Cyber Security Works discovered a reflected XSS vulnerability, CVE-2020-24604, in Ignite Realtime Openfire 4.5.1. Openfire (formerly Wildfire). Openfire is a cross-platform real-time collaboration server based on the XMPP protocol. The vulnerability was discovered by CSW Security Researcher on Feb 5, 2020.
Vulnerability Detection
CVE-2020-24604 was detected manually using a Burp Suite tool. The server properties page is vulnerable to reflected cross-site scripting.
Disclosure
The vulnerability was disclosed to Openfire on Feb 5, 2020. The vendor responded and released a patch on March 6, 2020, to mitigate this vulnerability.
Timeline
| Date | Description |
| Feb 4, 2020 | Vulnerability Discovered by CSW Security Researcher. |
| Feb 5, 2020 | Vulnerability Reported to Vendor |
| Feb 6, 2020 | Vendor responded with bug tracker Links |
| Feb 13, 2020 | Follow up with vendor for fix release |
| Mar 1, 2020 | Follow up with Vendor for fix release |
| Mar 6, 2020 | Vendor responded with a released fix |
| Aug 20, 2020 | Request for CVE |
| Aug 24, 2020 | CVE Assigned |
| Sep 1, 2020 | Vendor Updated CVE in the bug tracker and Request for an update in CVE |
| Sep 2, 2020 | CVE Published in NVD |
Vulnerability Analysis
CVE-2020-24604 is a reflected cross-site scripting vulnerability in Openfire Product (Openfire version 4.5.1). The XSS vulnerability allows remote attackers to inject arbitrary web script or HTML through the GET request “searchName”, “searchValue”, “searchDescription”, “searchDefaultValue”,”searchPlugin”, “searchDescription” and “searchDynamic” in server-properties.jsp and security-audit-viewer.jsp
Proof of Concept
Product: Openfire
Vendor: Ignite Realtime
Product version: Version 4.5.1
Privilege: admin
Vulnerable URL: GET request “searchName”,” searchValue”, “searchDescription”, “searchDefaultValue”,“searchPlugin”, “searchDescription” and “searchDynamic” are vulnerable parameters in the following URLs,
