The massive breach of the SolarWinds Network Management product has compromised as many as 18,000 organizations outside of the US Government entities, security agencies, and defense entities. We took a closer look at the weaknesses that exist in other SolarWinds’ products and found that top scanners miss most of the vulnerabilities.
Our Key Findings
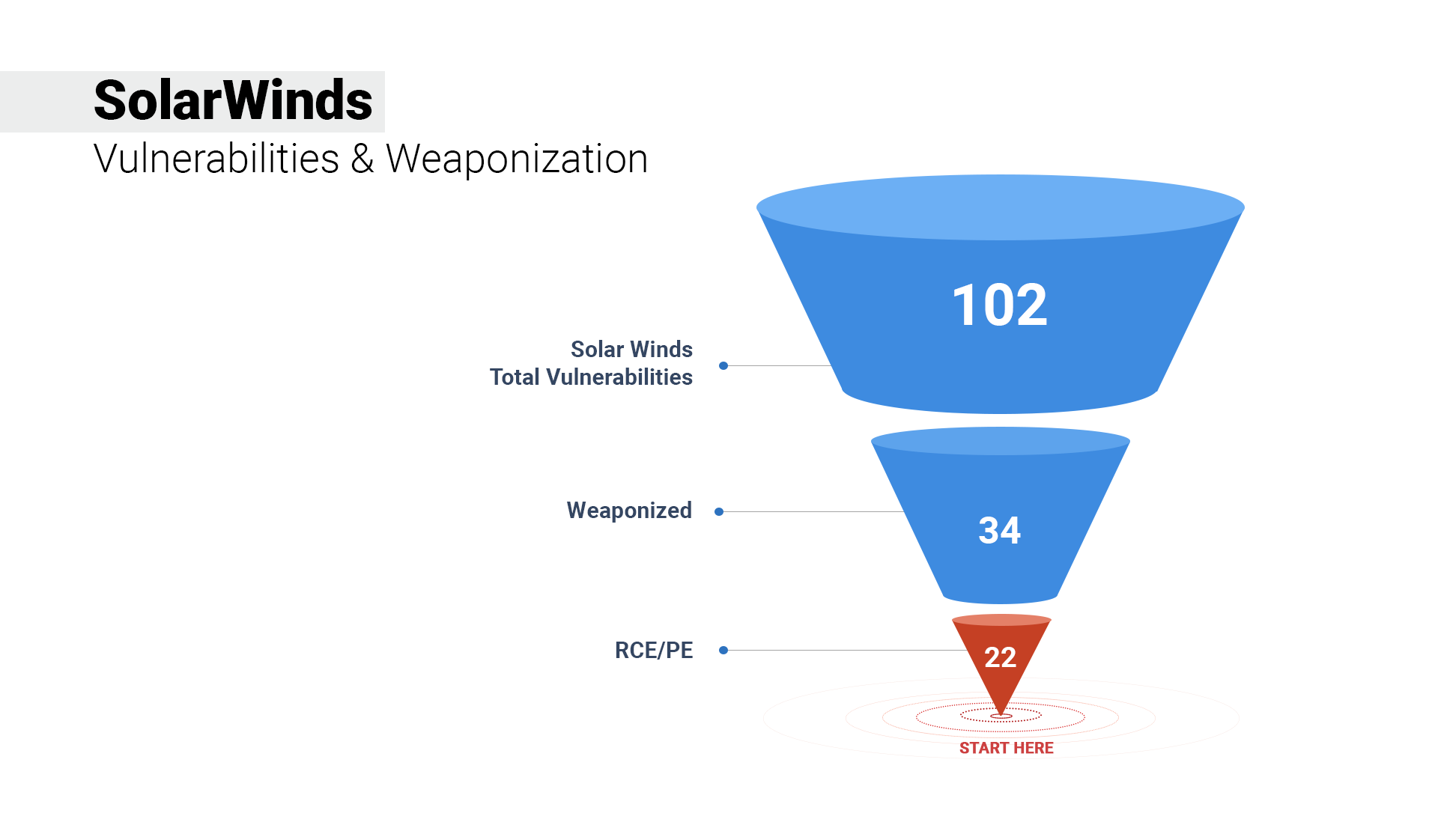
- 102 vulnerabilities exist in SolarWinds products, wherein 34 CVEs are weaponized.
