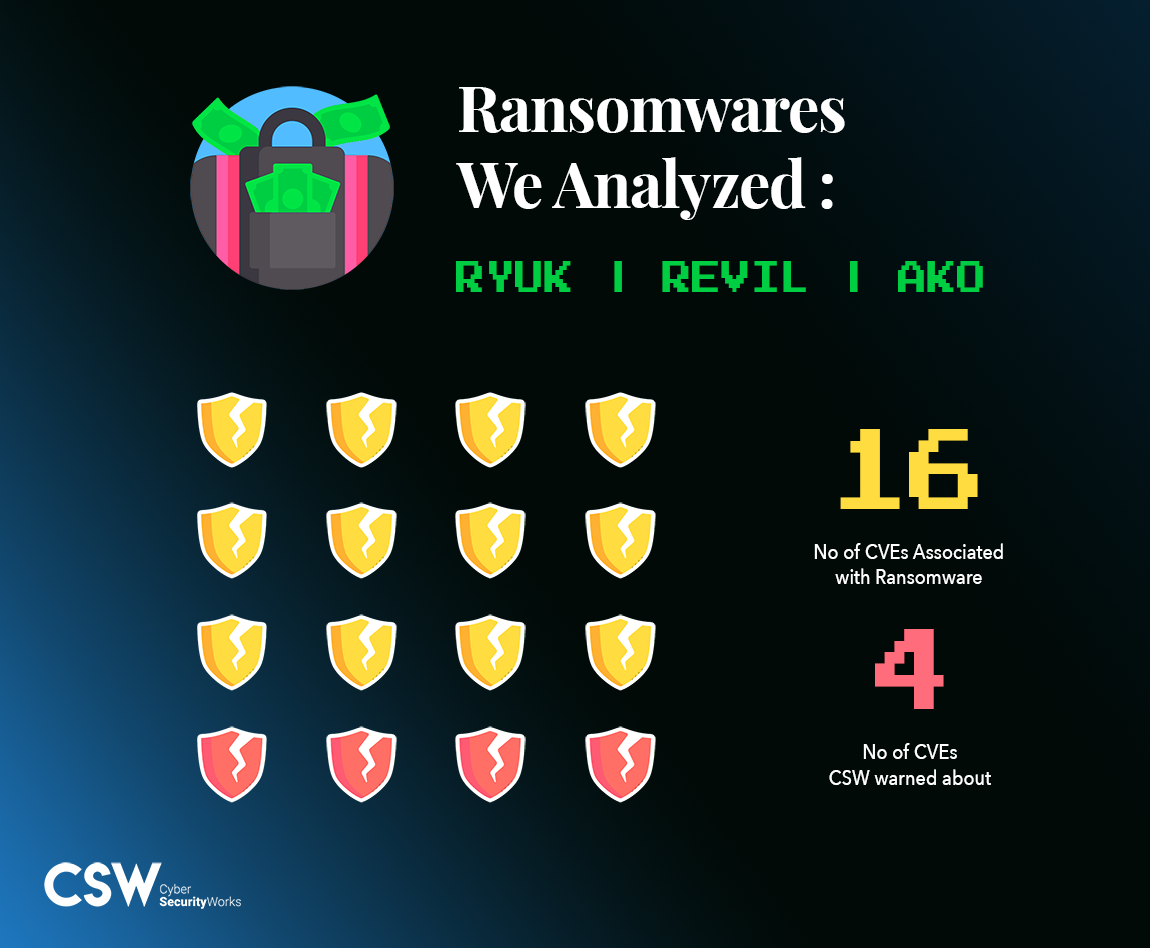
We analyzed three ransomware incidents (Ryuk, Revil & AKO) and found 16 CVEs associated with them. Incidentally, CSW warned about four of these CVEs in our cyber risk series way back in March 2020!
 Hospitals all over the world, stringently follow infection management protocols such as hand washing, sterilization of gowns, face masks & shields, continuous sterilization of equipment and devices to ensure proper protection for patients and doctors alike.
Hospitals all over the world, stringently follow infection management protocols such as hand washing, sterilization of gowns, face masks & shields, continuous sterilization of equipment and devices to ensure proper protection for patients and doctors alike.
If only health care workers, doctors, nurses and hospital employees could extend the same principles to cyber hygiene, we wouldn’t be seeing a spate of Ransomware attacks sweeping all over the world.
