In our recent report series called ‘Cyber Risk in Working Remotely’ we examined popular VPN applications and their inherent vulnerabilities. This definitive report is an eye-opener for organizations as we analyzed popular applications such as Fortinet, Pulse Secure, Palo Alto, Check Point, SonicWall, OpenVPN, Citrix, Cisco and many others for vulnerabilities.
Key Findings
The report provides a comprehensive study of vulnerabilities that exist in popular VPN solutions
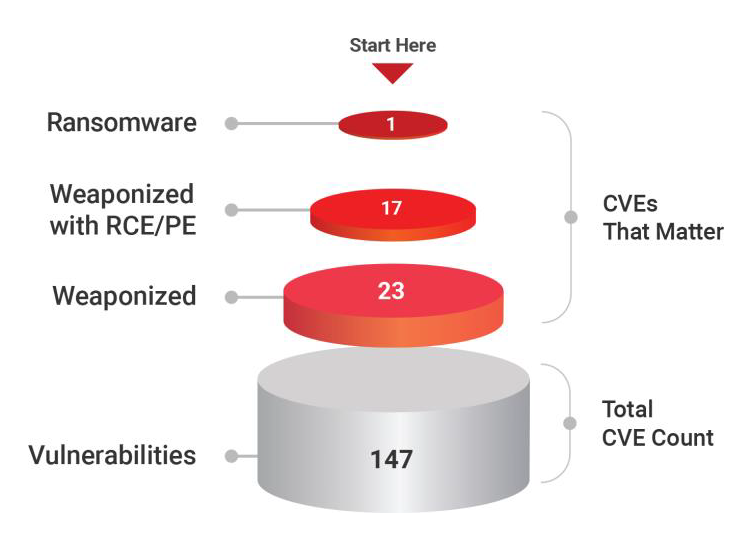
- 23 CVEs are weaponized
- 17 CVEs are associated with RCE & Privilege Execution
- 1 CVE is associated with a Ransomware ‘Sodinokibi’
Vulnerabilities in VPNs
- In the past decade (2010 – 2020) over 147 vulnerabilities (CVE) have been detected across all vendors (that were examined in the report) out of which 23 are weaponized. Out of the weaponized CVE, 1 is associated with Ransomware, 5 with RCE, and 12 have privilege execution.
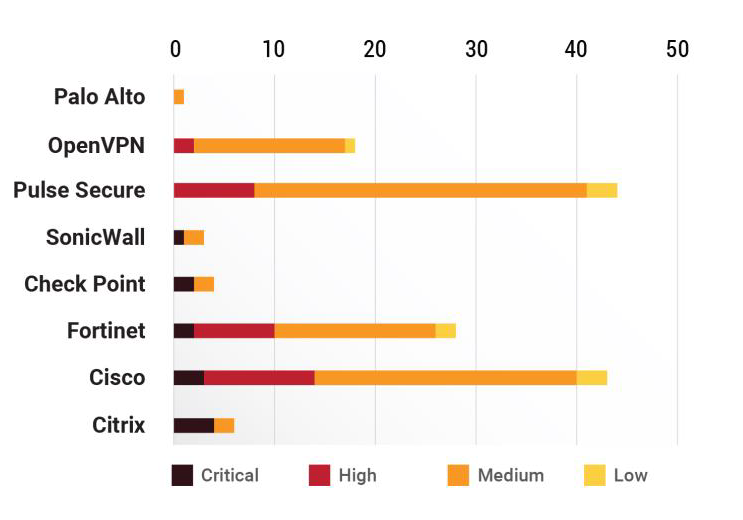
- According to the Common Vulnerability Scoring System (CVSS >=9), there are 12 critical and 29 high vulnerabilities that need to be fixed immediately.
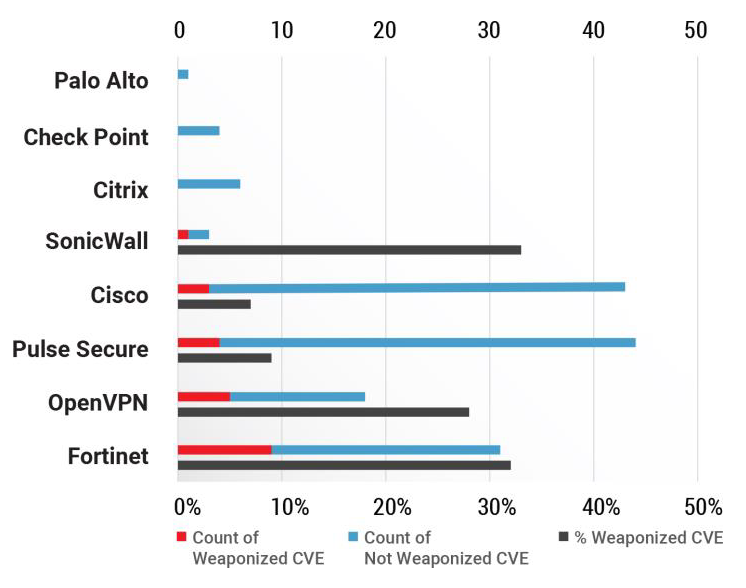
- If you are using VPNs from these vendors, here is a heads-up on their vulnerability count. Pulse Secure has over 44 vulnerabilities in total, of which 4 are already weaponized and 1 is associated with a Ransomware, and 2 have remote code execution capabilities.
- Cisco stands second with 43 vulnerabilities of which 3 have been weaponized. Fortinet stands in the second position with over 28 vulnerabilities in total out of which 9 are already weaponized.
- In terms of priority, Citrix has 4 critical vulnerabilities that need to be fixed, followed by Cisco (3), Fortinet (2), and Check Point (2).
- 2015 and 2017 have been busy years for threat actors (where weaponization of VPN vulnerabilities are concerned) with a count of 7 and 8, respectively.
Count of Vulnerabilities that popular scanners missed
| Nessus | Nexpose | Qualys | |
| Fortinet | 3 | 3 | 1 |
| Cisco | 0 | 3 | 1 |
| Total | 3 | 6 | 2 |
The scanners that ought to detect these vulnerabilities are not doing their job!
- CVE-2019-11510 (the same vulnerability that led to Travelex breach) still exists in Pulse Secure and it allows unauthenticated remote attackers to perform arbitrary file reading.
- CVE-2019-15711 in Fortinet has a PE exploit that allows a user with a low privilege to run system commands under root privilege.
- CVE-2019-11539 which exists in Pulse Secure allows an authenticated attacker to inject and execute commands through the admin web interface.
With popular scan systems not having our back, vigilance is called for. There are 124 vulnerabilities in VPNs that are just waiting to be weaponized.
Threat actors are moving fast and unless you want to pay a huge ransom for your data or watch it being auctioned, vigilance is called for. Don’t be complacent about installing patches for your scan systems and until these CVS are addressed, we would recommend that you use applications that have a smaller number of vulnerabilities.
Download the whitepaper Cyber Risk in VPNs