- 30 CVEs are rated critical; 21 are high.
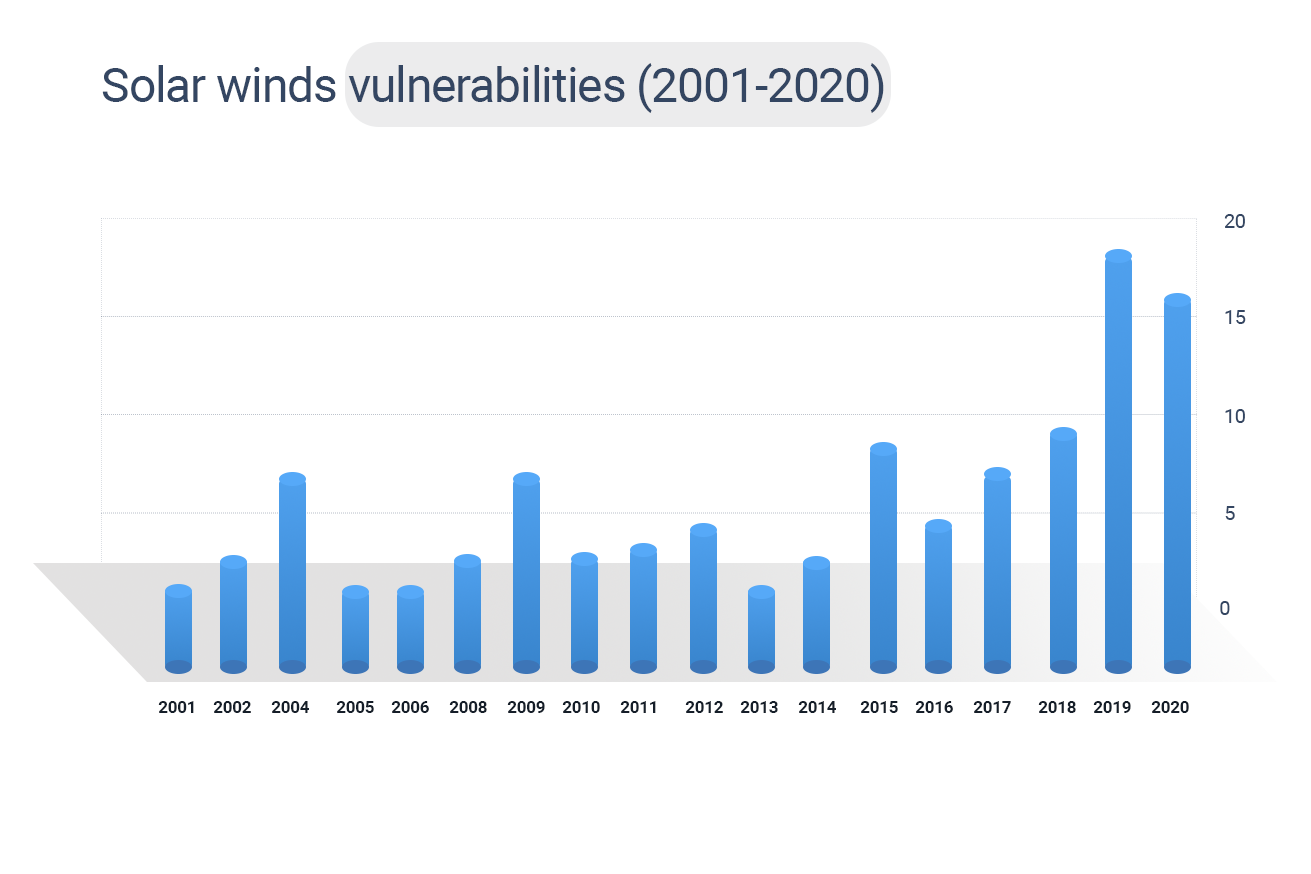
- 85 old vulnerabilities exist in SolarWinds, ranging from 2001 to 2019.