Last week, Universal Health Services was attacked by Ryuk Ransomware, leading to a shutdown of the network in over 250 hospitals all over the US.
Investigations revealed that Ryuk ransomware has infected their systems. Ryuk attackers trick users into opening malicious links and they use vulnerable Internet Explorer browsers to exploit and deliver malware.
Ryuk exploits the following vulnerabilities –
- CVE-2013-2618 (Network Weathermap HTML Injection Vulnerability),
- CVE-2017-6884 (Zyxel EMG2926 home router OS Command Injection Vulnerability)
- CVE-2018-8389 (Internet Explorer Remote Code Execution Vulnerability)
- CVE-2018-12808 (Adobe Acrobat and Reader Arbitrary Code Execution Vulnerability)
It’s high time that hospitals and health care centers take cyber hygiene seriously because a ransomware attack is not a pesky technical problem anymore. It can take lives. It already has.
Last month, Düsseldorf University Hospital (Germany) was attacked by Revil through Citrix’s VPN server vulnerability CVE-2019-19781. This ransomware attack led to the death of a patient – making this incident first recorded fatality caused by a ransomware.
Revil exploits vulnerabilities such as –
- CVE-2019-2725 (Oracle Weblogic Vulnerability)
- CVE-2019-19781 (Citrix ADC and Citrix NetScaler Gateway Arbitrary Code Execution)
- CVE-2018-8453 (Window 10 and Windows Server vulnerability)
Earlier last month, the AKO ransomware attack on Children’s Minnesota and Allina Health hospitals led to the exposure of over 160,000 patients’ records through a cloud computing company called Blackbaud that manages the hospital’s database. AKO ransomware uses Citrix vulnerability CVE-2019-19781 to deliver ransomware.
Cyber hygiene and a lack of awareness about cyber security is being exploited by these malicious actors who don’t think twice before attacking a hospital during pandemic times.
Our research has revealed that there are many state-sponsored groups that are using Ryuk and Revil to take down health care centers and hospitals in Europe, UK, US etc.
| Ransomware | CVEs | APT Groups |
|---|---|---|
| Ryuk | CVE-2017-0143 | Calypso |
| CVE-2017-0144 | Shadow Brokers | |
| CVE-2017-0145 | APT3 (Chinese Group) | |
| Revil | CVE-2019-2725 | GOLD SOUTHFIELD threat group |
| CVE-2019-19781 | ||
| CVE-2018-8453 | ||
| AKO | CVE-2019-19781 | APT41 (Chinese Actor) |
We urge hospitals and health centers to patch these CVEs without further delay.
Table 1: Download information about 16 CVEs, known exploits, APT Groups, Ransomware & Patches
These incidents could have been avoided. We warned about five CVEs in our Cyber Risk Series (published in 2020) as potential vulnerabilities that could be exploited by ransomware and sadly our prediction came true.
- CVE-2019-6109 (Cyber Risk in Enterprise Data Storage)
- CVE-2019-6110 (Cyber Risk in Enterprise Data Storage)
- CVE-2018-20685 (Cyber Risk in Enterprise Data Storage)
- CVE-2019-19781 (Cyber Risk in Remote Desktop)
.png)
Cyber Risk Report: An extract from Cyber Risk in Enterprise Data Storage
.png)
Cyber Risk: Cyber Risk in Working Remotely

The way forward
Hospitals need to protect themselves from Ransomware attacks especially now when we need them functioning to help people cope with a pandemic.
- Protect your network against trending ransomware attacks by applying patches and updates.
- Avoid misconfigurations
- Initiate a continuous vulnerability management process.
- Backing up your data is critical.
- Integrating Ransomware detection tools in your infrastructure is essential.
- Frequent pentesting and enhancing your defenses is crucial
Lastly, awareness about cyber security is low among hospital staff another reason why phishing and email scams are so successful. Most hospitals do not have a budget for cyber security and nor do they have dedicated security teams to manage vulnerabilities or educate employees.
Definition
Ransomware: Ransomware is a malicious software (malware) that encrypts computers. Once encrypted, you cannot access your files or see the content. After encrypting, the attacker will demand a ransom from you if wish to get access back to your files. Once the ransom is paid (which can range from thousands or hundreds of dollars/bitcoins), you will recieve instructions about the decryptiion key that will restore your files back to you.