http://localhost:9090/server-properties.jsp
http://localhost:9090/security-audit-viewer.jsp
POST request “action” is a vulnerable parameter in this URL
http://localhost:9090/server-properties.jsp
Steps to Reproduce:
Issue: Reflected cross-site scripting (POST Request)
Step 1: Log in to the application (admin) through the URL
Step 2: Navigate to this URL and click on the ‘encrypt’ button
Step 3: Set up a proxy and intercept the request
Step 4: Add the malicious payload ><script>alert(‘VULXSS’) </script> in the parameter ‘action’ and forward the request.
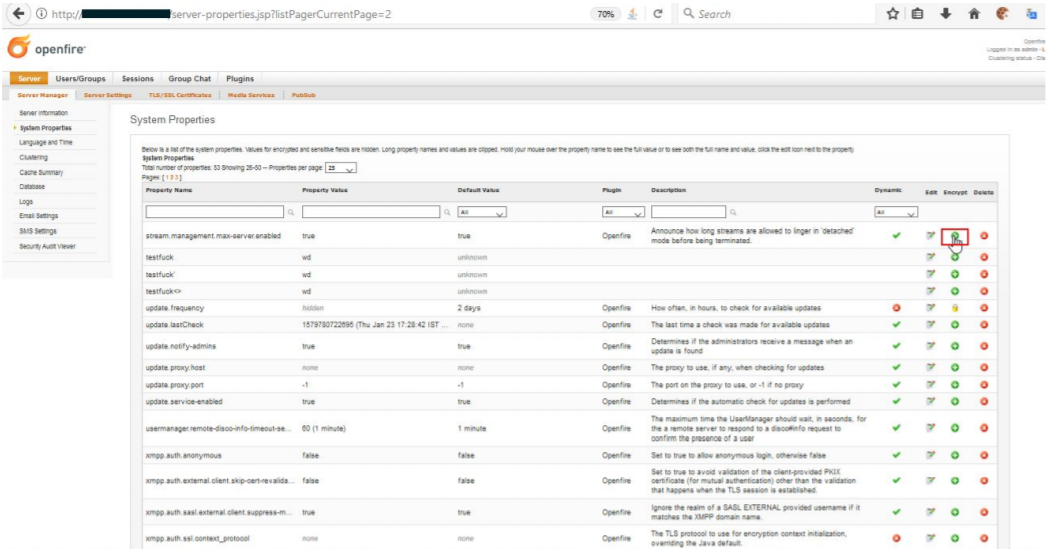
Figure 01: System Properties Page
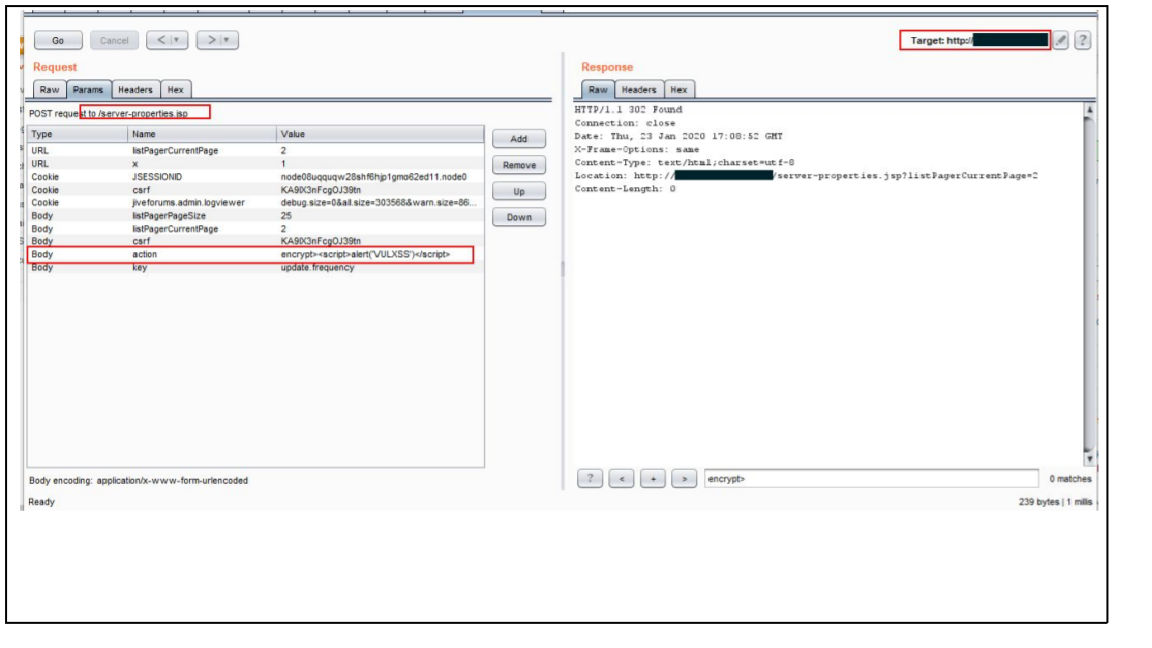
Figure 02: Request to the server with malicious payload><script>alert(‘VULXSS’)</script> in the parameter “action”
.png)
Figure 03: Malicious Javascript payload is executed on the victim’s browser
Mitigation
We recommend the following fixes for this vulnerability
-
Perform context-sensitive encoding of untrusted input before it is echoed back to a browser using an encoding library.
-
Implement input validation for special characters on all the variables reflecting the browser and storing it in the database.
-
Implement client-side validation.
Impact
If this vulnerability is exploited successfully, it may result in
-
The disclosure of information stored in user cookies. Typically, a malicious user will craft a client-side script, which, when parsed by a web browser, performs some activity such as sending all site cookies to a given mail address.
-
It may be possible to run arbitrary code on a victim’s computer when cross-site scripting is combined with other flaws.
Recommendation
Based on the CSW team’s recommendations, Ignite Realtime Openfire executed a validation on their end and released a fix to mitigate this vulnerability.
https://issues.igniterealtime.org/browse/OF-1963
<gdiv></gdiv>