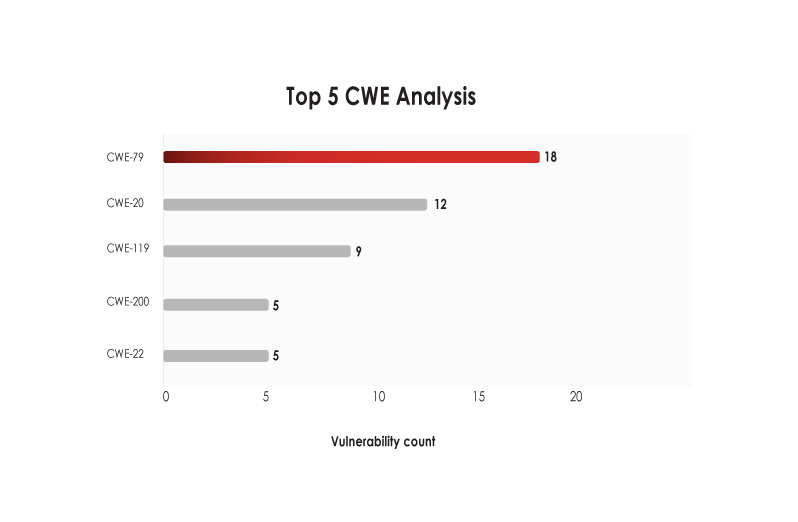
- CWE-79 (Improper Neutralization of Input During Web Page Generation) seems to be the most exploited weakness, with 18 falling in this category.
- The 15 CVEs in the Orion Network Management tool and CVE-2019-9546 are the suspected culprits for this breach.
- SolarWinds Orion Network Management tool is also responsible for the FireEye breach when pentesters’ tools were stolen.
The Attack Surface
When we analyzed the vulnerabilities and weaponization statistics, we observed the following:
- 35% of SolarWinds CVEs are weaponized.
- 22 CVEs have RCE/PE capabilities, making their fixes extremely critical.
- SolarWinds’ products have vulnerabilities existing from 2001 to 2019. The maximum number of vulnerabilities is from 2019, followed by 2020 and 2010.
CWE Analysis
- CWE-79 and CWE-20 are the most exploited weaknesses in SolarWinds’ products.
Old Vulnerabilities
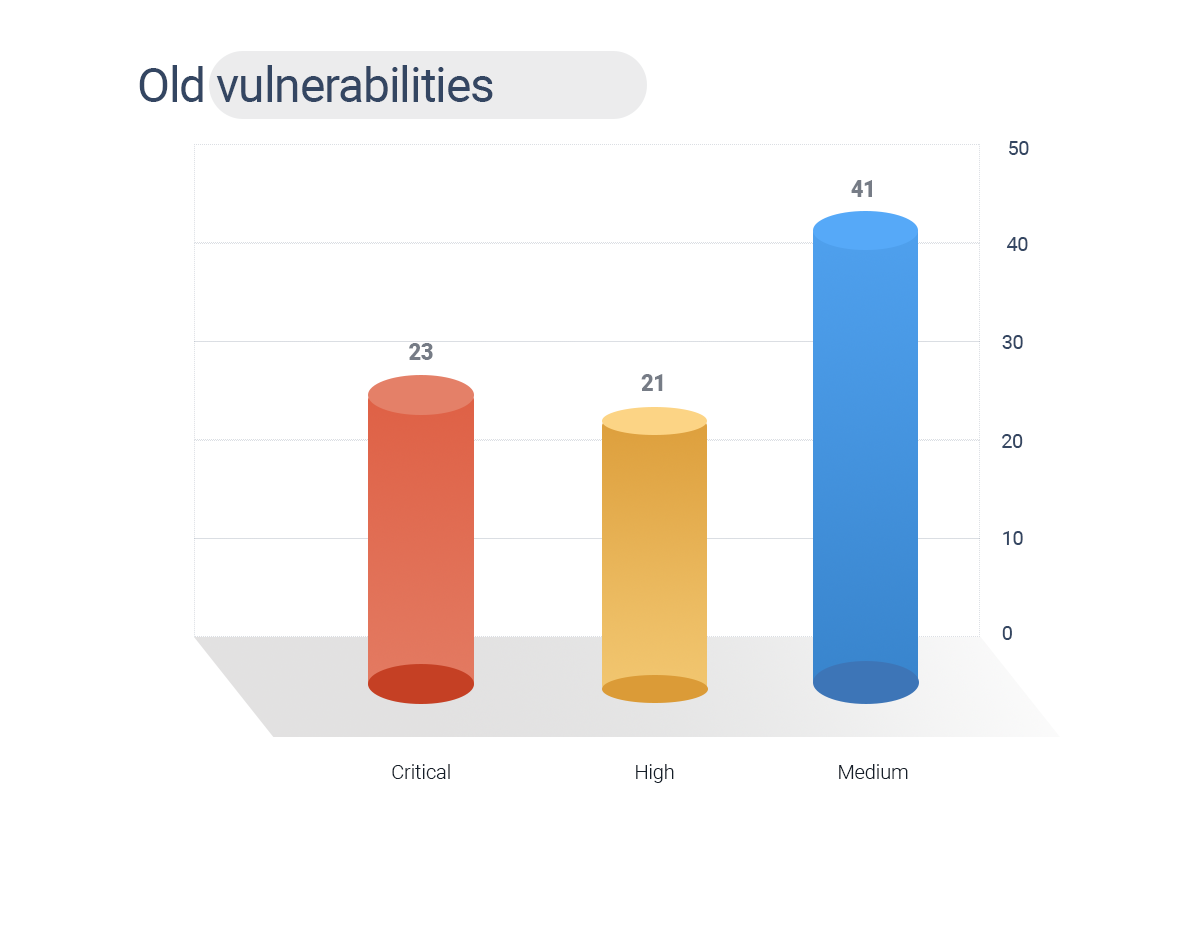
83% of vulnerabilities in SolarWinds are old weaknesses. These vulnerabilities range from 2001 to 2020, presenting two decades of bugs.
- Of these 85 vulnerabilities, 32 are weaponized with known exploits.
- 13 CVEs have RCE and PE capabilities.
- 23 CVEs are rated critical, 21 are high, and 41 are medium.
SolarWinds’ Product Analysis
Next, we analyzed the different types of products that have these vulnerabilities and their broad categories:
- 45 vulnerabilities are associated with file transfer servers specifically used to transfer colossal data, a favorite target of threat actors who can steal and expose sensitive files.
- 24 CVEs were linked to the IT monitoring tool. These types of tools should not be exposed to the internet as they serve as standalone tools for pointing out critical issues.
.png)
SolarWinds Global Exposure Analysis
More than 300,000 customers worldwide, including defense, Fortune 500 companies, government agencies, telecommunication companies, and educational institutions, have been using the SolarWinds Network Monitoring tool.
Country-wise exposure analysis reveals the following details:
- 117 countries use SolarWinds’ products, making this breach extremely critical.
- The US tops the list with a count of 698 internet-facing products; the UK ranks next with 98 products, and India has 56.
Table: Analysis Based on Countries
SolarWinds Scanner Coverage Analysis
We analyzed the data further by comparing the CVEs with some scanners that could detect SolarWinds’ vulnerabilities.
