged CVE-2019-11510 and CVE-2019-19781 attack vectors that might be used by attackers to compromise corporate networks.
 Our analysis was validated when these vulnerabilities started trending all through 2020 and in April 2021, CISA, FBI and other Security agencies warned users that a Pulse Secure vulnerability was used by Russian and China-linked attackers to spy on the US Defense Industry.
Our analysis was validated when these vulnerabilities started trending all through 2020 and in April 2021, CISA, FBI and other Security agencies warned users that a Pulse Secure vulnerability was used by Russian and China-linked attackers to spy on the US Defense Industry.
CVE-2019-19781 – Citrix vulnerability has become a pet favorite of attackers and is now associated with 11 ransomware strains and four APT groups (APT41, Fox Kitten, APT29, and Berserk Bear). This RCE exploit allows Directory Traversal that could allow an unauthenticated attacker to perform arbitrary code execution.
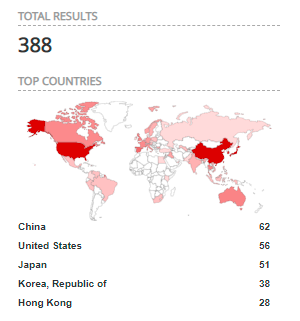
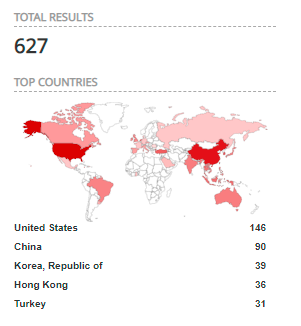
Despite multiple warnings and advisories from security agencies and the vendor, Shodan results show 380 (Pulse Secure) and 627 (Citrix) assets all over the world are vulnerable to these weaknesses (if they are not patched already).
Pulse Secure products vulnerable to CVE-2019-11510
Citrix products vulnerable to CVE-2019-19781
These vulnerabilities have become the favorite attack vectors of malicious agents to compromise and penetrate into networks. Though our warnings have been validated by NSA and other security agencies we wish organizations had prioritized these weaknesses for patching and stayed safe from attackers.
Click here to download our Cyber Risk Reports
Worried about cyber attacks? Are you sure there are no gaps in your security?
We can help shrink your attack surface. Talk to us!