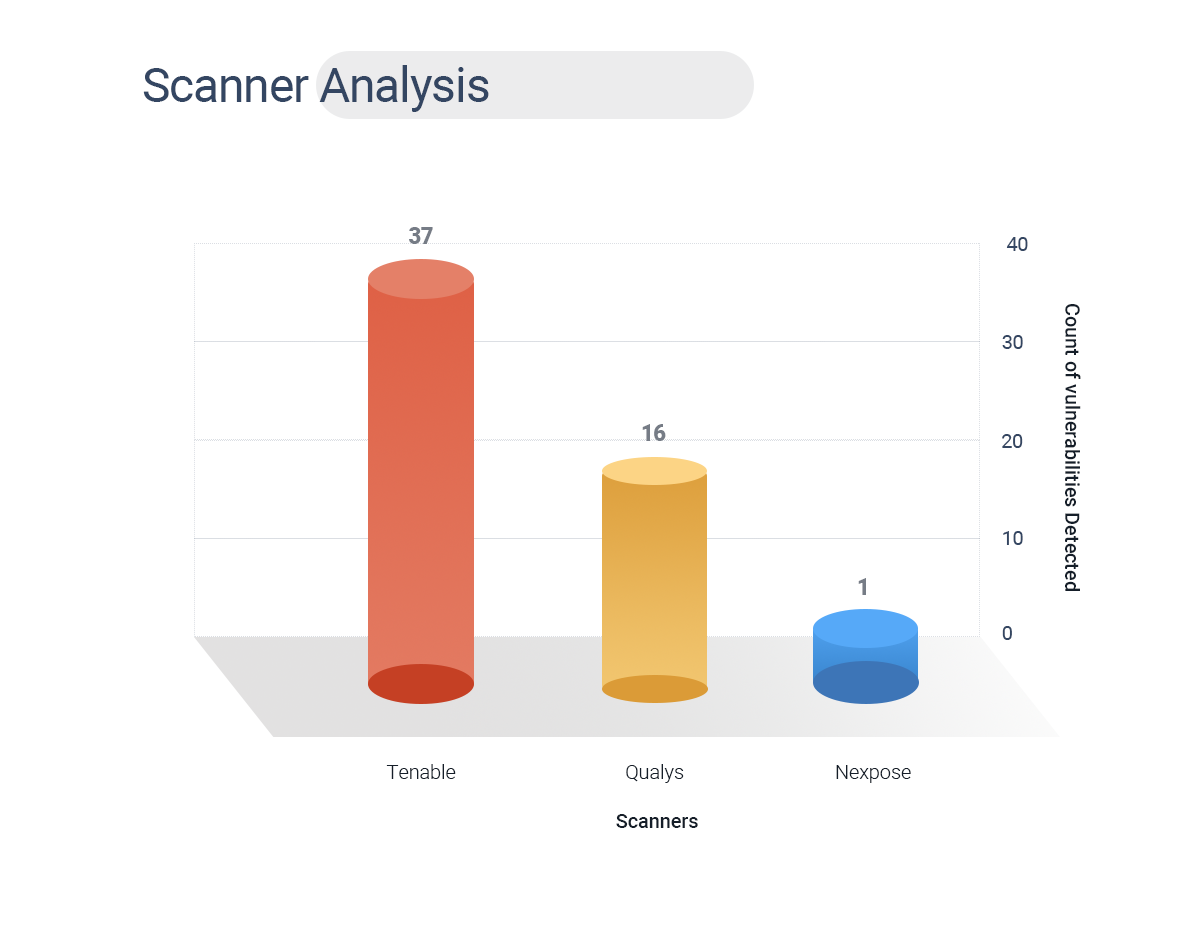
- Out of 102 CVEs, the Tenable scanner detected 37 vulnerabilities.
- Qualys was able to find 15 vulnerabilities.
- Nexpose detected a single vulnerability.
Internet chatter is abuzz with the fact that this might be a nation-state attack, a fact that we concur with. There have been no demands for ransom, and the threat actors have been patiently biding their time since the Spring of 2020 to mount their attacks. While much conversation is floating around about the possible APT groups that could have been involved in this attack, our investigation has not revealed any association with ransomware or APT groups.
What we see today is probably the most serious cyberattack of all times perpetrated by threat actors not motivated by greed. With state secrets compromised, attacks such as these force us to take a step back and see what we can learn from it.
One of the many lessons from this incident would be that organizations should and must seriously invest in vulnerability management and penetration testing and continuously check their attack surface from infrastructure to code.
Related Blogs
SolarWinds Vulnerability Analysis
FireEye’s Stolen Pentesting Tools
